Defense system and method for Internet-of-Things system to resist DDOS attack
An Internet of Things system and defense system technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve the problems of inability to defend against DDoS attacks, complicated environment configuration, and threatening DDoS attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] In view of the deficiencies in the prior art, the inventor of this case was able to propose the technical solution of the present invention after long-term research and extensive practice. The technical solution, its implementation process and principle will be further explained as follows.
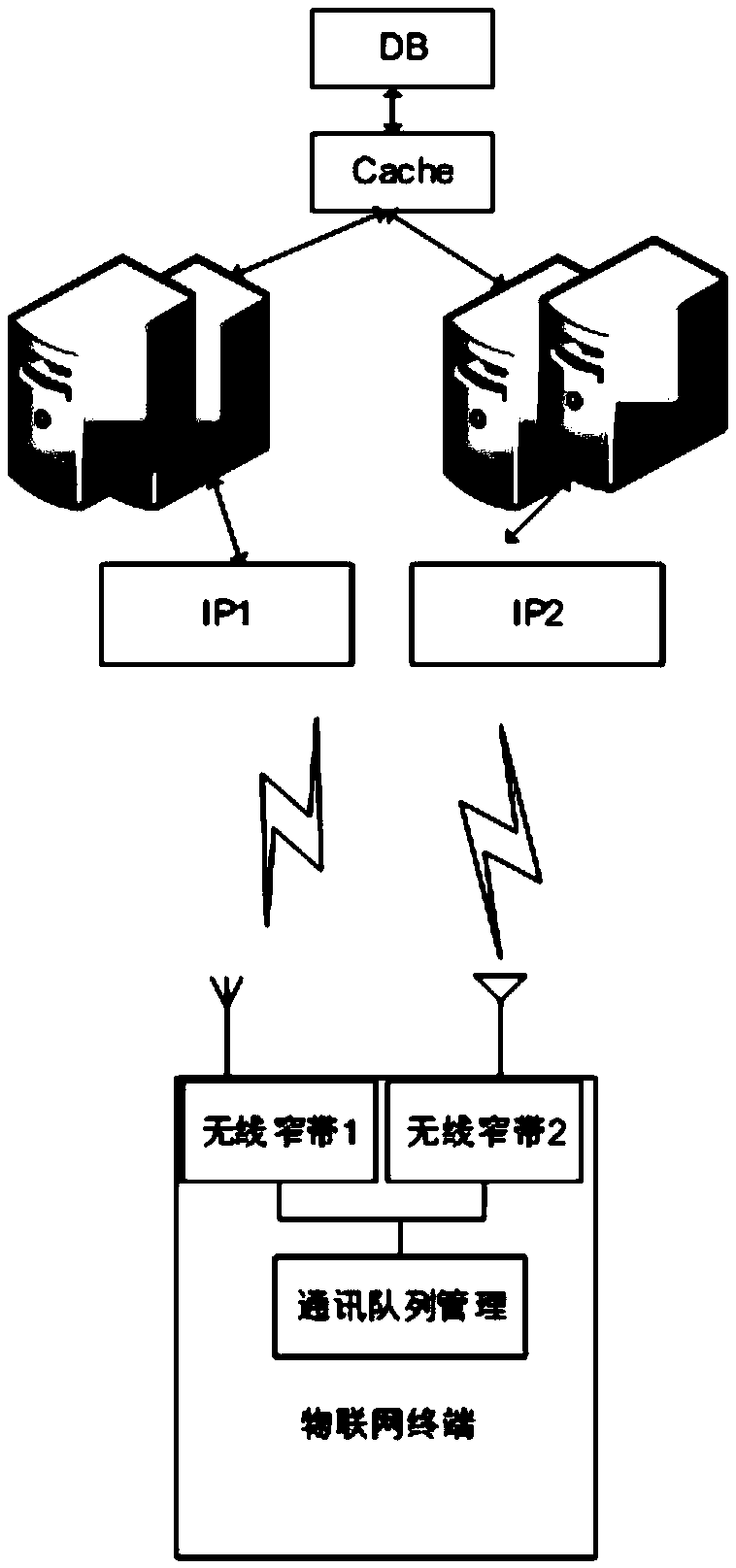
[0015] The embodiment of the present invention provides a defense system for the Internet of Things system to deal with DDOS attacks, which includes: two or more different server groups, and the terminals of the Internet of Things system access two or more different servers through more than one wireless narrowband Group, two or more different server groups work in parallel, and the two servers are connected to the same database.
[0016] Further, the defense system of the Internet of Things system against DDOS attacks includes: a first server group and a second server group, and the terminals of the Internet of Things system are respectively connected to the first server group via...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com