Detection method of wpa2 protocol vulnerability
A detection method and a vulnerability technology, applied in wireless communication, electrical components, security devices, etc., can solve problems such as threats to personal information security, personal information data theft, etc., to improve accuracy, improve detection efficiency and convenience Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
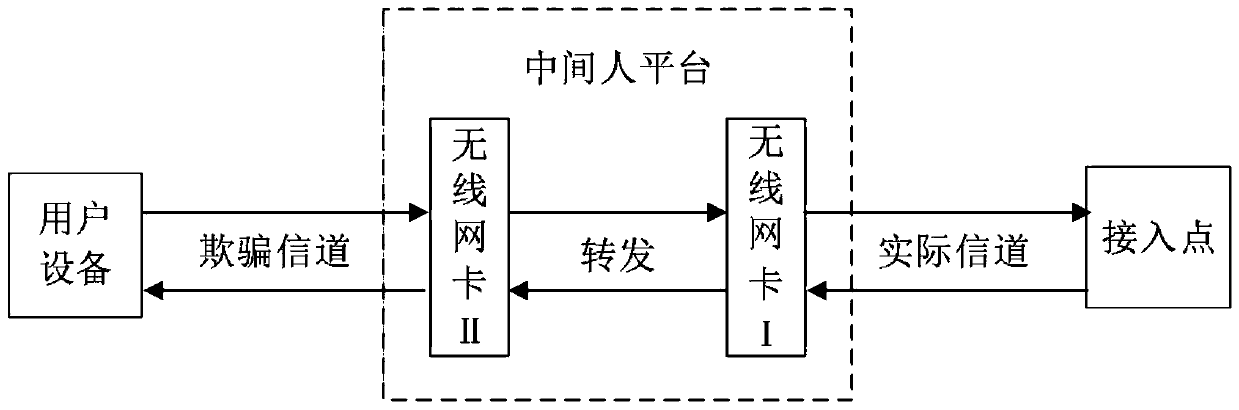
[0090] Embodiment 1, the detection device (hereinafter referred to as detection device for short) of WPA2 protocol vulnerability, such as Figure 4 As shown, it includes a control module 1 , a detection module 2 , a verification module 3 and a monitoring module 4 . The control module 1 is connected with the detection module 2, the verification module 3 and the monitoring module 4 respectively, and the control module 1 also communicates with the computer through the USB interface. The detection module 2 and the monitoring module 4 are respectively connected to the smart device under test through a network antenna, that is, the detection module 2 and the monitoring module 4 can transmit and receive wireless network signals. The monitoring module 4 is connected to the verification module 3 with signals.
