Identity authentication system based on quantum key card
An identity authentication and key fob technology, applied in user identity/authority verification, transmission systems, digital transmission systems, etc., can solve problems such as insufficient security, time stamp replay attacks, and high requirements for system time synchronization, and achieve good safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
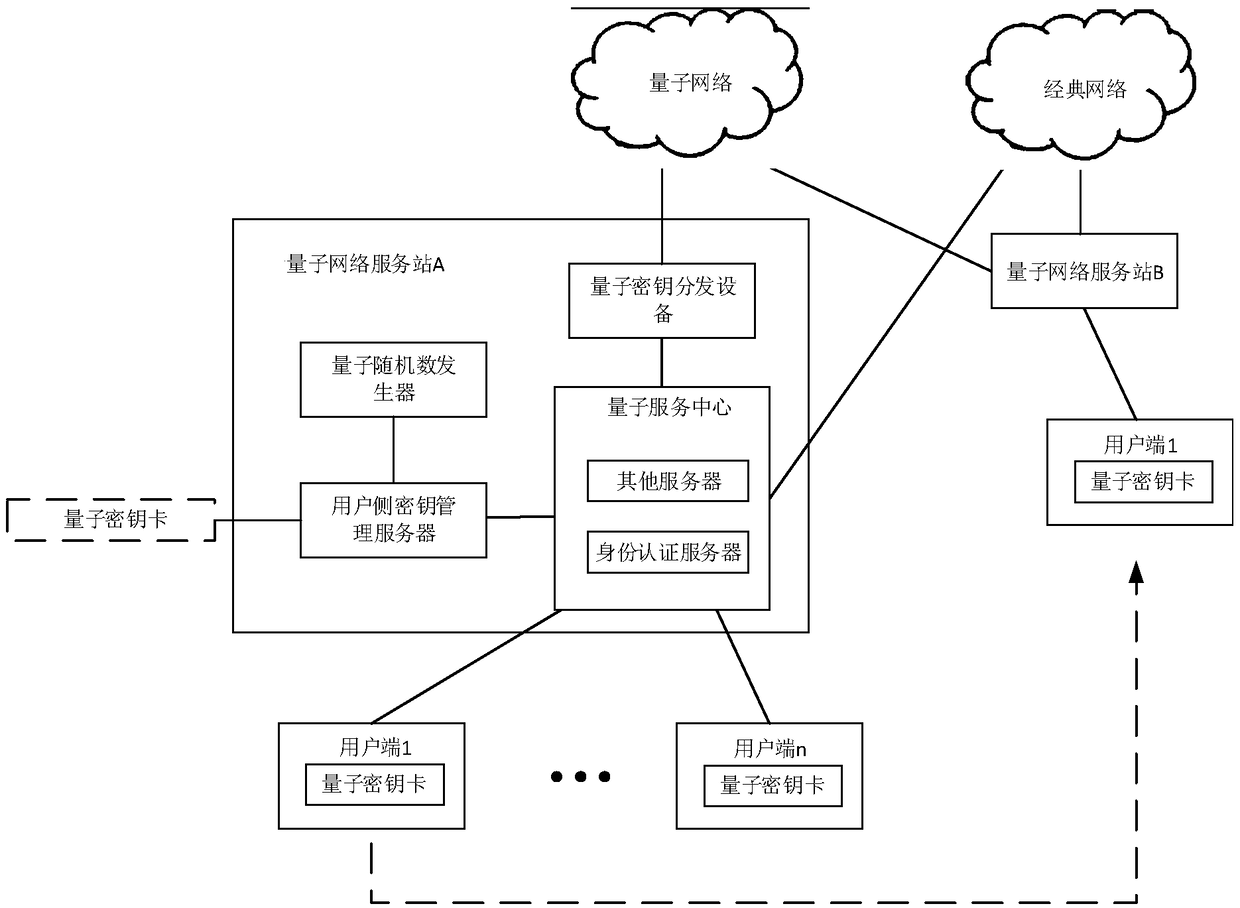
[0085] Embodiment 1, authentication of two client terminals belonging to the same quantum network service station in the local area network
[0086] In the following steps, the encryption, decryption and encryption operations involved in each client side are all performed in the matched quantum key card. The encryption and decryption operations involved in the identity authentication server and ticket permission server are completed in the encryption and decryption server of the quantum network service station.
