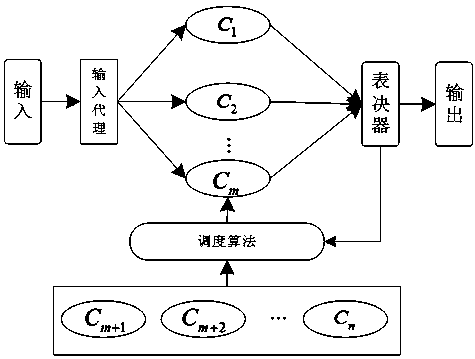
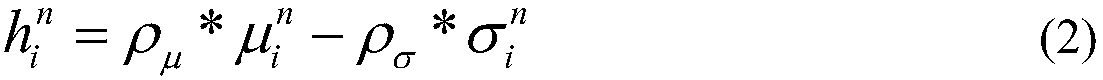Scenario-based dynamic scheduling method for heterogeneous execution of mimic web server
A dynamic scheduling and executor technology, applied in the field of network security, can solve problems such as the inability to fully guarantee the diversity of executors, the effective use of unfavorable mimic voting mechanisms, and the reduction of system security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
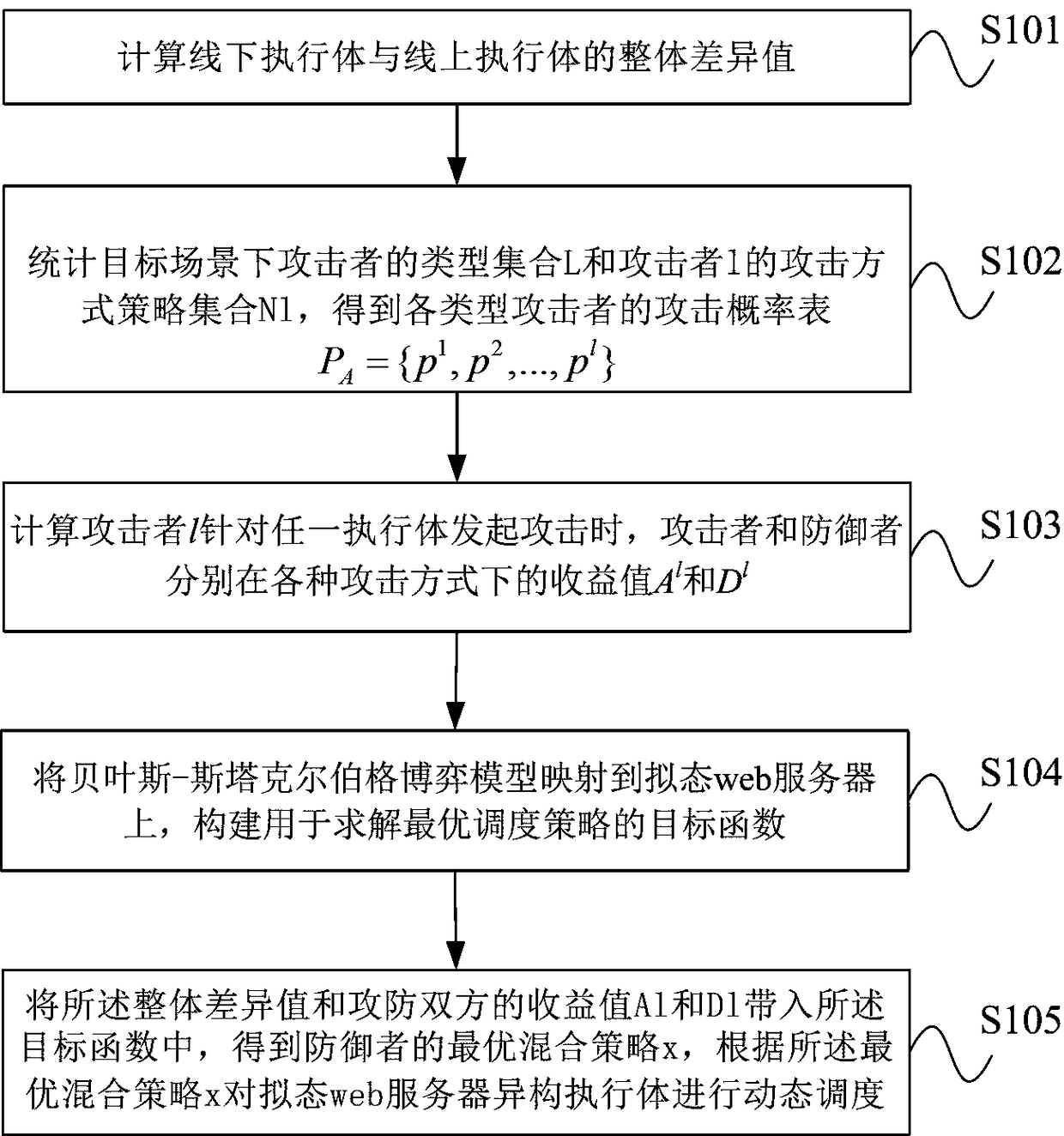
[0043] figure 2 It is a schematic flow chart of a scenario-based method for dynamically scheduling heterogeneous executives of a mimetic web server provided by an embodiment of the present invention. like figure 2 As shown, the method includes the following steps:
[0044] S101. Calculate the overall difference value between the offline execution body and the online execution body;
[0045] S102. Count the attacker type set L and the attacker l's attack method strategy set N in the target scenario. l , get the attack probability table P of various types of attackers A ={p 1 ,p 2 ,...,p l}, where l∈L;
[0046] S103. Calculate the income value A of the attacker and the defender in various attack modes when the attacker l launches an attack on any executive body l and D l ;
[0047] S104. Map the Bayesian-Stackelberg game model to the mimic web server, and construct an objective function for solving the optimal scheduling strategy;
[0048] S105. Comparing the overal...
Embodiment 2
[0051] On the basis of the first embodiment above, the present invention provides another embodiment, and the specific process is as follows:
[0052] S201. Calculating the overall difference between the offline executive and the online executive mainly includes the following sub-steps:
[0053] S2011: Calculate the difference ω between the execution body i and the execution body j ij ;
[0054] ω ij =C ij *P (1)
[0055] Among them, C ij =[c 0 ,c 1 ,c 2 ,... c t ] represents the difference value of each layer of the software stack from executive i to executive j, P=[p 0 ,p 1 ,p 2 ,...p t ] T Represent the weighting coefficient of the difference value of each layer of the software stack, and t represents the number of software stack layers of each executive body in the executive body set C of the mimic web server;
[0056] Specifically, according to the common vulnerabilities of different software at each layer of the software stack of executive body i and execut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com