A hardware architecture and application context integrity measurement method based on hardware security isolation execution environment
A technology of integrity measurement and application context, applied in the protection of internal/peripheral computer components, electrical digital data processing, instruments, etc., can solve problems such as large software overhead, large efficiency loss, large attack surface, etc., to achieve accurate acquisition, reduce Additional system overhead, the effect of ensuring metric completeness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
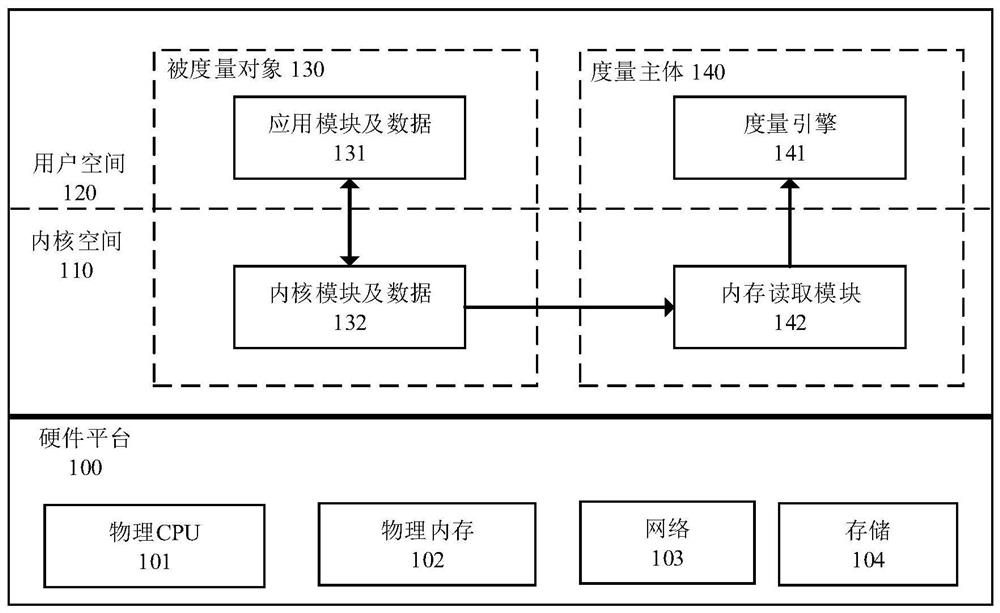
[0067]The hardware security isolation execution environment includes security isolation hardware 400, security domain 420 and common domain 410 divided based on security isolation hardware, security domain code can access common domain storage and computing resources, common domain code cannot access security domain storage and computing resources; The application context includes a resource request process / application 431, an interest-related process / application 433, and kernel key resources 442, which mainly include a system call table 443, an interrupt description table 444, kernel code and static data 445, and kernel data structure metadata 446 , the global descriptor table 447, etc., the resource request process / application 431 initiates the measurement, the interest-related process / application 433 is generated by the system security policy 464, the kernel code and static data, and the metadata of the kernel data structure are extracted from the kernel image and compilation...
Embodiment 2
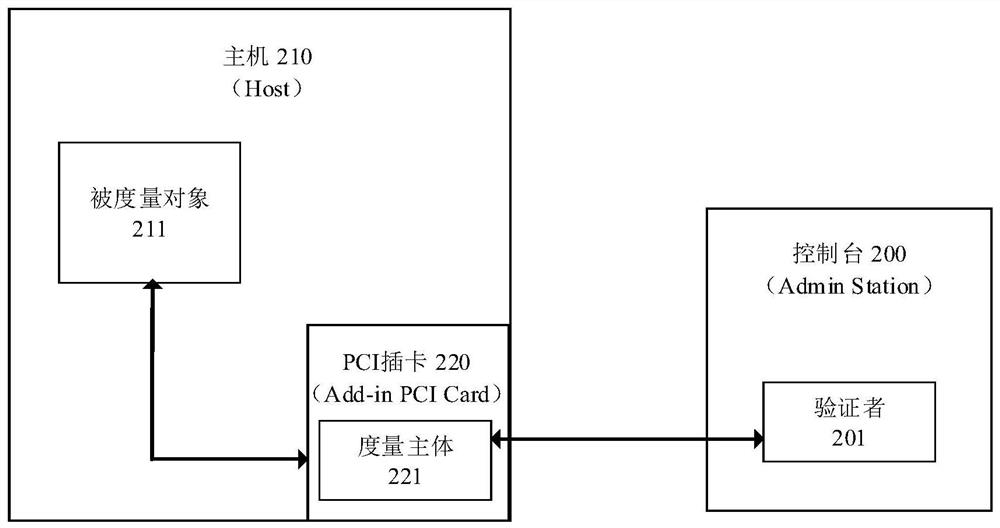
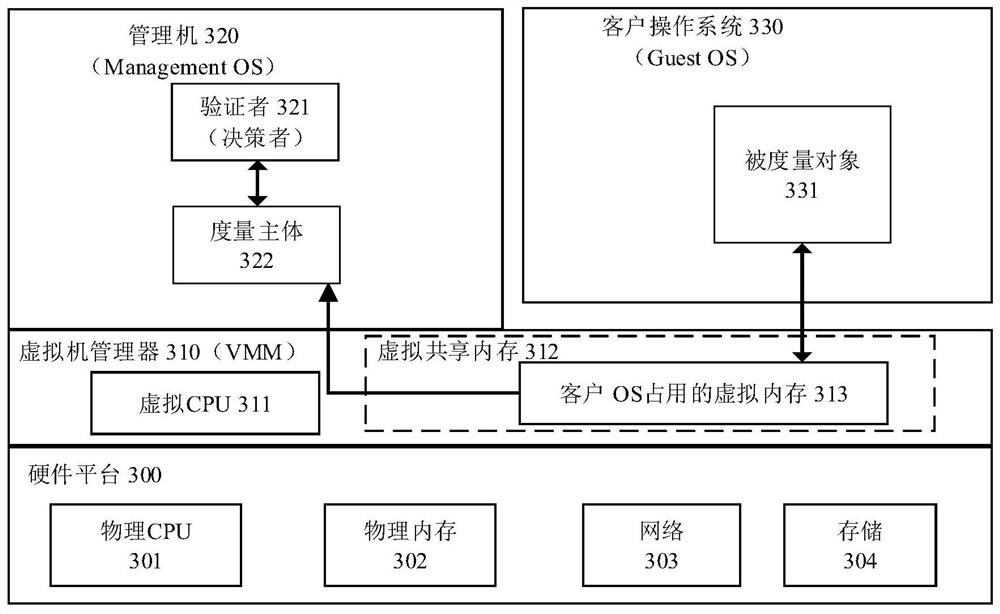
[0078] (1) Execution environment based on hardware security isolation: Figure 4 As shown, based on Trusted Execution Environment (TEE) technology, such as the TrustZone architecture, security extension is performed, including security isolation hardware 400 , security manager 461 , security service driver layer 441 and security service interface layer 462 . The security isolation hardware 400 provides a configurable hardware isolation environment; the security manager 461 can configure the security isolation hardware 400 to work in the normal domain 410 or the security domain 420; the security service driver layer 441 is located in the kernel space 440 of the normal domain 410 Provide security services for the user space 430, such as the measurement engine client 435 accessing the security isolation hardware 400 through the security service driver layer 441; the security service interface layer 462 is located in the kernel space 460 of the security domain 420, and provides sec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com