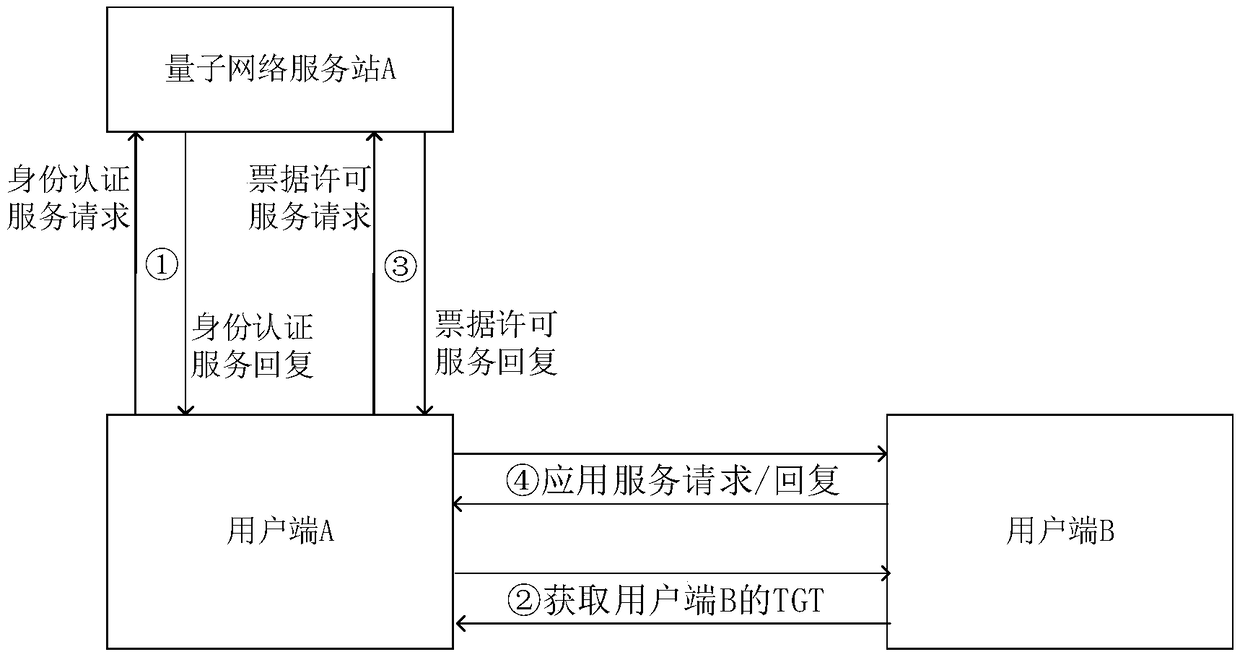
[0087] like figure 2 As shown, when both client A and client B belong to the same quantum network service station, the quantum key card involved in the identity authentication process is registered and issued at the local quantum network service station. For specific steps, see Figure 4 , in the figure, the curly brackets indicate the encrypted part, and the content immediately following indicates the key used, such as {Ainfo+N 1}K A Indicates the use of K A En...
Embodiment 2
[0139] Embodiment 2, identity authentication of two client terminals in the wide area network
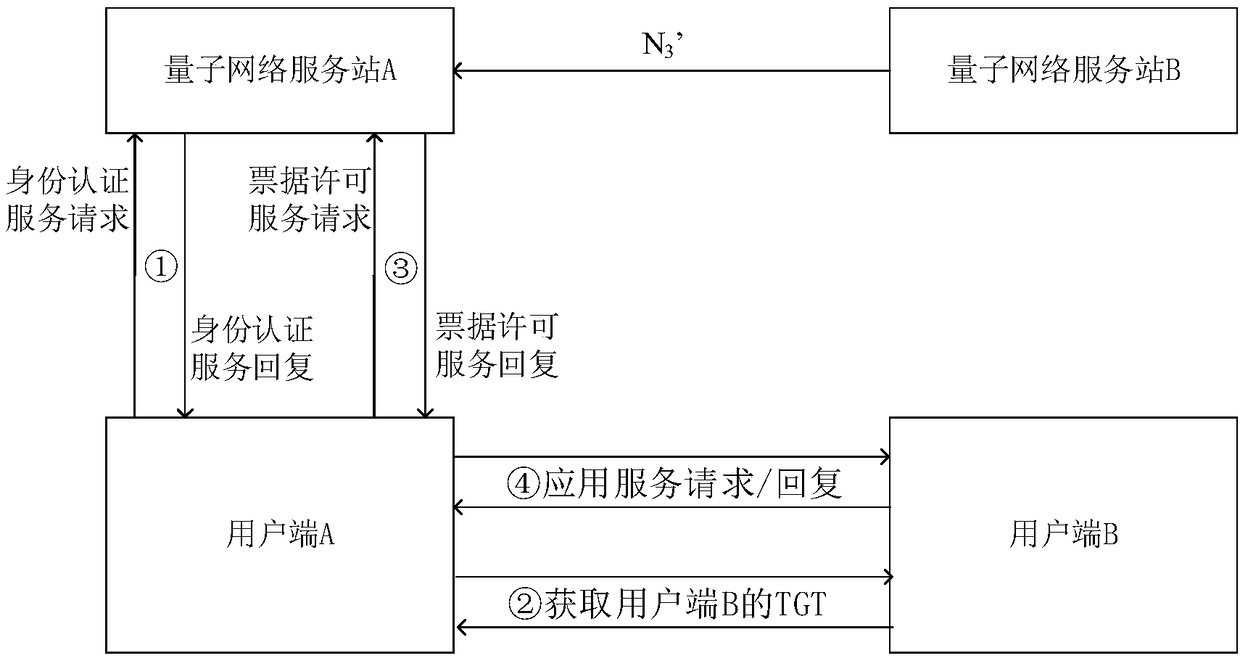
[0140] like image 3 As shown, when client A and client B do not belong to the same quantum network service station, the quantum key cards involved in the identity authentication process are registered and issued by the quantum network service station to which the client belongs. The difference between the system architecture in this embodiment and Embodiment 1 is that it is applied in a wide area network. The first-level switching center is a quantum network core station in a prefecture-level city or a fairly large area, and the second-level switching center is a county-level city or equivalent. The quantum network core station of a large or small area, the quantum network service station is a quantum communication access site of a fairly large area of a township or street office.
[0141] The primary switching center is connected with multiple subordinate secondary switching ce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com