Data encryption security storage method and system based on cloud platform and storage medium
A secure storage and data encryption technology, applied in the field of data security, can solve problems such as system suspension, failure to meet needs, and limited data throughput
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
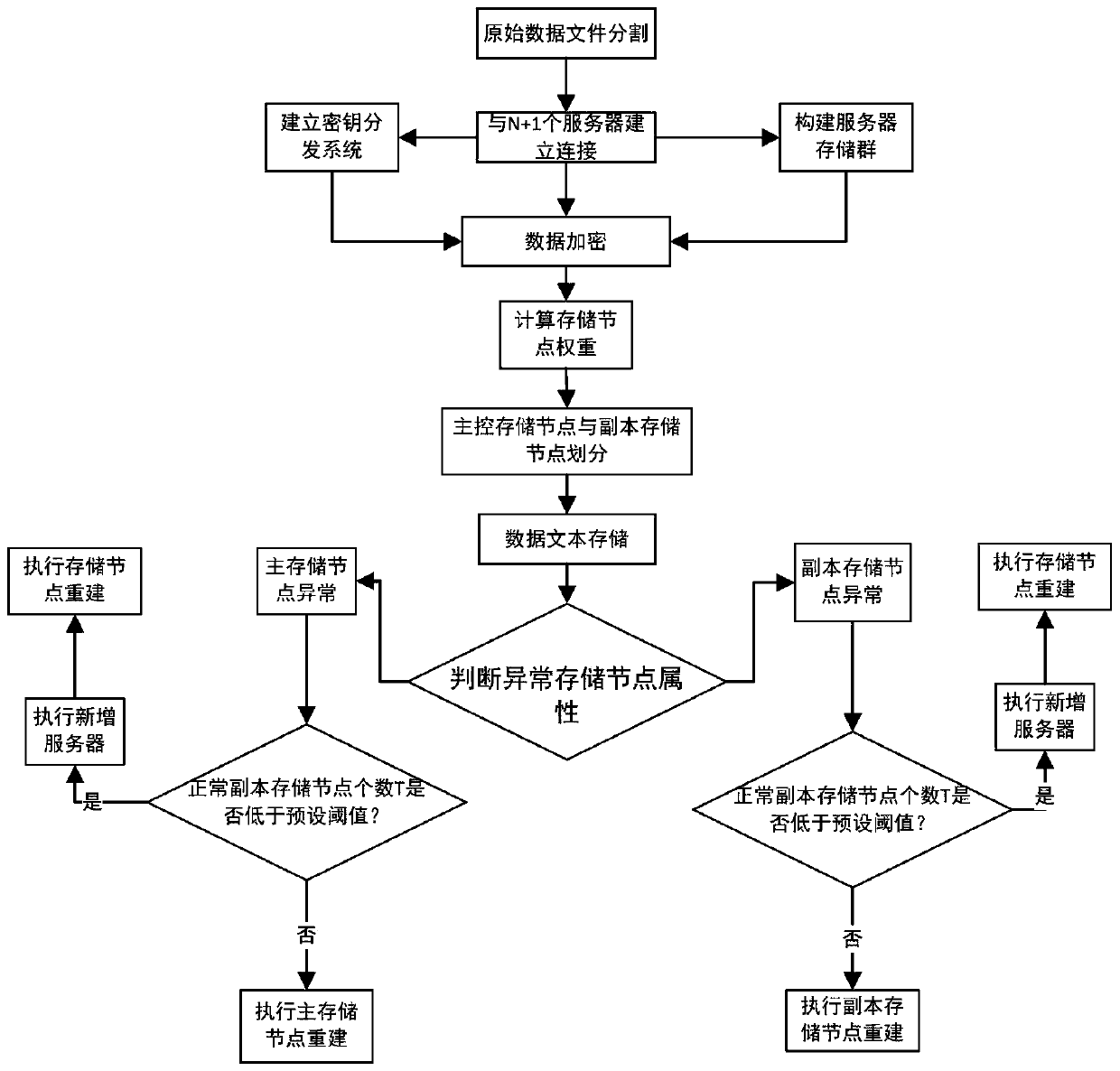
[0089] Please refer to figure 1 , a cloud platform-based data encryption security storage method of the present embodiment, comprising the following steps:
[0090] The user terminal divides the original data file F into N unit files f 1 … f N , including:
[0091] Use the erasure code or fountain code algorithm to encode the original data, and divide the original data into N data fragments, and use the hash algorithm to obtain the storage number according to the size and type of the data fragments, and generate N unit files f 1 … f N ;
[0092] The user terminal establishes a connection with N+1 servers through the cloud platform, and uses N+1 servers as key server nodes to build a key distribution system with the cloud platform and user terminals, and uses N+1 servers as storage nodes to build a key distribution system. The server storage group of above-mentioned original data file F;
[0093] The key distribution system is established based on the verifiable SM2 thr...
