Malicious anchor node detection method based on isolated forest and sequential probability ratio test
A sequential probability ratio and detection method technology, applied in the direction of location information-based services, security devices, electrical components, etc., can solve the problems of misjudgment, failure to detect malicious anchor nodes, malicious anchor nodes cannot be detected, etc., to achieve detection More, detect real and accurate effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
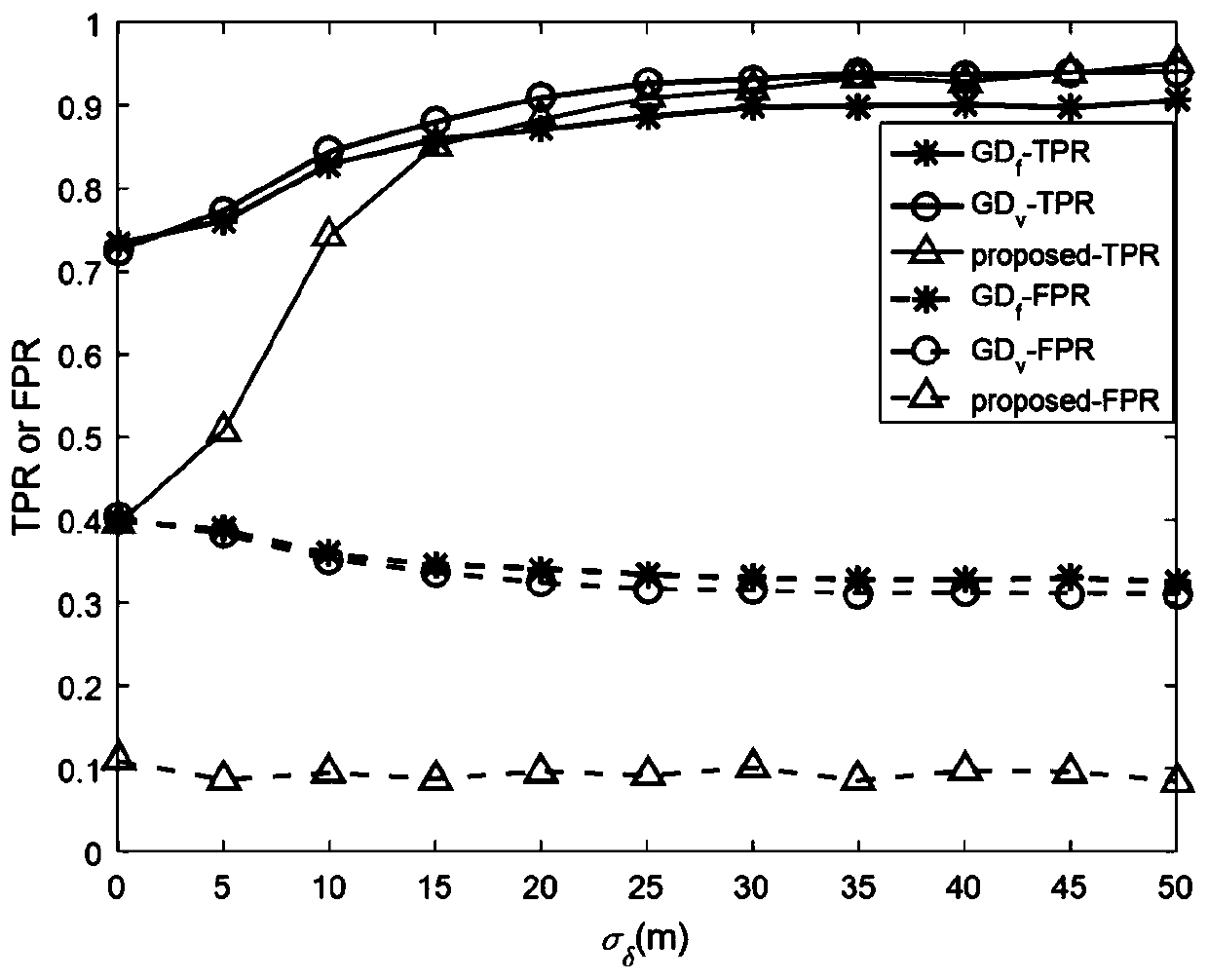
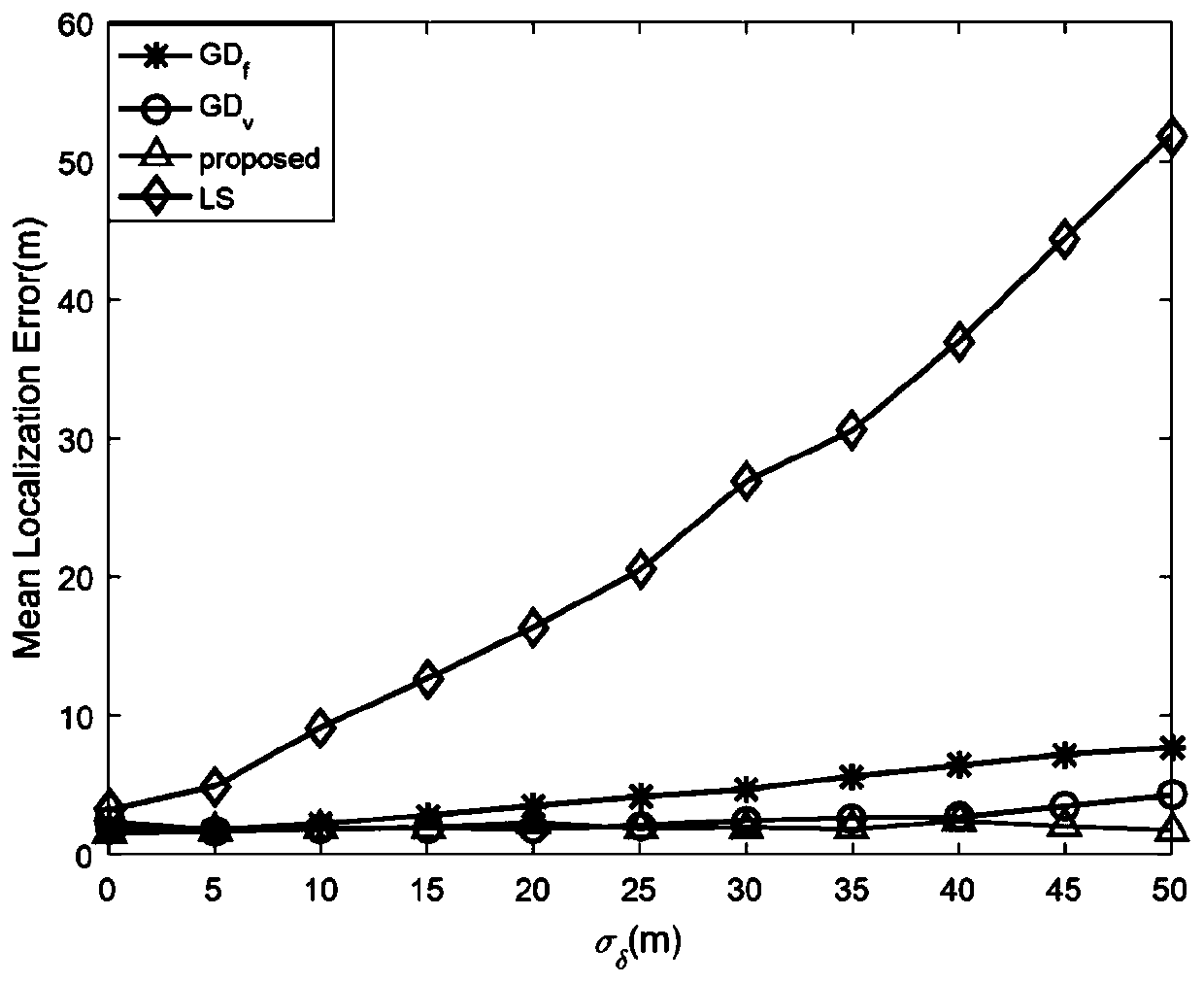
[0065] 30 anchor nodes and one target node are randomly deployed in a square area with an area of 60m×60m, among which there are 9 malicious anchor nodes. In the simulations performed, the standard deviation σ of the noise is measured under coordinated and non-coordinated attacks n Both are set to 2m, the mean value μ of the attack item under the non-cooperative attack δ Set to 4m.
