Bluetooth financial card and working method thereof
A financial card and Bluetooth technology, applied in the field of information security, can solve problems such as inconvenient operation, easy to forget verification information, and low work efficiency, and achieve the effect of overcoming inconvenient operation, convenient and safe transactions, and convenient transaction operations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
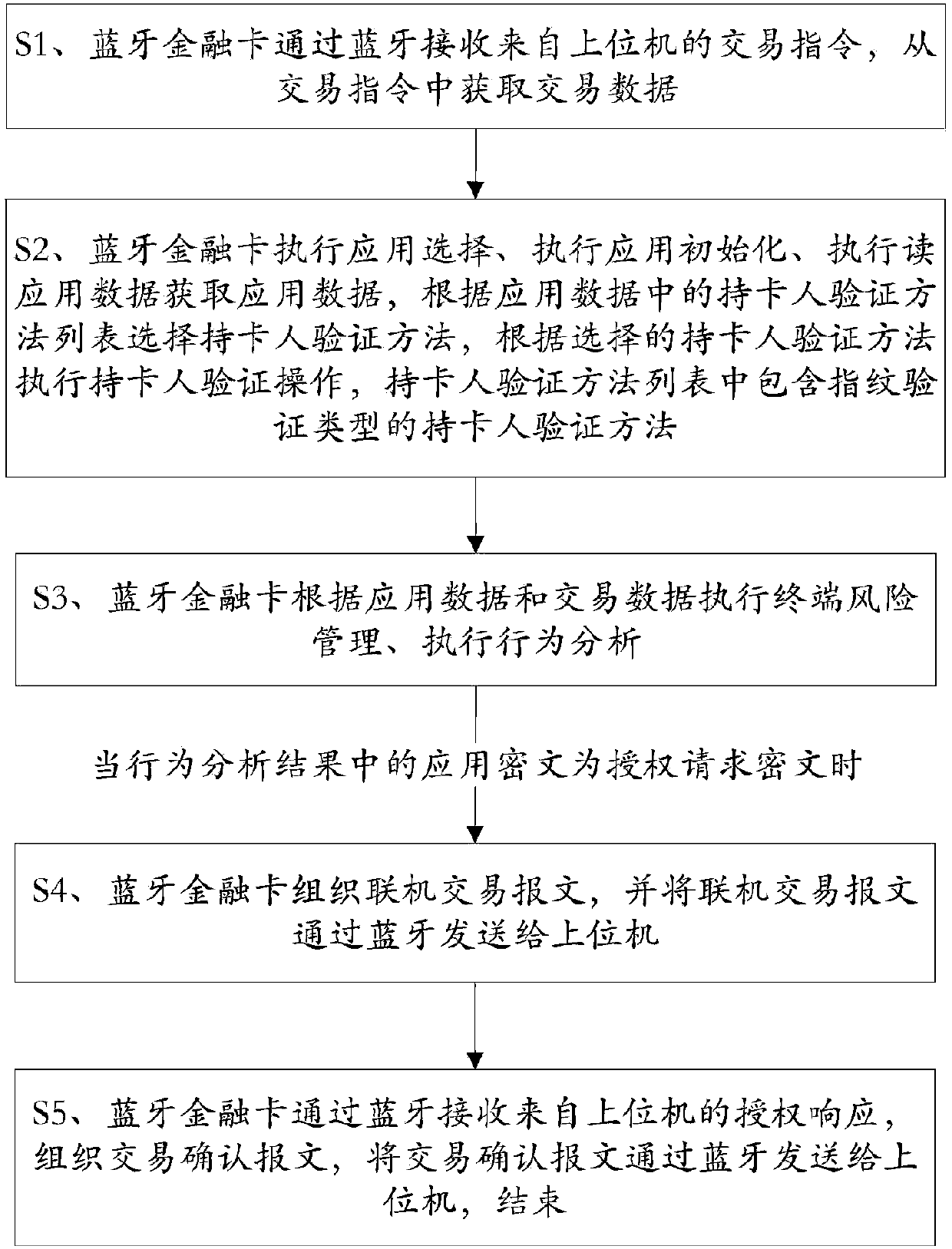
[0037] This embodiment provides a working method of a bluetooth financial card, such as figure 1 As shown, specifically include:
[0038] Step S1: The Bluetooth financial card receives transaction instructions from the host computer through Bluetooth, and obtains transaction data from the transaction instructions;
[0039] Step S2: Bluetooth financial card executes application selection, executes application initialization, executes reading application data to obtain application data, selects the cardholder verification method according to the cardholder verification method list in the application data, and executes the cardholder verification method according to the selected cardholder verification method. Cardholder verification operation, the cardholder verification method list includes the cardholder verification method of fingerprint verification type;
[0040] Step S3: The Bluetooth financial card performs terminal risk management and behavior analysis according to the ...