Embodiment 2
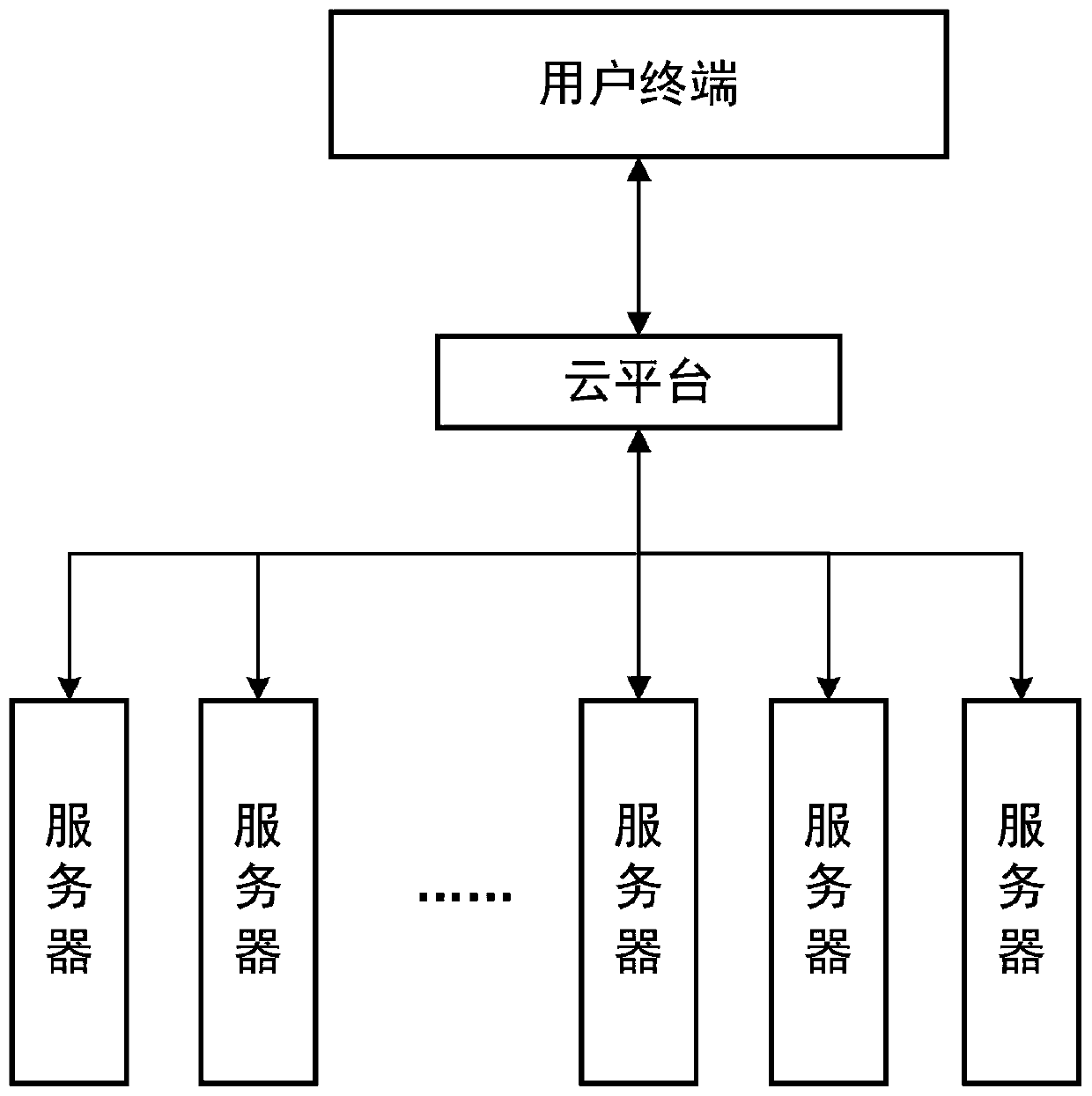
[0130] Please refer to figure 2 , the present embodiment provides a cloud platform-based data encryption security storage system, including:
[0131] user terminal;
[0132] cloud platform;
[0133] server module;
[0134] The user terminal executes dividing the original data file F into N unit files f 1 … f N , and establish a connection with the N+1 servers in the server module through the cloud platform, use the N+1 servers as key server nodes to build a key distribution system with the cloud platform and user terminals, and use the N+1 servers as key server nodes The storage node constructs the server storage group of the original data file F;
[0135] The key distribution system is established based on the verifiable SM2 threshold encryption scheme, generates and executes key distribution, and distributes the generated complete key to each key server node for encrypted storage;
[0136] The cloud platform provides data communication independent of the threshold cr...
Embodiment 3
[0179] This embodiment provides a storage medium, on which a computer program is stored, and when the computer program is run by a processor, the steps of the cloud platform-based data encryption secure storage method described in Embodiment 1 are executed.
[0180] The cloud platform-based data encryption security storage method, system and storage medium of the present invention reduce the oversupply of resources, can quickly recover from storage failures in parallel, can achieve an effective balance between storage and load, and reduce key leakage Unpredictable security threats, with good security and privacy protection features, ensure the security and risk resistance of data storage.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com