Hardware Trojan detection and discrimination method based on support vector machine
A hardware Trojan detection and support vector machine technology, applied in the direction of internal/peripheral computer component protection, etc., can solve the problems of destroying the original circuit function of the chip, the original circuit cannot work normally, leaking the user's private information, etc., to achieve good detection and low cost , to solve the effect of small samples
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] Embodiments of the present invention are described in further detail below in conjunction with the accompanying drawings:
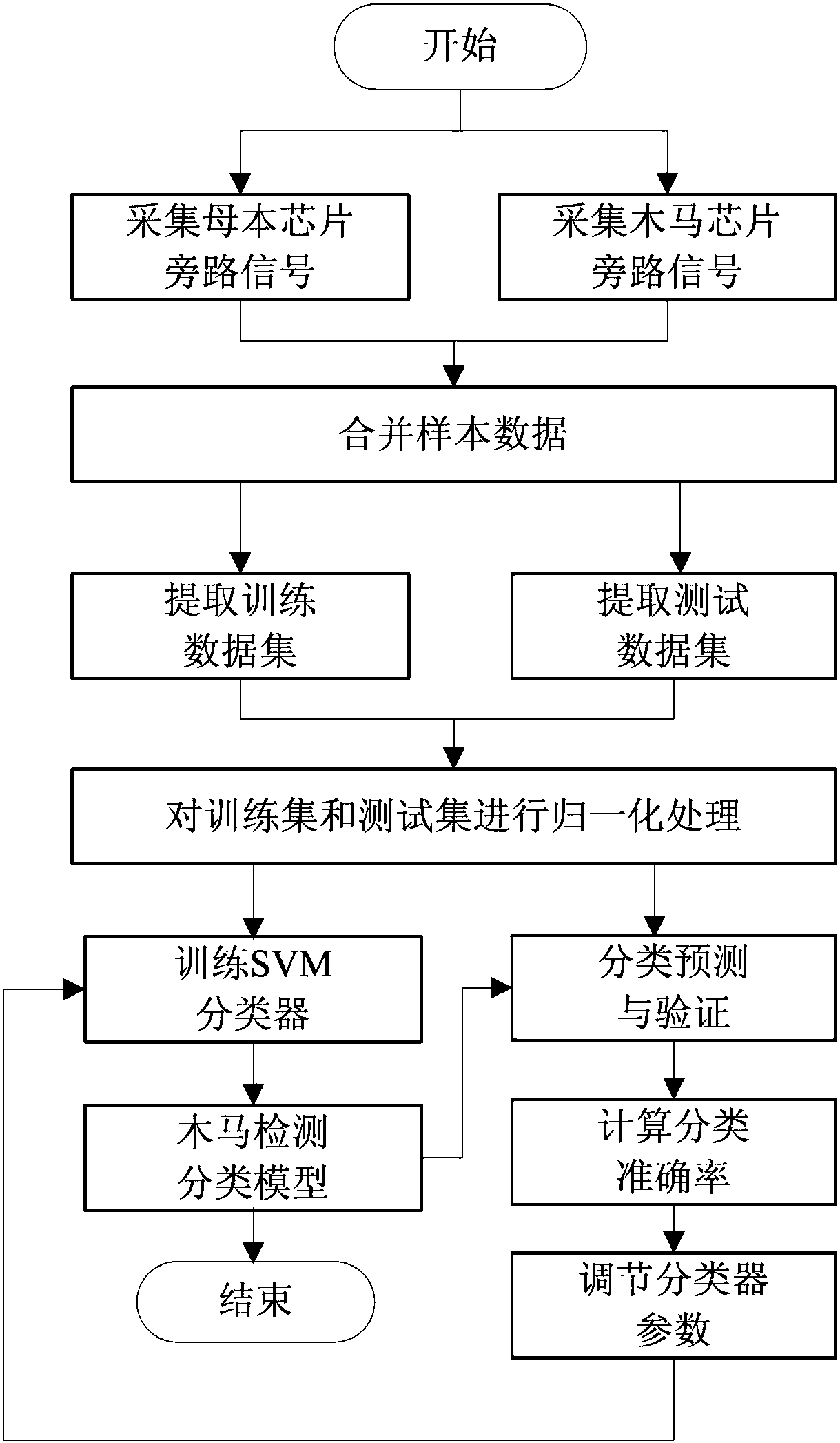
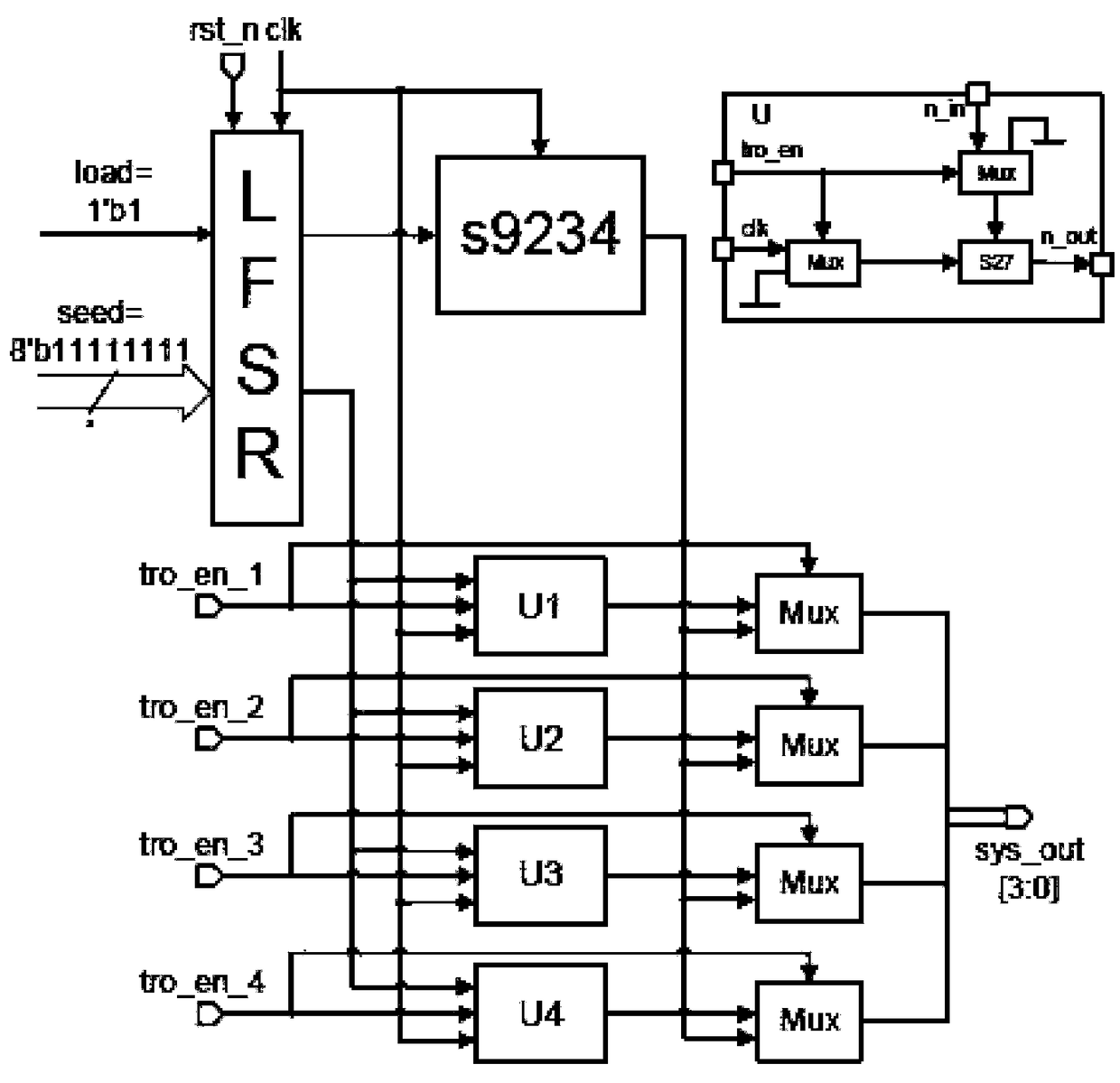
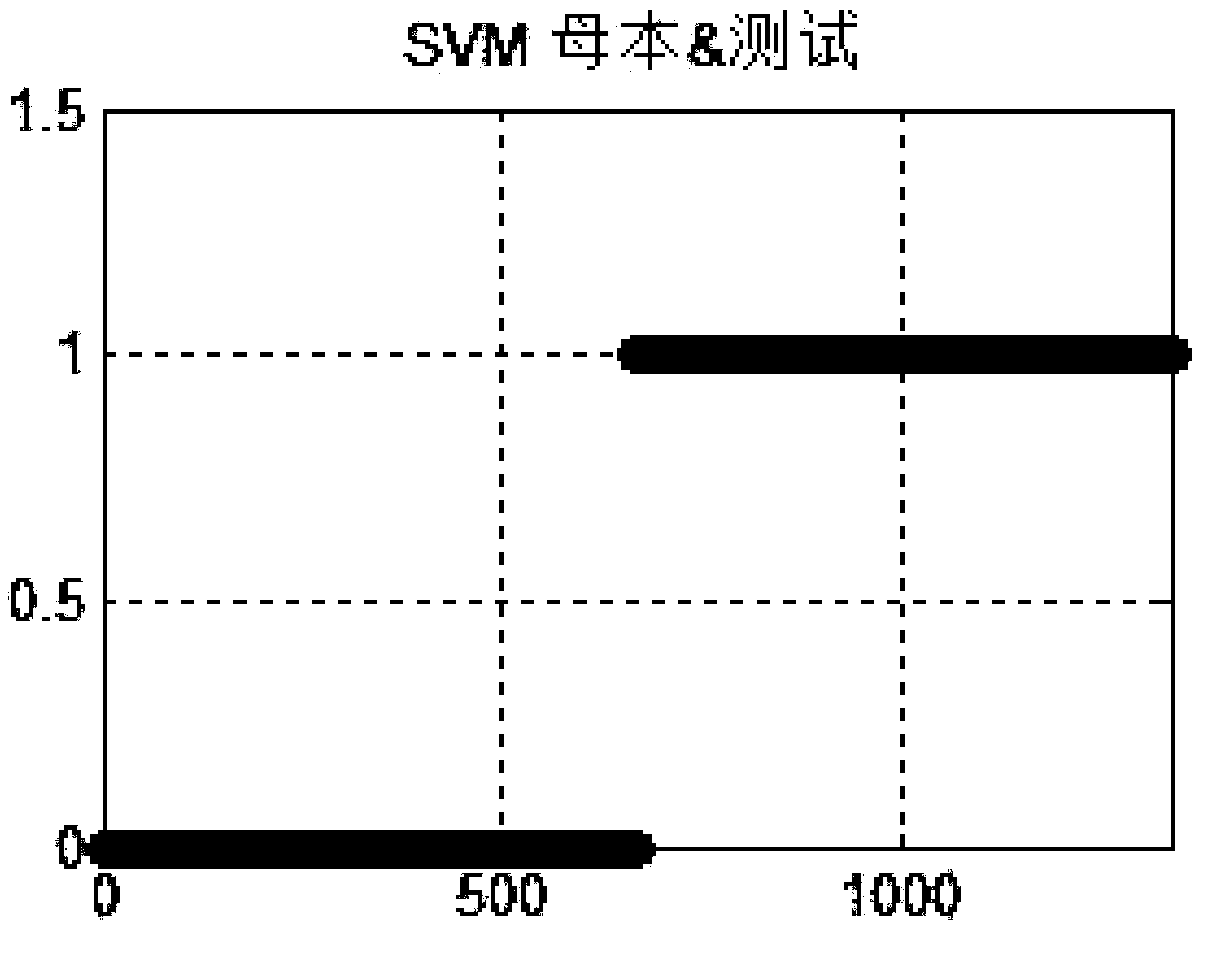
[0026] A hardware Trojan detection method based on support vector machine. The side channel current signal of the chip circuit is used as the original signal. After normalized data preprocessing, the sample library is divided into a training set and a verification set. The training set is used to train SVM classification The hardware Trojan classification and detection model is generated by the device, and the test set is used to verify the classification prediction accuracy of the model. When the accuracy is not ideal, the K-CV cross-validation method can be used to adjust the training parameters and retrain the SVM classifier to generate a new classification and detection model. , and then verify the accuracy of the classification prediction, and so on, and finally obtain a satisfactory hardware Trojan classification and detection model. Input th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com