Embodiment 2
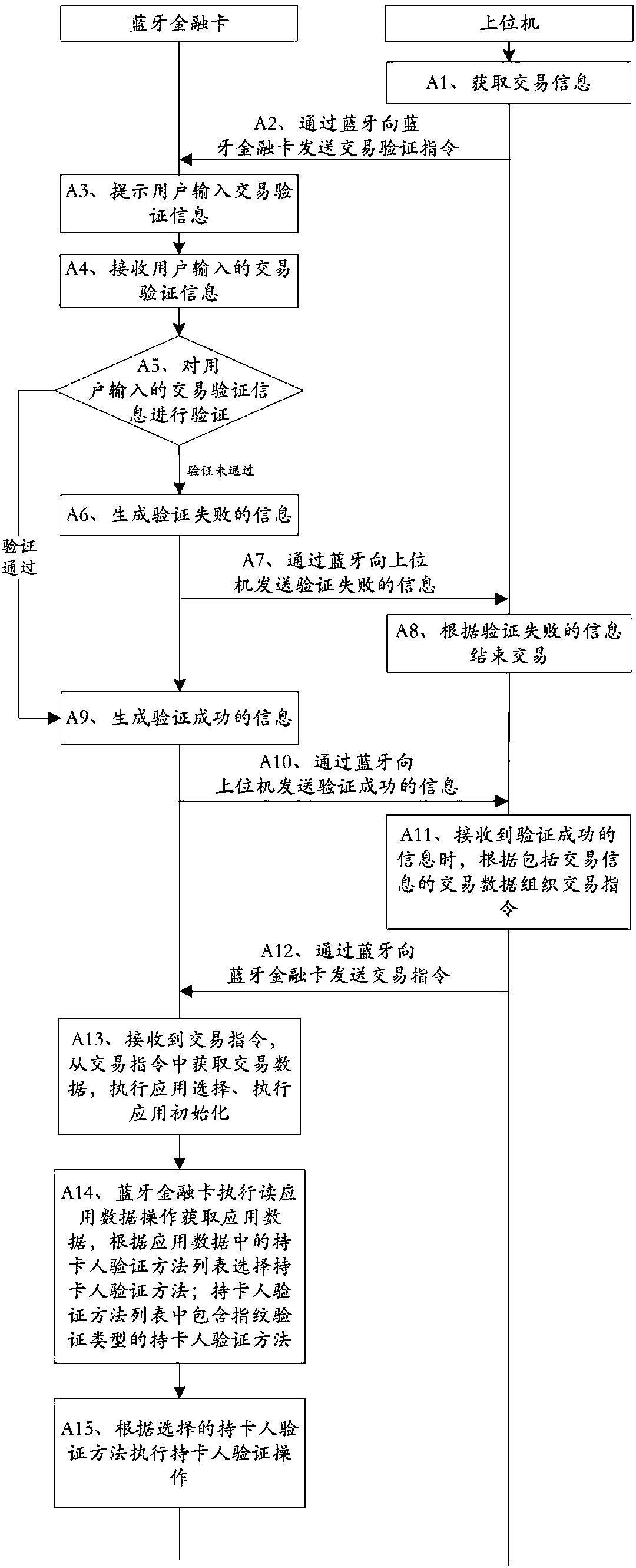
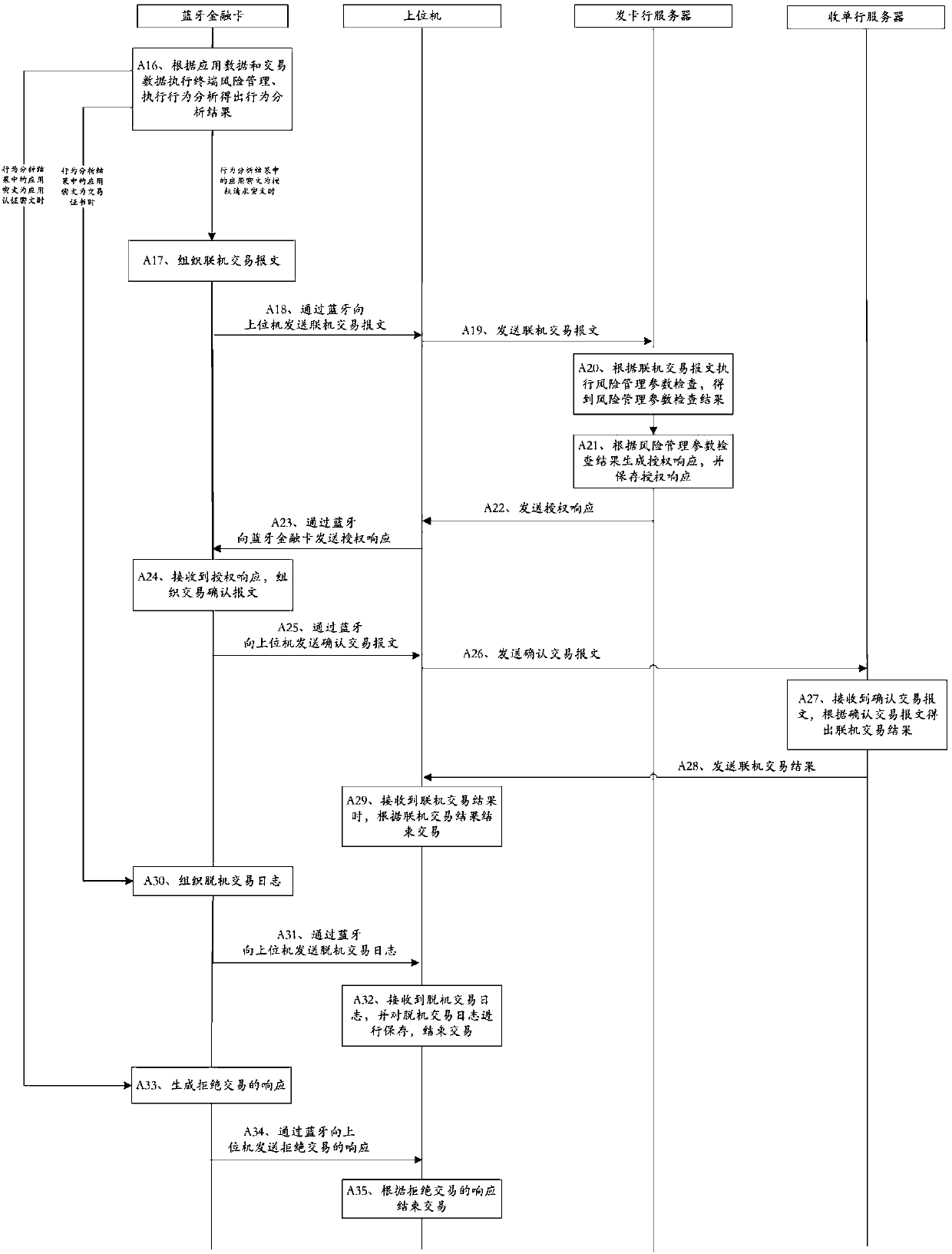
[0103] This embodiment provides a working method of a system including a Bluetooth financial card, a host computer, a card issuing bank server and an acquiring bank server, such as Figure 2-Figure 3 shown, including:
[0104] Step A1: The host computer obtains transaction information.
[0105] Specifically, the transaction information includes the transaction amount.
[0106] Specifically, when the host computer scans the barcode on the product, the host computer obtains the transaction amount information; or, when the user enters the transaction amount information on the host computer and clicks the confirmation button of the host computer to confirm the submission, the host computer obtains the transaction amount information.
[0107] Preferably, after the host computer obtains the transaction amount information, the method further includes: the host computer displays the transaction amount.
[0108] Step A2: The host computer sends a transaction verification instruction ...
Embodiment 3
[0244] This embodiment provides a bluetooth financial card, such as Figure 4 shown, including:
[0245] The receiving module 401 is used to receive transaction instructions from the host computer via bluetooth;
[0246] An acquisition module 402, configured to acquire transaction data from the transaction instruction received by the receiving module 401;
[0247] The first execution module 403 is configured to execute application selection, application initialization, and reading application data to obtain application data after the acquisition module 402 acquires the transaction data;
[0248] The selection module 404 is used to select the cardholder verification method according to the cardholder verification method list in the application data obtained by the first execution module 403; the cardholder verification method list includes the cardholder verification method of the fingerprint verification type;
[0249] The cardholder verification module 405 is used to perfor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com