A method and system for deception prevention based on dynamic network constructed by SDN
A dynamic network, six-tuple technology, applied in the field of defense against network attacks, can solve the problems of inability to achieve dynamic construction, difficult to actively defend, and inability to obtain attacker information.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
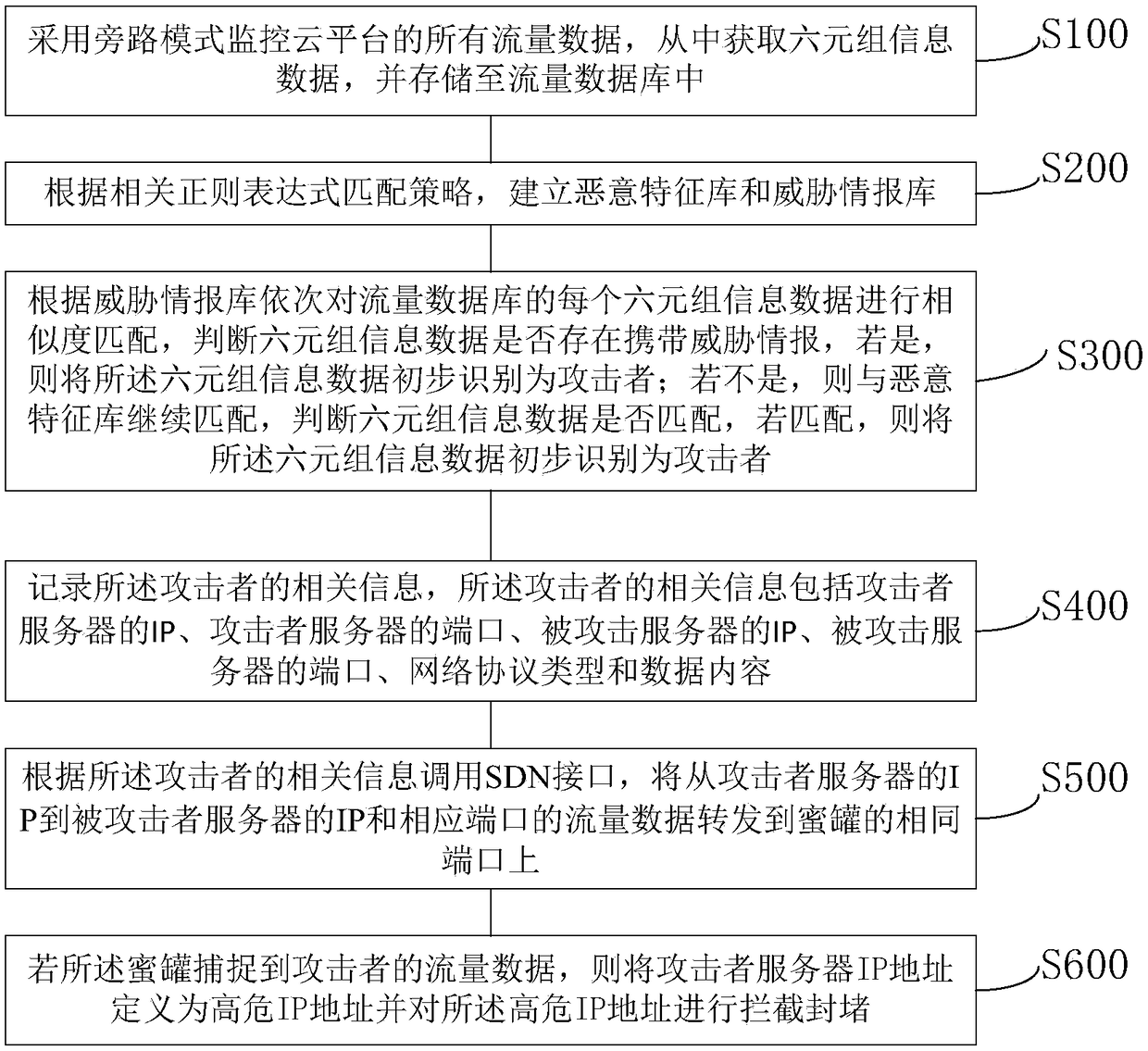
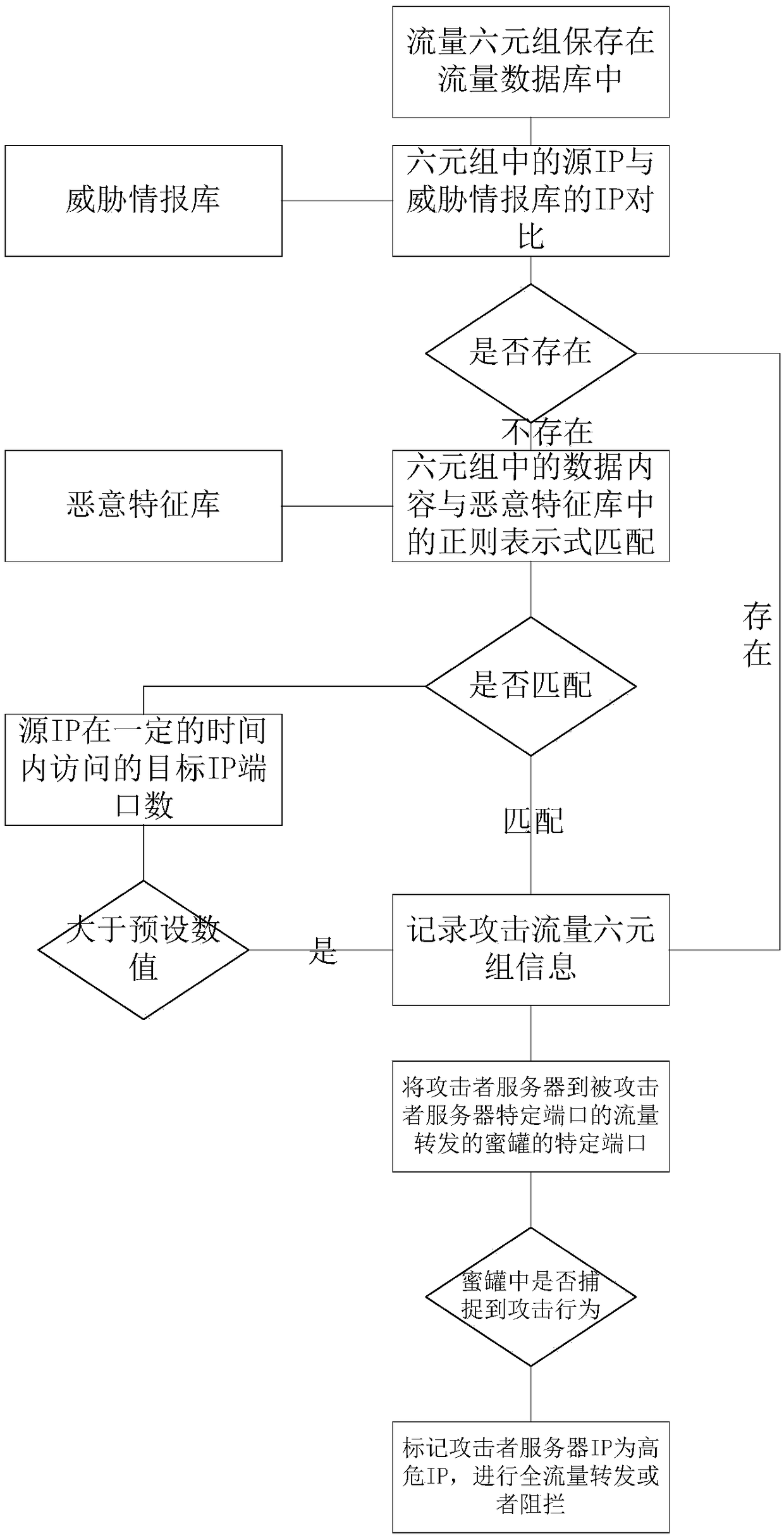
[0037] A deception defense method based on SDN to construct a dynamic network, such as figure 1 shown, including the following steps:
[0038] S100. Monitor all traffic data of the cloud platform in a bypass mode, obtain six-tuple information data therefrom, and store them in a traffic database;
[0039] S200. Establish a malicious signature database and a threat intelligence database according to relevant regular expression matching strategies;
[0040] S300. Perform similarity matching on each six-tuple information data in the traffic database in sequence according to the threat intelligence database, and determine whether the six-tuple information data carries threat intelligence, and if so, initially identify the six-tuple information data as an attack If not, then continue to match with the malicious signature database, judge whether the six-tuple information data matches, if match, then initially identify the six-tuple information data as an attacker;
[0041] S400. Re...
