Method and system for realizing unified identity authentication strategy for micro-service architecture
A technology of identity authentication and implementation method, which is applied in the direction of transmission system, electrical components, etc., can solve the problems of increasing the complexity of associated configuration of business microservice nodes and gateways, increasing the consumption of server computing resources, and increasing the service pressure of public gateways, etc., to achieve Avoid cumbersome development and configuration problems, ensure non-simulation, and ensure the effect of legitimacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings, but it should be understood that the protection scope of the present invention is not limited by the specific embodiments.
[0033] Unless expressly stated otherwise, throughout the specification and claims, the term "comprise" or variations thereof such as "includes" or "includes" and the like will be understood to include the stated elements or constituents, and not Other elements or other components are not excluded.
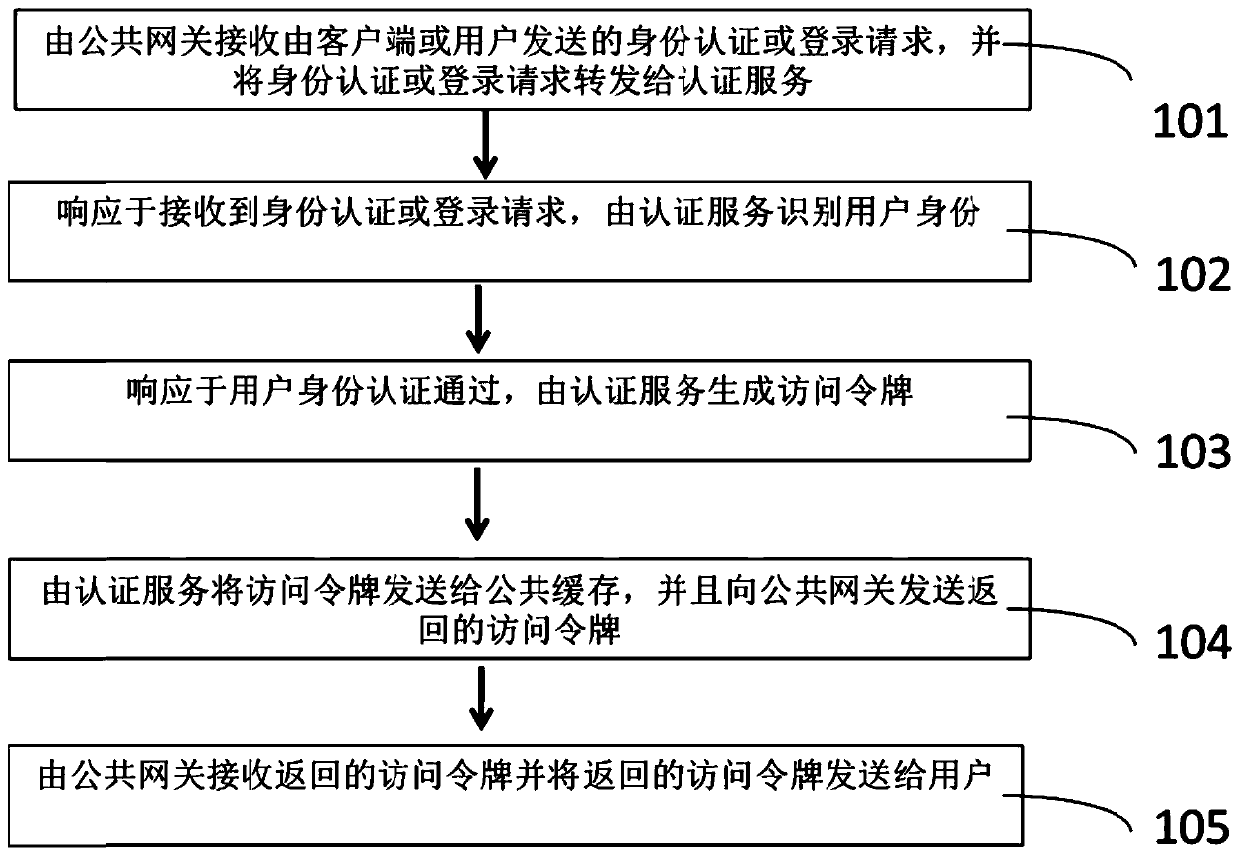
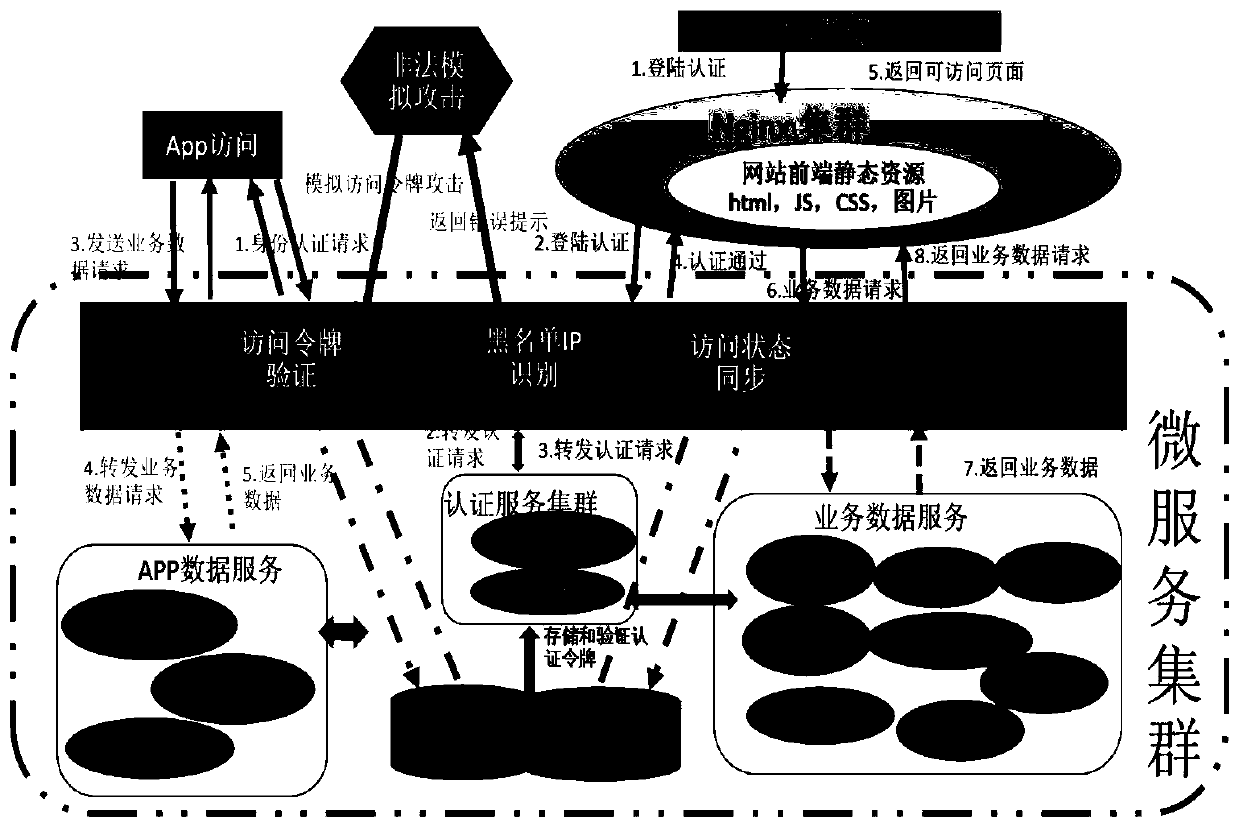
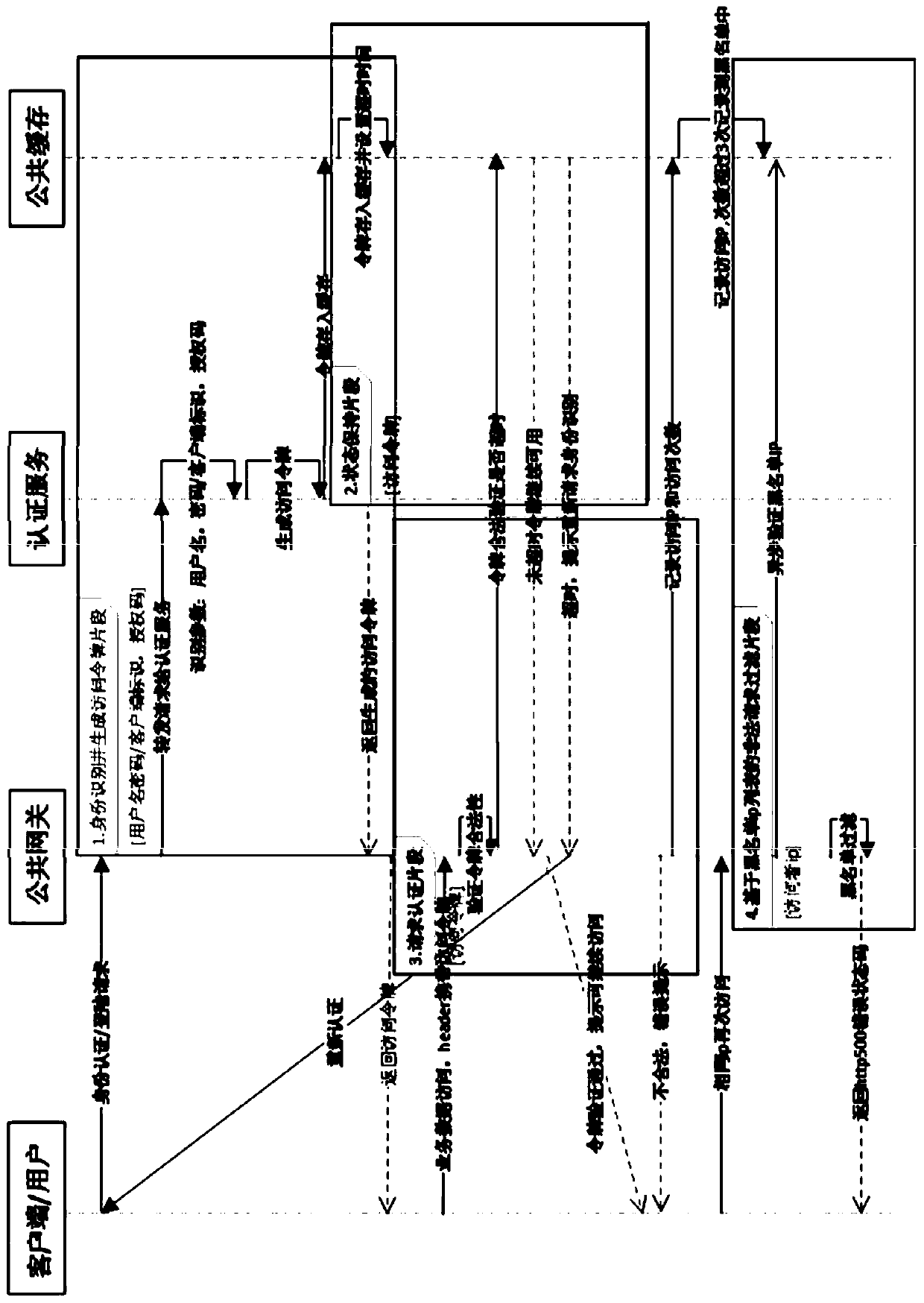
[0034] figure 1 It is a flowchart of a method for implementing a unified identity authentication strategy oriented to a microservice architecture according to an embodiment of the present invention. As shown in the figure, the implementation method of the microservice architecture-oriented unified identity authentication strategy of the present invention includes the following steps: Step 101: The public gateway receives t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com