Data security management method of power business terminal
A technology for power business and data security, applied in the field of information statistics security, can solve the problems of lack of necessary identification of data credibility, failure to consider information security issues, lack of use of mobile handheld devices, etc., to improve information collection, ensure security, and ensure confidentiality. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
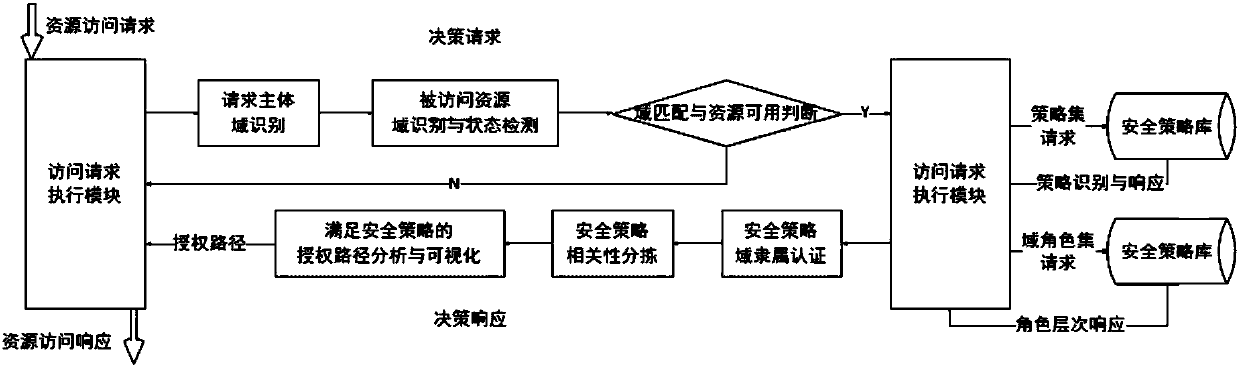
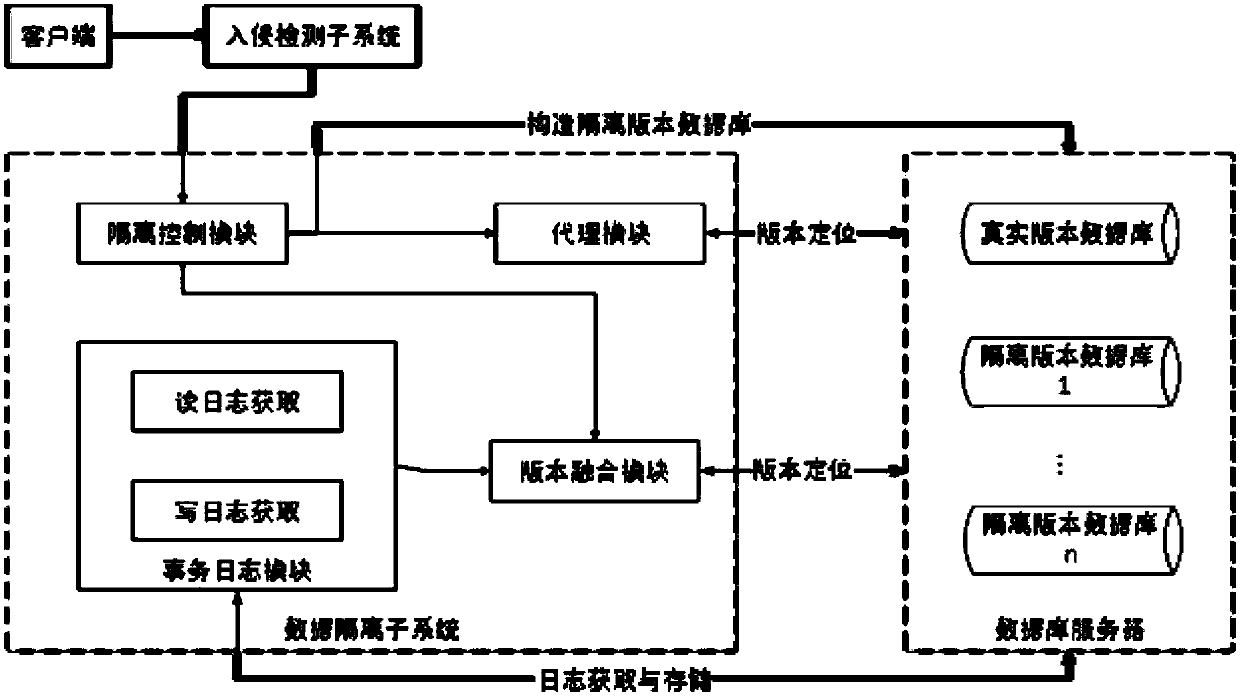
[0026] A data security management method for a power service terminal, comprising constructing a multi-level security model of a power service terminal based on a security chip, the multi-level security model of a power service terminal includes a trusted software stack functional architecture, and the trusted software stack functional architecture includes the following part:
[0027](1) Trusted access control: Since service providers cannot be trusted to implement user-defined access control policies, in data security technology, researchers are concerned with how to implement access control of data objects through non-traditional access control methods; among them, The most concerned is the access control based on cryptographic methods; including the method of implementing access control based on hierarchical key generation and distribution strategies; using attribute-based encryption algorithms, such as the attribute-based encryption scheme KP-ABE of key rules or ciphertext...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com