Whole apparatus having an authentication arrangement, and method for authentication
A technology for components and data processing devices, applied in the direction of computer security devices, internal/peripheral computer component protection, electrical components, etc. Simplified QA, tamper-proof measures and effects of attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
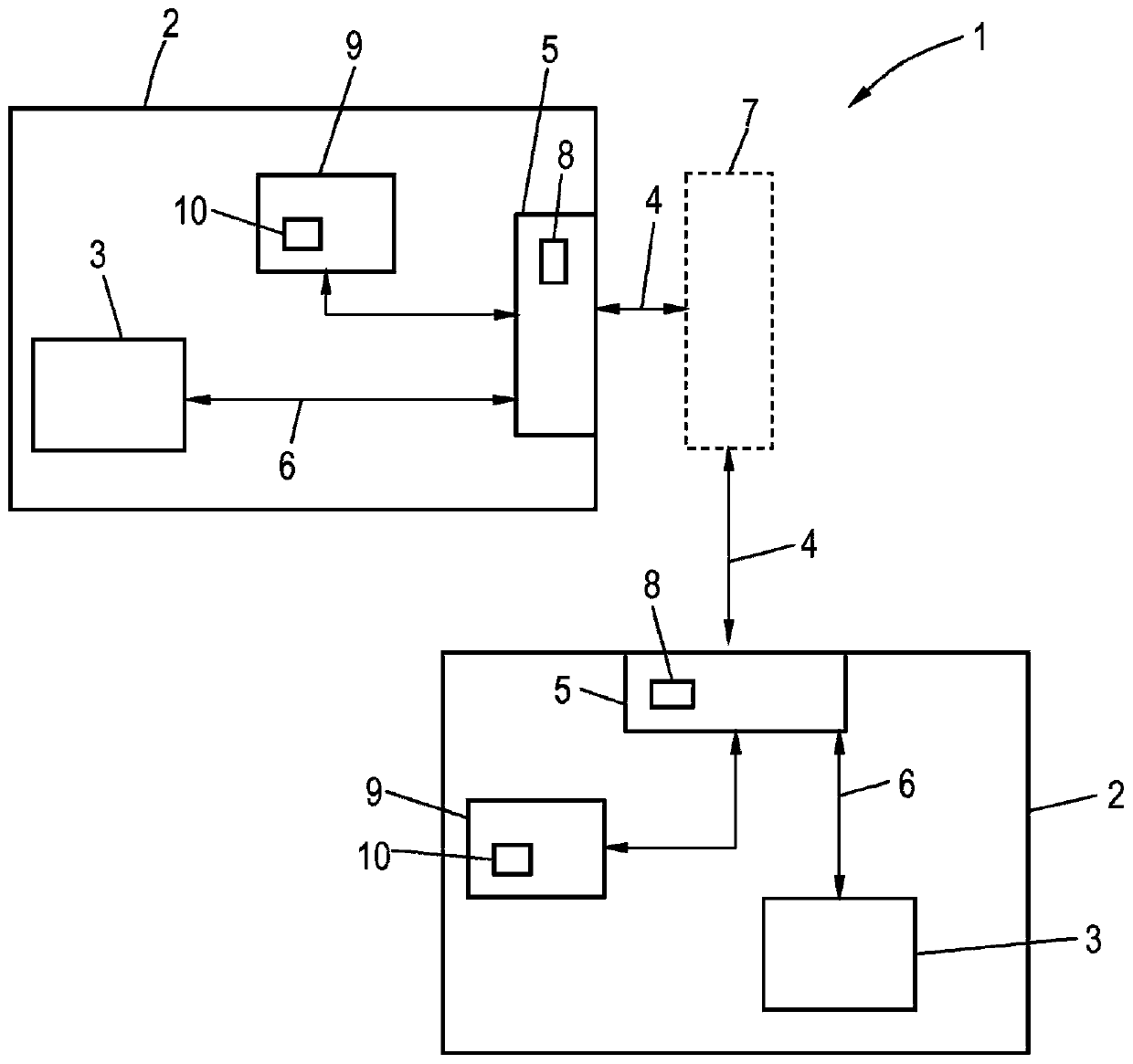
[0030] figure 1 An embodiment of an overall device 1 according to the invention is shown. In this case, the overall device 1 has, for example, the two illustrated data processing devices 2 , which each have a computing unit 3 , for example a CPU. Computing unit 3 may for example provide a common execution environment with a runtime system which can manage interrupt handling, drivers, applications and the like. The data processing devices 2 should be able to communicate with each other via the PCIe communication connection 4, and therefore both have an interface unit 5, which can be configured as a PCIe microchip, in an interrupt and user data connection 6 with the computing unit 3, which basically above is known. It is not important here whether the communication link 4 is run directly or via a bridge device 7 (which can be designed as a switch, router, multiplexer / demultiplexer) which is only indicated here, wherein , it should be pointed out that the bridging device 7 its...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com