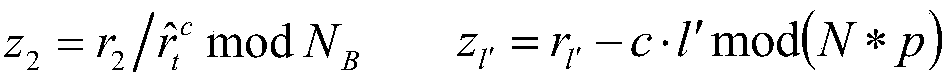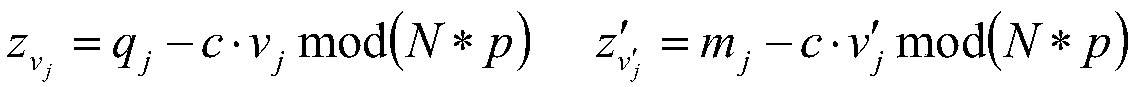Zero knowledge proving method suitable for protecting privacy of block chain, and medium
A zero-knowledge proof, privacy protection technology, applied in user identity/authority verification, payment system, transmission system, etc., can solve problems such as large computing resources and time, inadequate risk assessment, and single usage scenarios
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
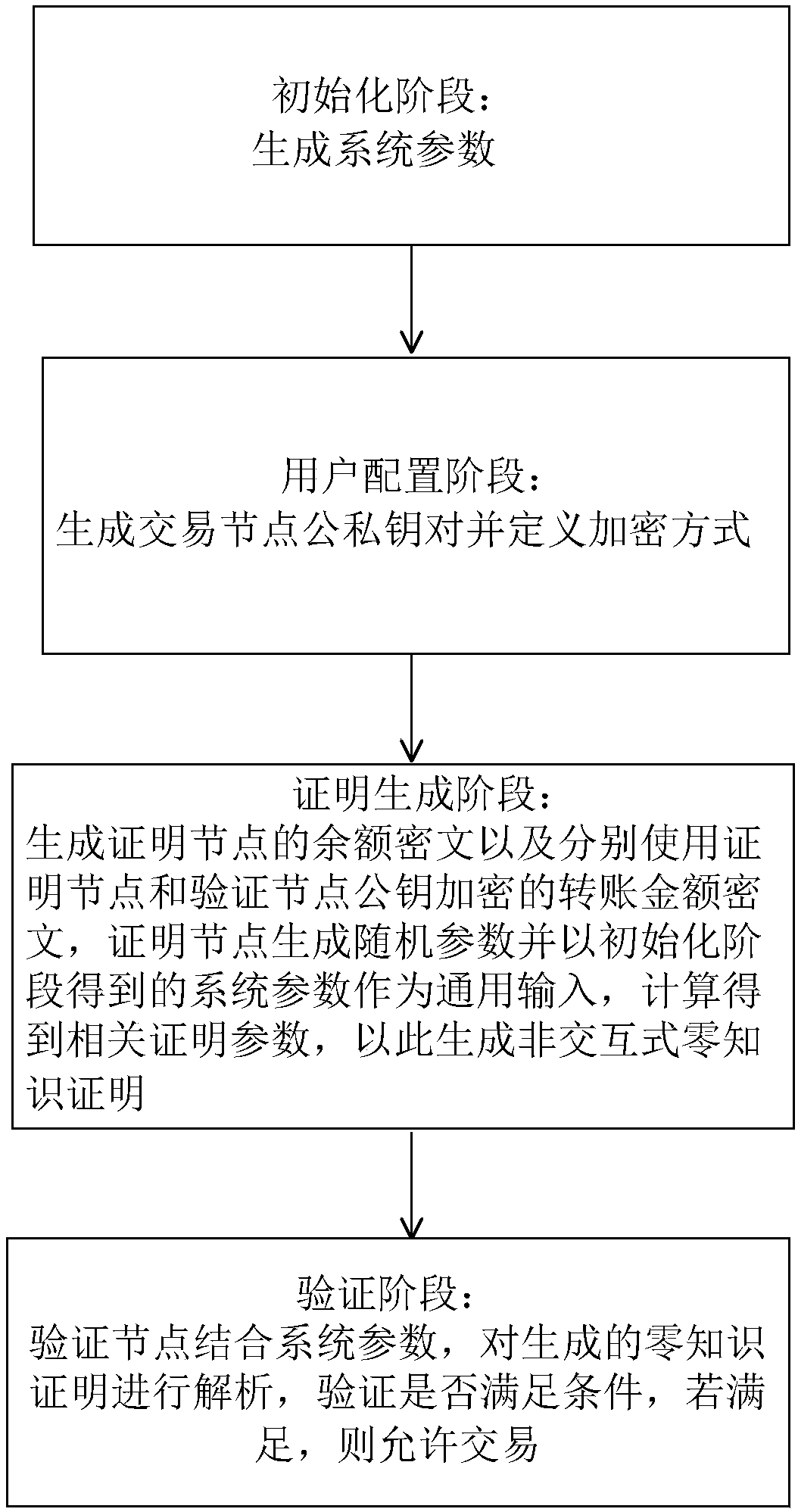
[0172] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments. Note that the aspects described below in conjunction with the drawings and specific embodiments are only exemplary, and should not be construed as limiting the protection scope of the present invention.
[0173] In the solution of the present invention, an additive homomorphic encryption algorithm is used to encrypt private data in the block chain, and a non-interactive zero-knowledge proof is generated during the transaction process to prove the validity of the transaction.
[0174] For the sake of simplicity, the embodiments mentioned below only consider two parties, Users A and B, in the smart contract. Suppose the plaintext space is [0,2 β ], where β=ε·γ (if β≠ε·γ, the scope can be appropriately enlarged to make β=ε·γ established). The implementation steps of the (non-interactive) zero-knowledge proof method suitable for blockchain privac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com