[0091] Note: Figure 4 The arrows in indicate the direction of signal transmission, image 3 The dotted line in indicates that the signal is transmitted through the wireless ne...
Embodiment 2
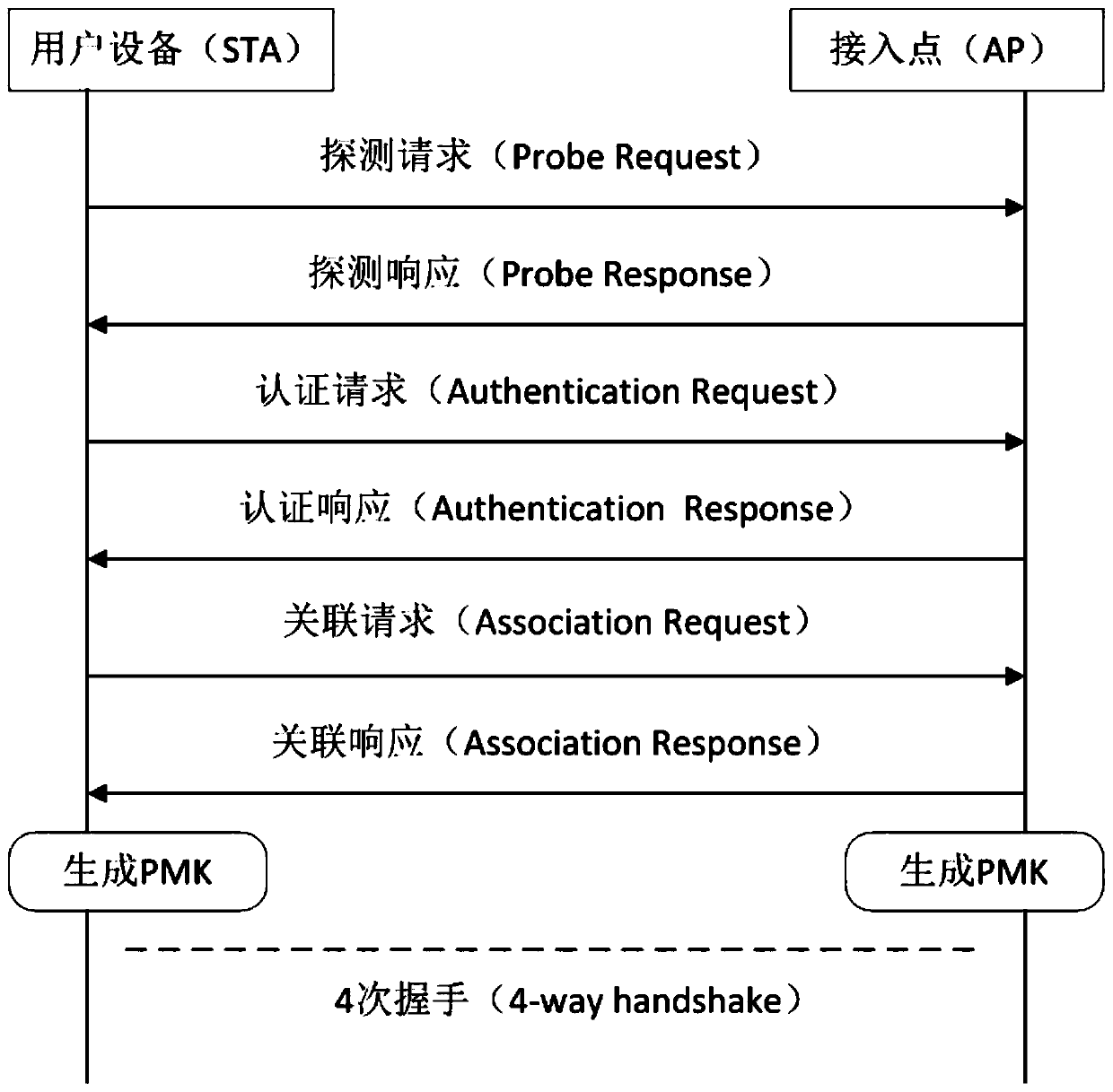
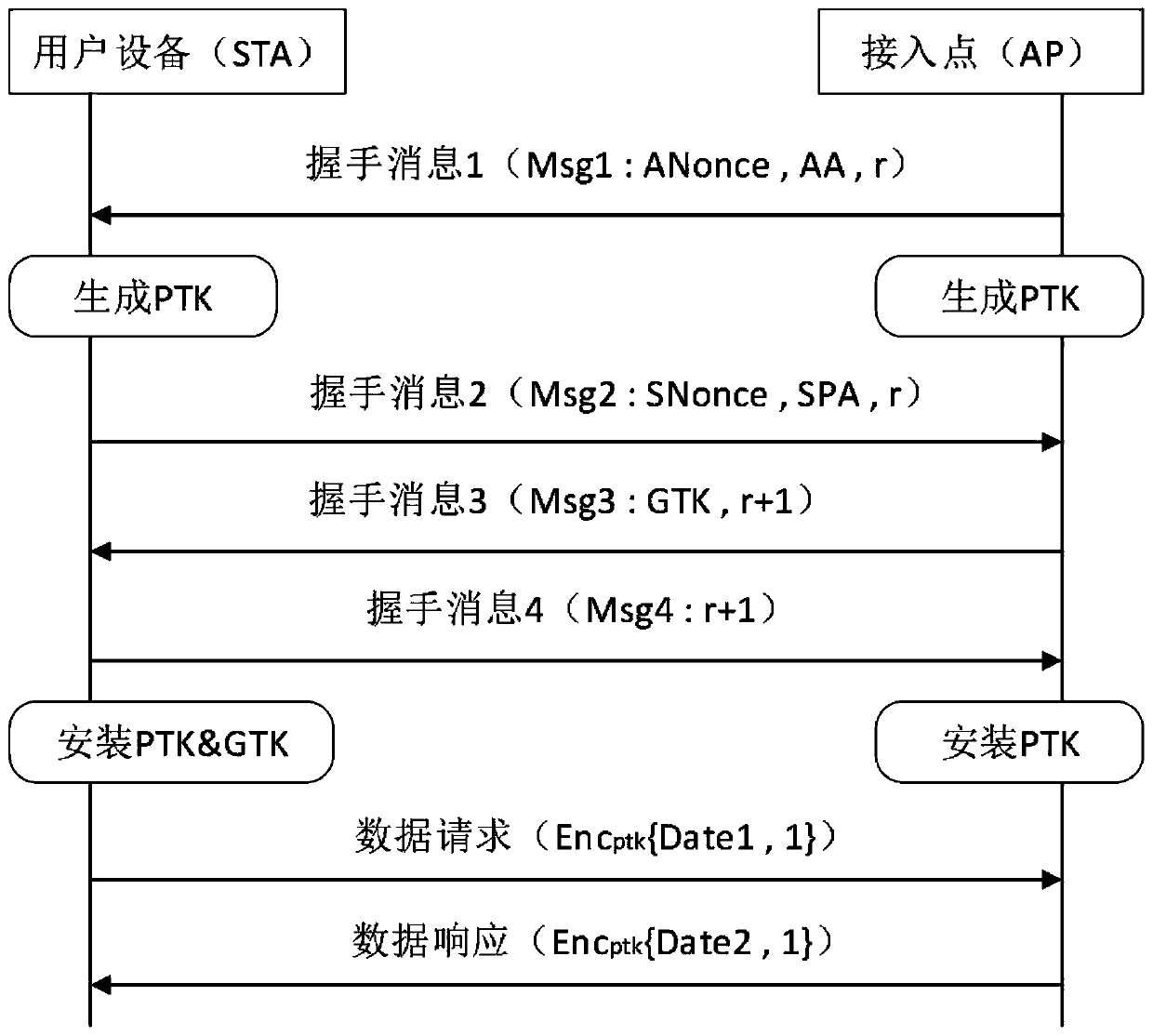
[0097] Embodiment 2, the detection method of WPA2 protocol vulnerability, such as Figure 5 and Figure 6 As shown, the detection device in Embodiment 1 triggers the vulnerability of the smart device to be tested by means of a message replay attack, thereby detecting whether the smart device to be tested has a WPA2 protocol vulnerability.
[0098] Such as Figure 5 As shown, the detection method for WPA2 protocol vulnerability using the detection device of embodiment 1 specifically includes the following steps:
[0099] Note: Figure 5 The arrows in the middle indicate the order of the steps, and the notes on the arrows indicate the requirements and instructions for the execution of the steps.
[0100] The following is a detailed description of the entire detection method according to the process:
[0101] S1. Start detection device:
[0102] The computer and the detection device are connected through a USB interface, and the staff configures the access point name and pas...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com