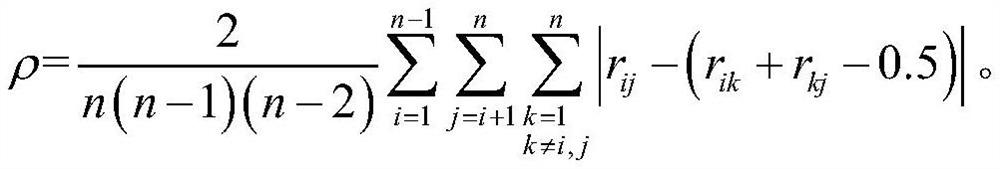A security protection method for measurement data
A technology for metering data and security protection, applied in the fields of digital data protection, data processing application, computing, etc., can solve the problems of low reliability of collection, influence of power grid stability, impact, etc., to improve estimation accuracy, reduce construction costs, and reduce construction costs. effect of investment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
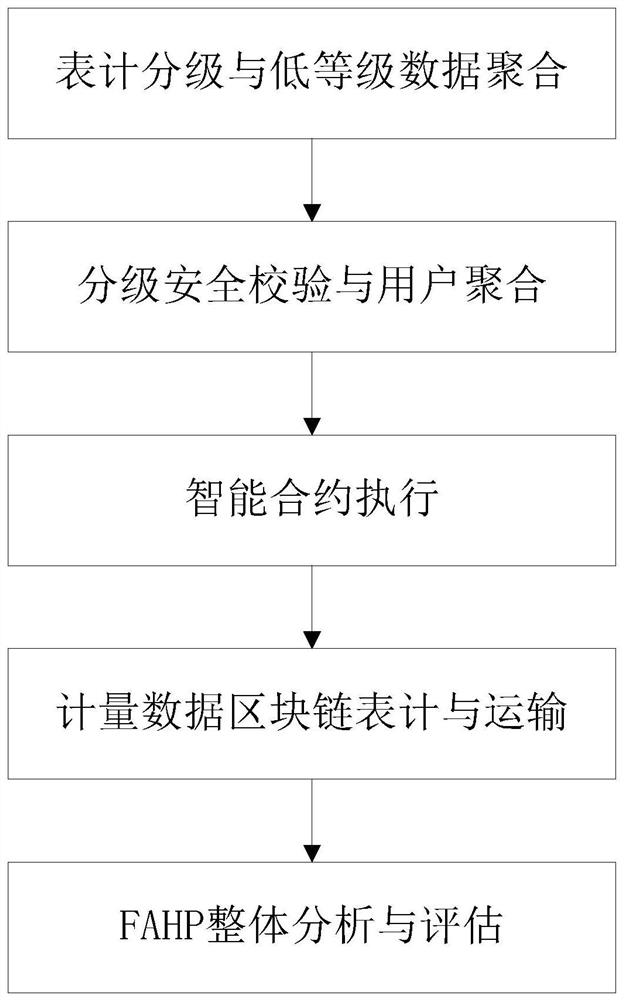
[0068] Embodiment 1: as figure 1 and figure 2 Shown; A measurement data security protection method, it includes:
[0069] S1: Classify the meters of users, charging piles, and two-way metering users, use the metering data of high-level users as blockchain label nodes alone, and integrate the metering data of low-level users according to the network topology as blockchain label nodes The high-level users refer to: 220kV and above electric energy metering devices for trade settlement, 500kV electric energy metering devices for assessment, or electric energy metering devices for measuring the power generation of generators with a stand-alone capacity of 300MW or above. The low-level users refer to: 10kV-220kV and above electric energy metering devices for trade settlement, 10kV-500kV electric energy metering devices for assessment, measuring the power generation of generators with a single unit capacity below 300MW, and power generation enterprises (stations) Electric energy m...
Embodiment 2
[0114] Example 2, in view of the problems affecting large-scale measurement security and transaction verification in the prior art, we analyzed the relevant factors and proposed some targeted technical means to solve the problems of insufficient data, numerous influencing factors, and interrelated issues. adverse conditions, and gives the following improved security metering and transaction process:
[0115] Such as figure 1 and figure 2 Shown; A measurement data security protection method, it includes:
[0116] S1: Classify the meters of users, charging piles, and two-way metering users, use the metering data of high-level users as blockchain label nodes alone, and integrate the metering data of low-level users according to the network topology as blockchain label nodes ; Step S1 classifies the measurement data in order to reduce the computational complexity of blockchain technology. Only specific large-scale users and large-scale charging pile groups that have a great im...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com