Behavior tracing detecting method facing internal threats in IaaS cloud environment
A detection method and cloud environment technology, applied in the field of cloud computing security, can solve problems such as difficult to judge legitimate data access requests, unable to identify unknown threats, and unable to trace data access behaviors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
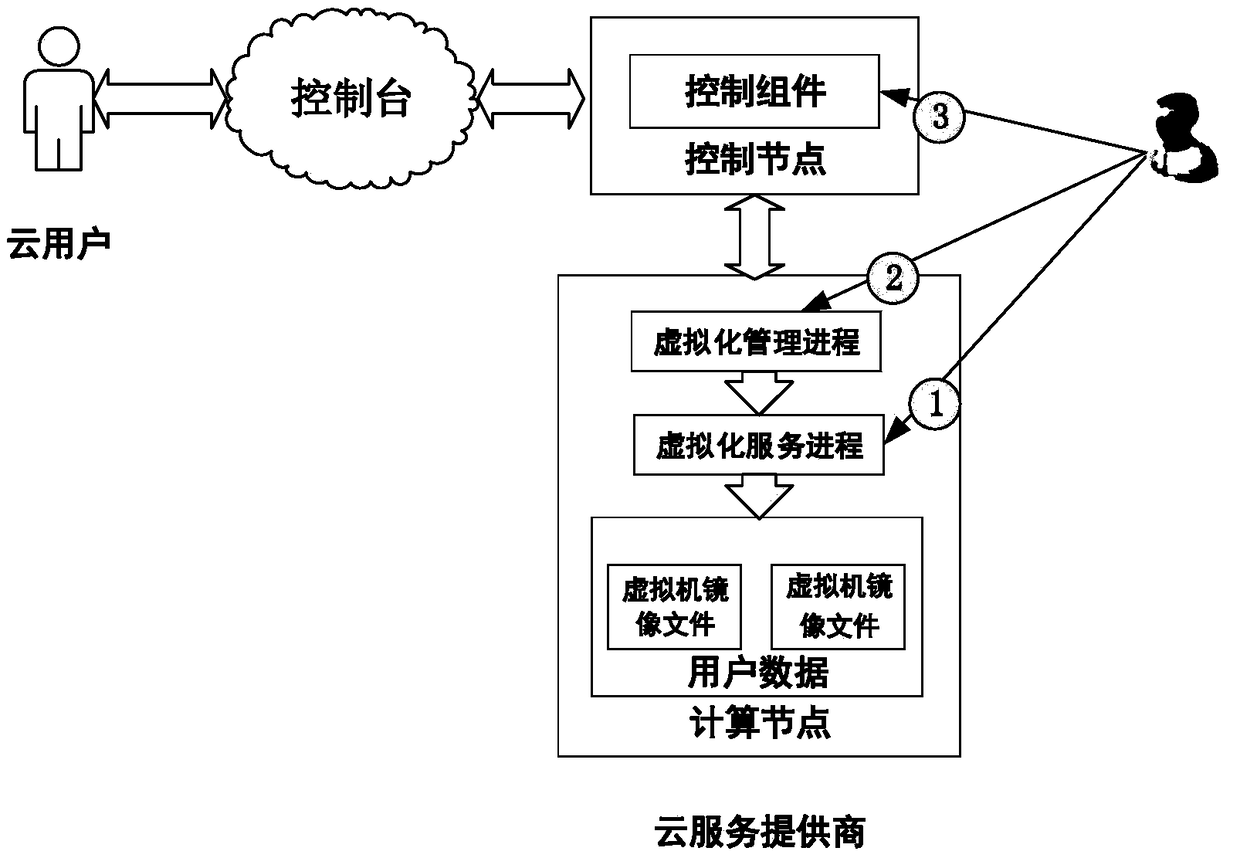
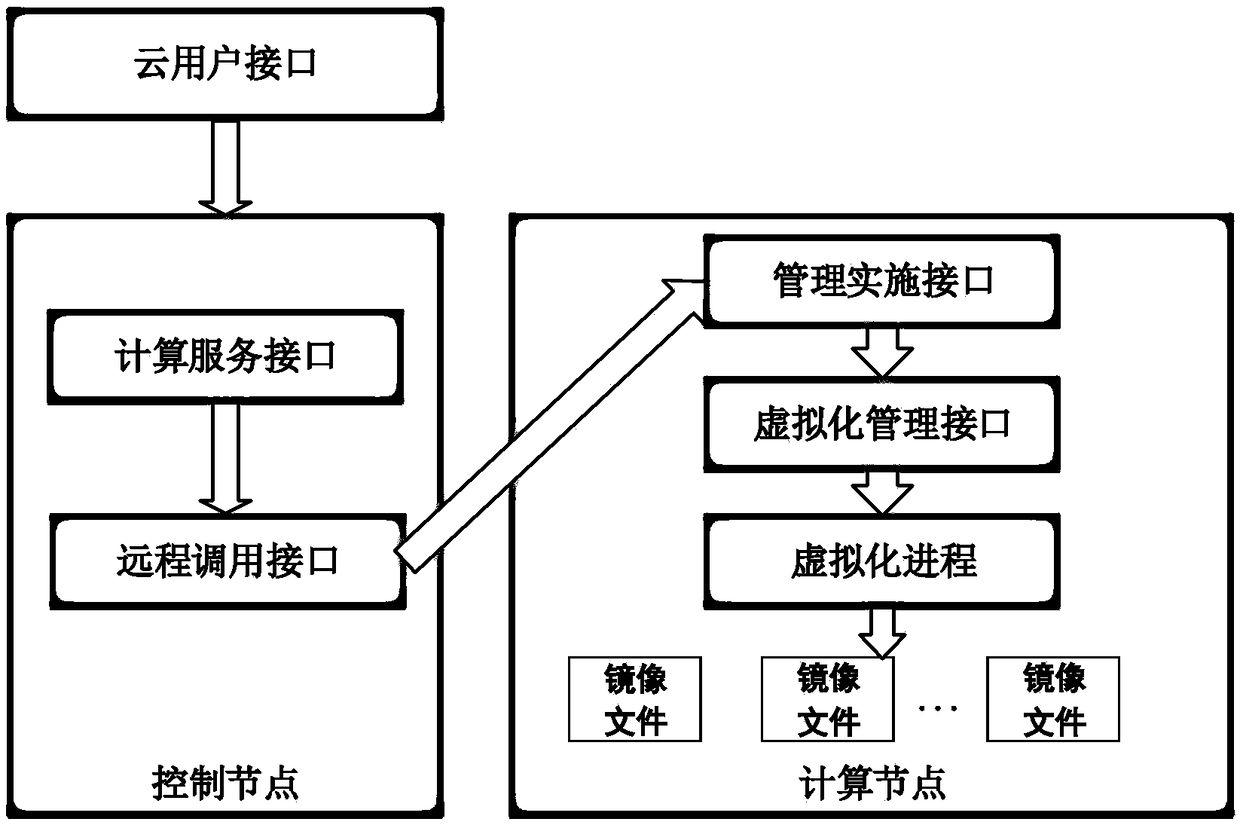
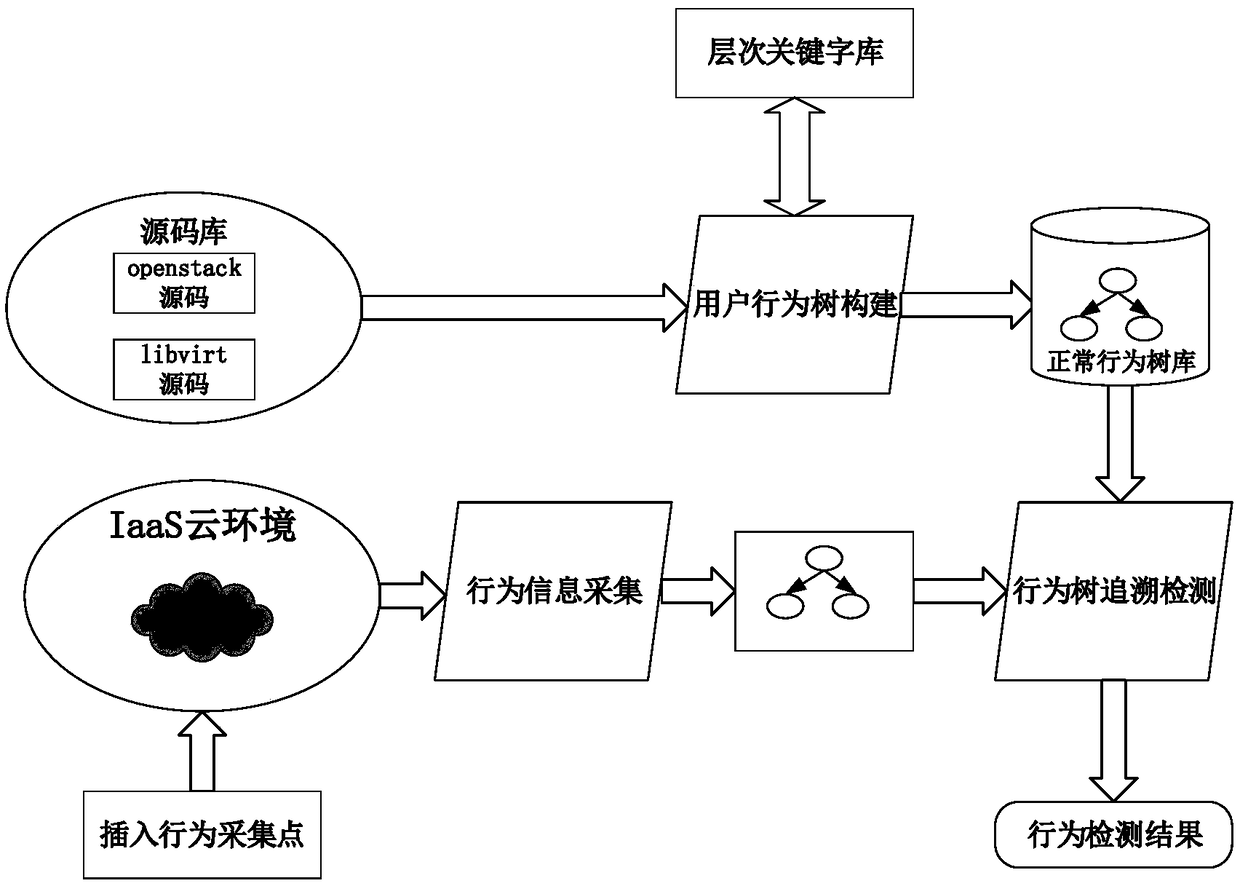
[0016] The present invention provides an internal threat-oriented behavior traceability detection method under the IaaS cloud environment, which is based on the calling process of user access data behavior in the IaaS cloud environment, such as figure 2 From the user's request to the implementation to the user's virtual machine image file, there are cloud user interface, computing service interface, remote call interface, management implementation interface, virtualization management interface, virtualization process and other interface layers. The method is realized by three modules: a user behavior tree construction module, a behavior information collection module, and a behavior traceability detection module, as well as data interaction among the modules.
[0017] The present invention is implemented on the OpenStack open source cloud platform. Embed the behavior tree creation module, behavior collection module, and behavior detection module into the OpenStack cloud enviro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com