Embodiment 2
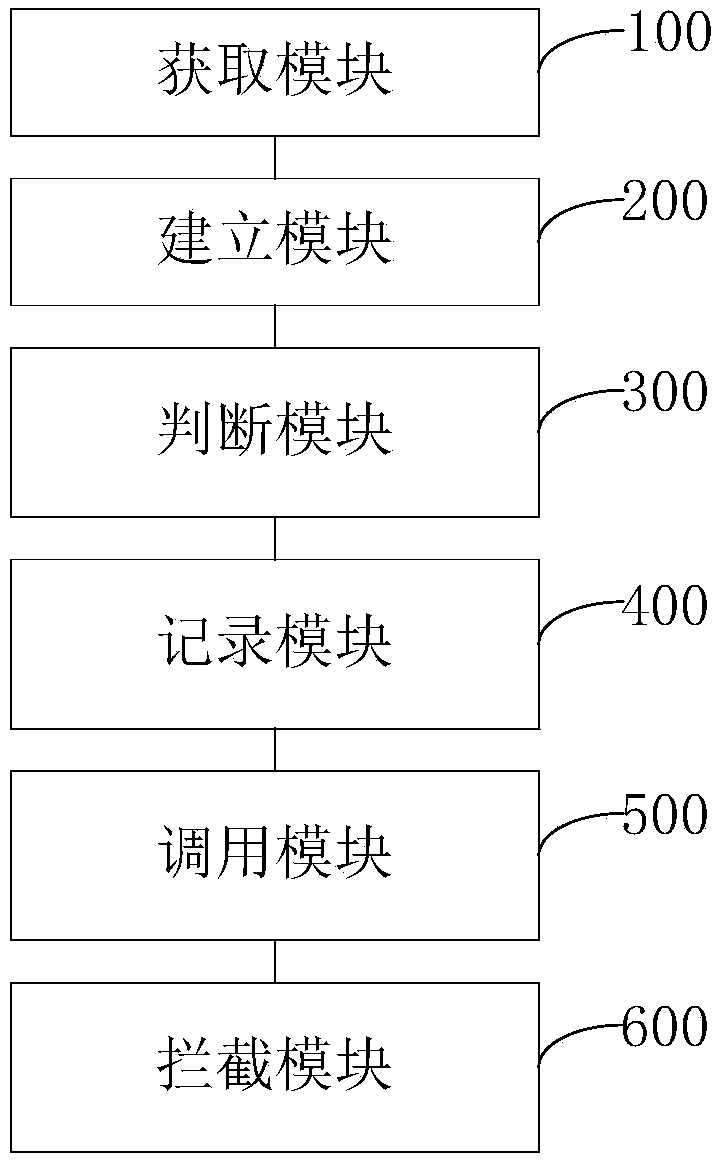
[0053] A deception defense system based on SDN to build a dynamic network, such as figure 2 As shown, it includes an acquisition module 100, an establishment module 200, a judgment module 300, a recording module 400, a calling module 500 and an interception module 600;
[0054] The acquisition module 100 is used to monitor all traffic data of the cloud platform in a bypass mode, obtain the six-tuple information data therefrom, and store it in the traffic database;
[0055] The establishment module 200 is used to establish a malicious signature database and a threat intelligence database according to relevant regular expression matching strategies;
[0056] The judging module 300 is configured to sequentially perform similarity matching on each six-tuple information data of the traffic database according to the threat intelligence database, and judge whether the six-tuple information data carries threat intelligence, and if so, compare the six-tuple information data The infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com