Image encryption and hiding method and device, image decryption method and device
An image, encrypted image technology, applied in computer security devices, instruments, electronic digital data processing and other directions, can solve the problems of attack, increase information leakage, loss or change, etc., to achieve the effect of reducing image leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
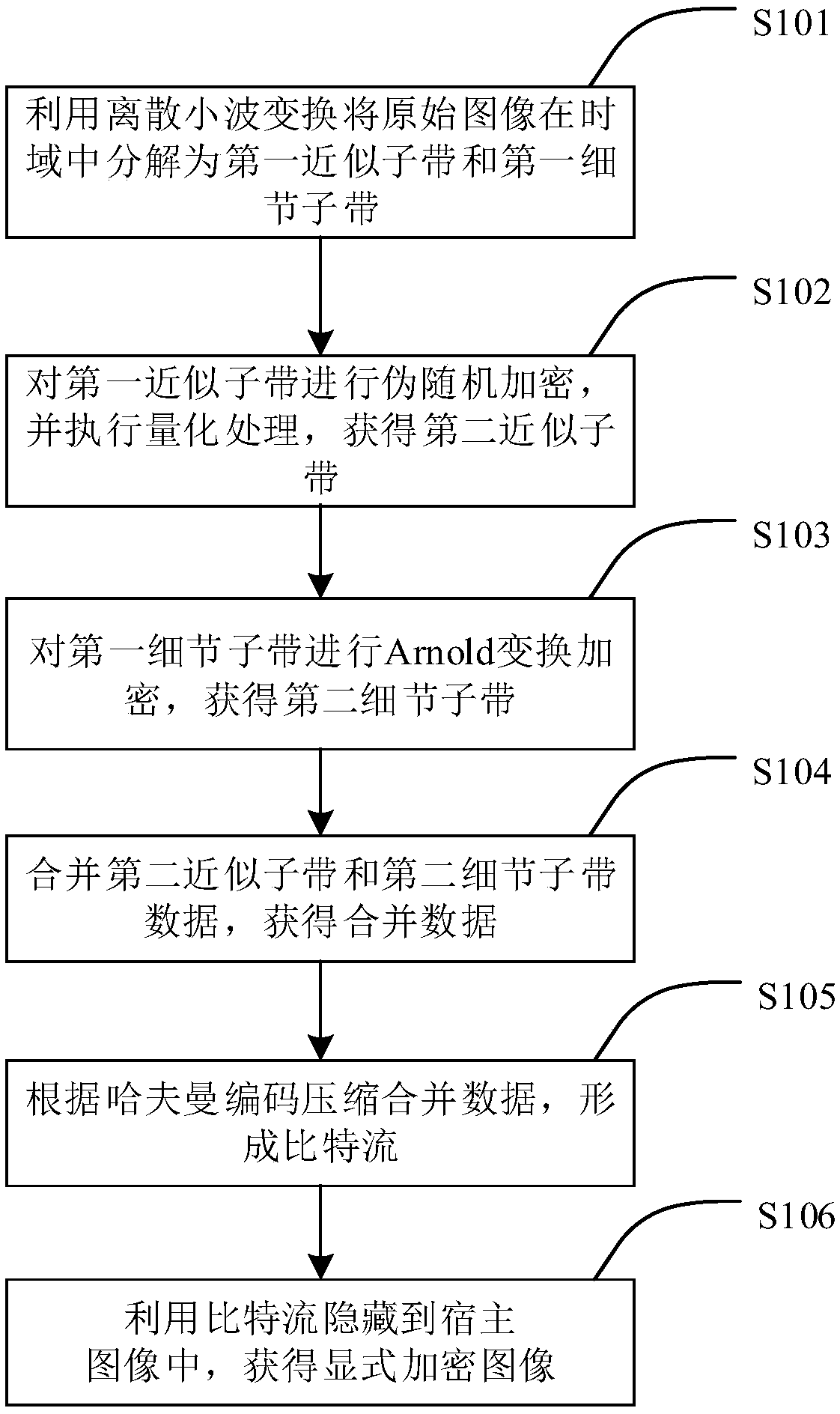
[0071] The embodiment of the present invention provides an image encryption and hiding method, such as figure 1 As shown, the method includes the following steps:
[0072] S101: Use discrete wavelet transform to decompose the original image into a first approximate subband and a first detail subband in the time domain.
[0073] Using discrete wavelet decomposition, the original image is decomposed into approximation sub-bands (LL) and detail sub-bands (LH, HL, HH), so that different encryption algorithms are performed on different domains for encryption.
[0074] S102: Perform pseudo-random encryption on the first approximate subband, and perform quantization processing to obtain a second approximate subband.
[0075] First, pseudo-random encryption is performed on the first approximate subband (LL). During pseudo-random encryption, a pseudo-random generator (Pseudo Random Number Generator, PRNG for short) is used to set a key K, which is used to generate data S randomly. A ...
Embodiment 2
[0106] An image decryption method provided by an embodiment of the present invention, such as Figure 7 As shown, the method includes:
[0107]S201: Extract a bit stream from an explicitly encrypted image by using lifting wavelet transform.
[0108] The above step S201 specifically includes:
[0109] S2011: Perform lifting wavelet decomposition on the explicit encrypted image to obtain a third approximation subband and a third detail subband.
[0110] The third detail subband (LH, HL, HH) is obtained after processing the explicitly encrypted image by lifting wavelet transform.
[0111] S2012: Take out the least significant bit of the binary number corresponding to each pixel value of the third detail subband in turn to obtain a bit stream.
[0112] The inverse process of the least significant bit replacement is performed, and the last two bits of the binary number corresponding to each pixel value of the third detail sub-band (LH, HL, HH) are sequentially taken out, and the...
Embodiment 3
[0129] An image encryption hiding device provided by an embodiment of the present invention, such as Figure 10 shown, including:
[0130] The decomposition module 31 is used to decompose the original image into a first approximate sub-band and a first detail sub-band in the time domain by using discrete wavelet transform. The main function of the decomposition module 31 is to use discrete wavelet decomposition to decompose the original image into approximate sub-bands (LL) and detail sub-bands (LH, HL, HH), so that different encryption algorithms are performed on different domains to encrypt. .
[0131] The approximate sub-band encryption module 32 is configured to perform pseudo-random encryption on the first approximate sub-band, and perform quantization processing to obtain the second approximate sub-band. The main function of the approximate sub-band encryption module 32 is to first perform pseudo-random encryption on the first approximate sub-band, and use a pseudo-ran...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap