Method for detecting camouflage intrusion information
A technology of normal information and covariance matrix, applied in the field of information security, can solve problems such as complex results, loss of personnel and property, and network system attacks, so as to improve detection efficiency and ensure safe and stable operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
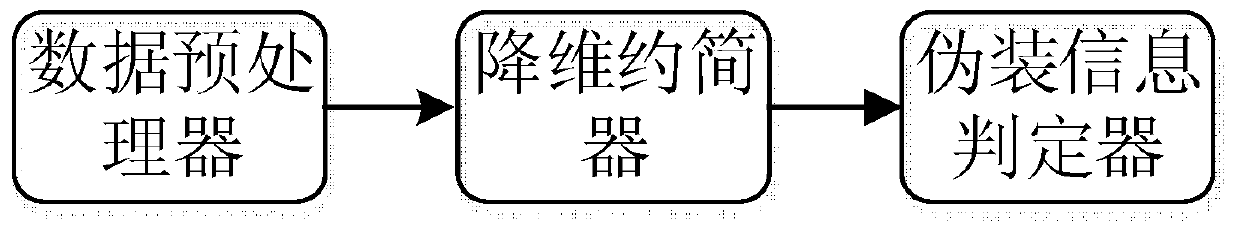
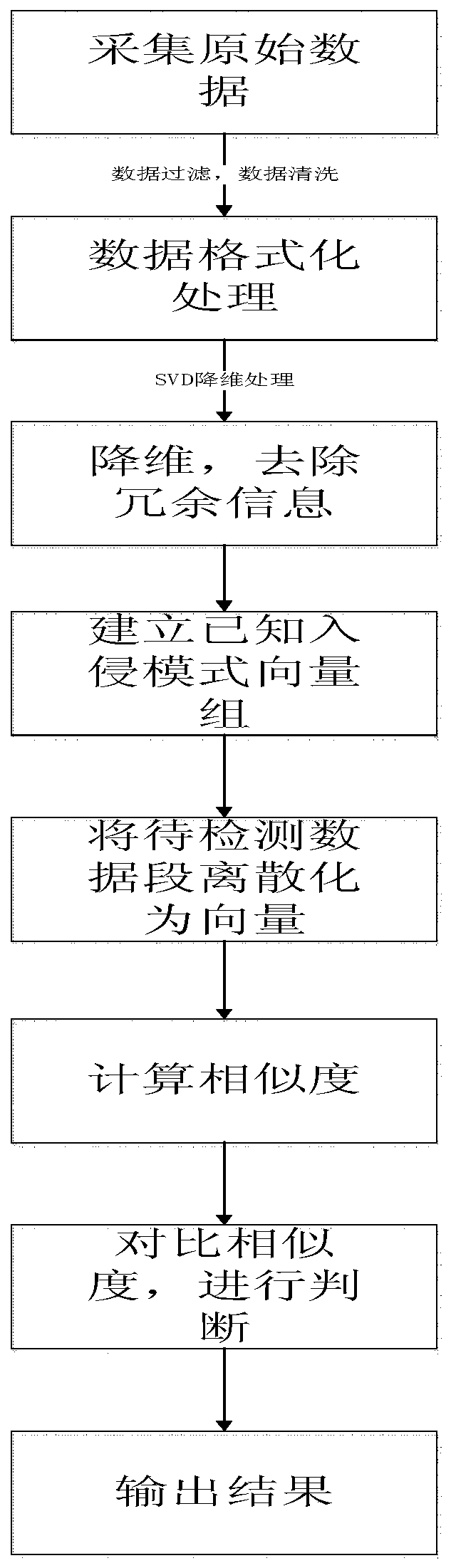
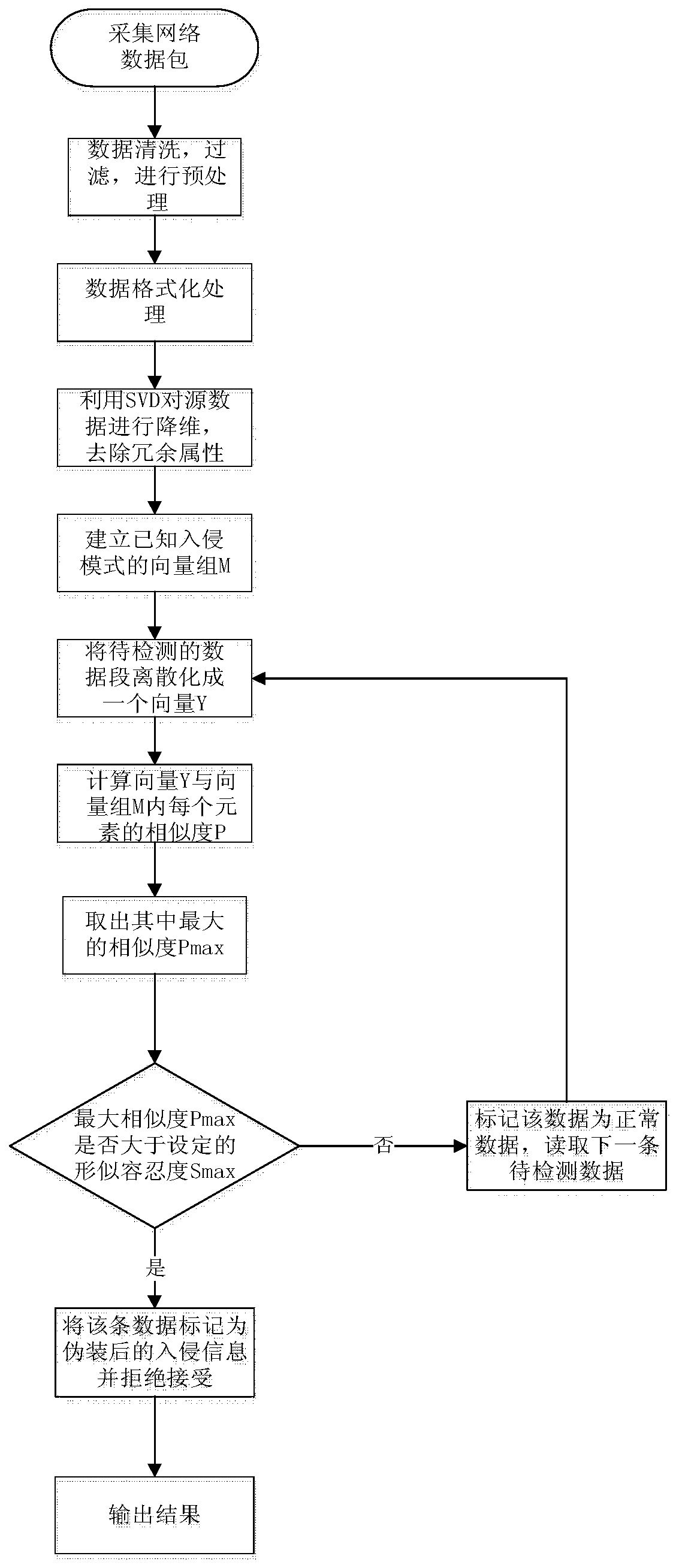
[0032] see Figure 1-Figure 3 , this embodiment provides a method for detecting masquerading intrusion information, including the following steps,
[0033] Step S1, grabbing network data, and filtering and formatting the data through a data preprocessor;
[0034] Step S2, reducing the dimensionality of the preprocessed data through a dimensionality reduction and deduplication device, and removing redundant attributes;
[0035] Step S3, use the masquerade information determiner to judge and detect the information that is masqueraded by disrupting the order of the intrusion characteristic data in the data packet in the data after dimensionality reduction and de-redundancy, if the similarity between the data and the known intrusion pattern is greater than the similarity tolerance , then it is determined that the information is a disguised intrusion information, and it is rejected; otherwise, the information is normal information, and it is allowed to accept.
[0036] In step S1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com