A Manageable Authenticated Encryption Method
A technology of certified encryption and custodian, which is applied in the field of certified encryption of files, which can solve the problems of losing the meaning of digital signature, users cannot choose the custodian by themselves, and cannot satisfy non-repudiation, so as to meet non-repudiation and halve the number of certificates , the effect of reducing the burden
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
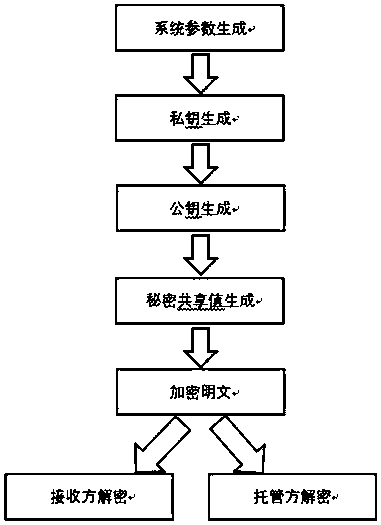
[0019] Attached below figure 1 Further illustrate the technical scheme of the inventive method
[0020] A kind of trustworthy authentication encryption method of the present invention comprises the following steps: system initialization (Setup), private key generation (Key-Gen), encryption algorithm (Encryption), decryption algorithm (Decryption), trusteeship decryption algorithm (Escrow-Decrypt) . Specifically include:
[0021] Step 1: Generate system parameters for encryption and decryption; given a security parameter k, where k is an integer, specify its size according to user security requirements; output two cyclic groups G with order q 1 with G 2 , while generating the group G 1 A generator P of and a bilinear map G 1 ×G 2 →G 2 , where q is a prime number. Choose a hash function H whose output is at least 160 bits. The plaintext space is M={0,1} n , the ciphertext space is Among them, n integer system public parameters are 1 ,G 2 ,n,P,H>;
[0022] Step 2:...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com