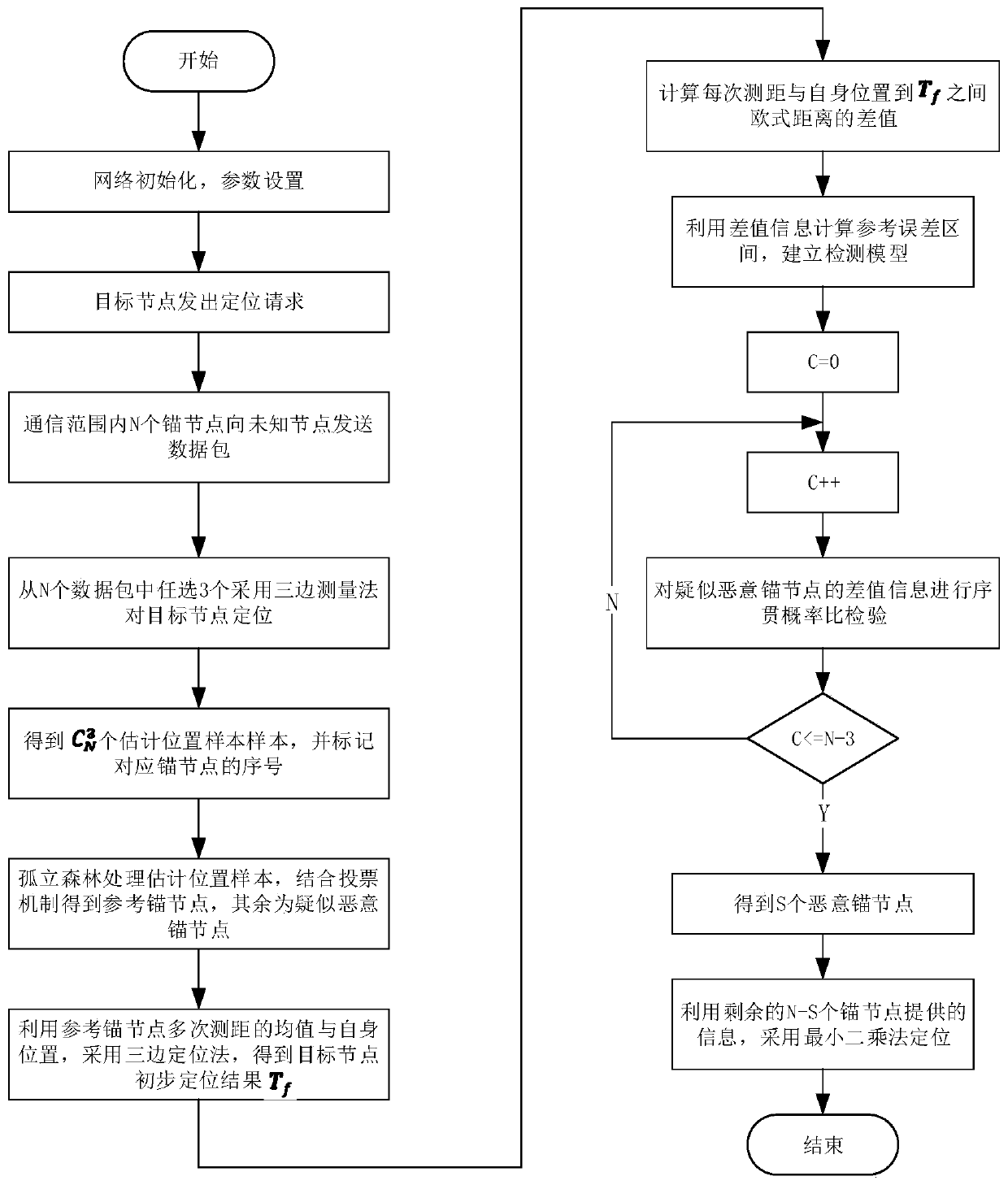
[0066] The application process is as follows: figure 1 As shown, there are multiple stages.
[0067] The first stage: the isolation forest determines the reference anchor node
[0068] The target node sends out a positioning request, and 30 anchor nodes within its communication range send data to the target node, and the target node obtains the location information of the anchor node and the ranging information between the anchor node and the target node, wherein the ranging information passes through the same A ranging method RSSI (Received Signal Strength Indication) is obtained;
[0069]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com