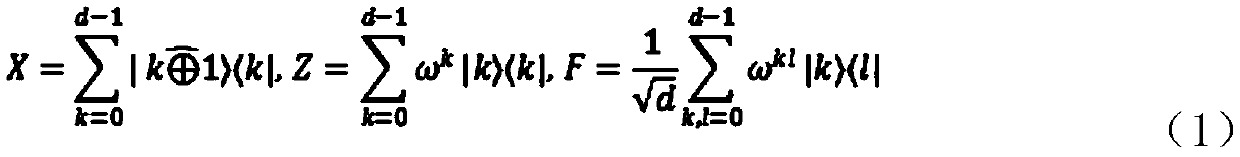Efficient and practical quantum secret sharing method based on d-level single particles
A quantum secret, single-particle technology, applied in the field of quantum information, can solve the problems of complex quantum operation ability and low efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
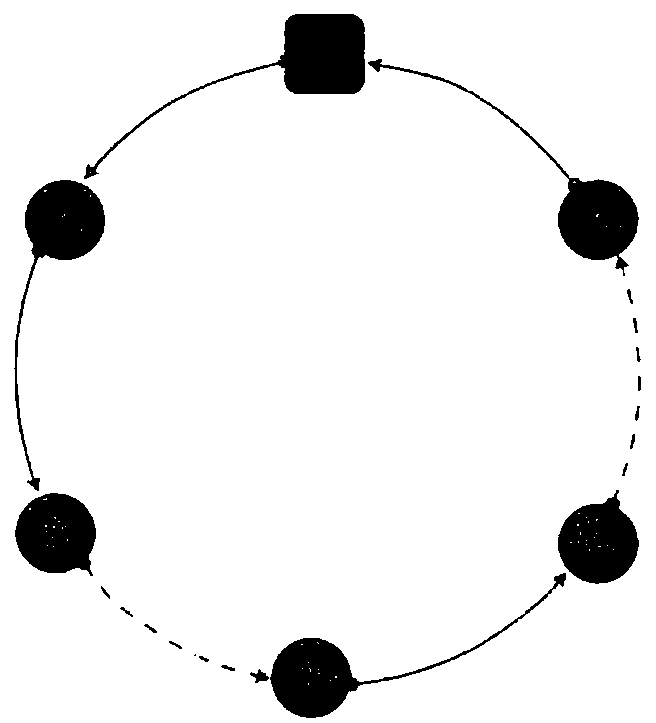
[0043] Such as figure 1 As shown, this embodiment provides an efficient and practical quantum secret sharing method based on d-level single particles, including the following steps:
[0044] Step S1: Let the secret distributor be R 0 , N participants are R 1 ,...R j ... R N , where R j is the jth participant; the secret distributor R 0 Divide the secret into N equal-length sub-secrets, and randomly distribute the N sub-secrets to N participants, who can collaborate to recover the distributor's secret;
[0045] Step S2: The secret distributor R 0 Provide a series of d-level single-particle strings as information carriers, that is, carrier particles, and embed random messages into carrier particles through local unitary operations on particles, and transmit the coded particle strings to the first participant R j (j=1); after receiving the particl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com