Multi-type data verification method and device, computer system and readable storage medium
A data verification and database technology, which is applied in the communication field, can solve the problems of time waste, verification code business intrusion, high labor cost, etc., and achieve the effect of avoiding time and energy costs, reducing business intrusion, and reducing time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
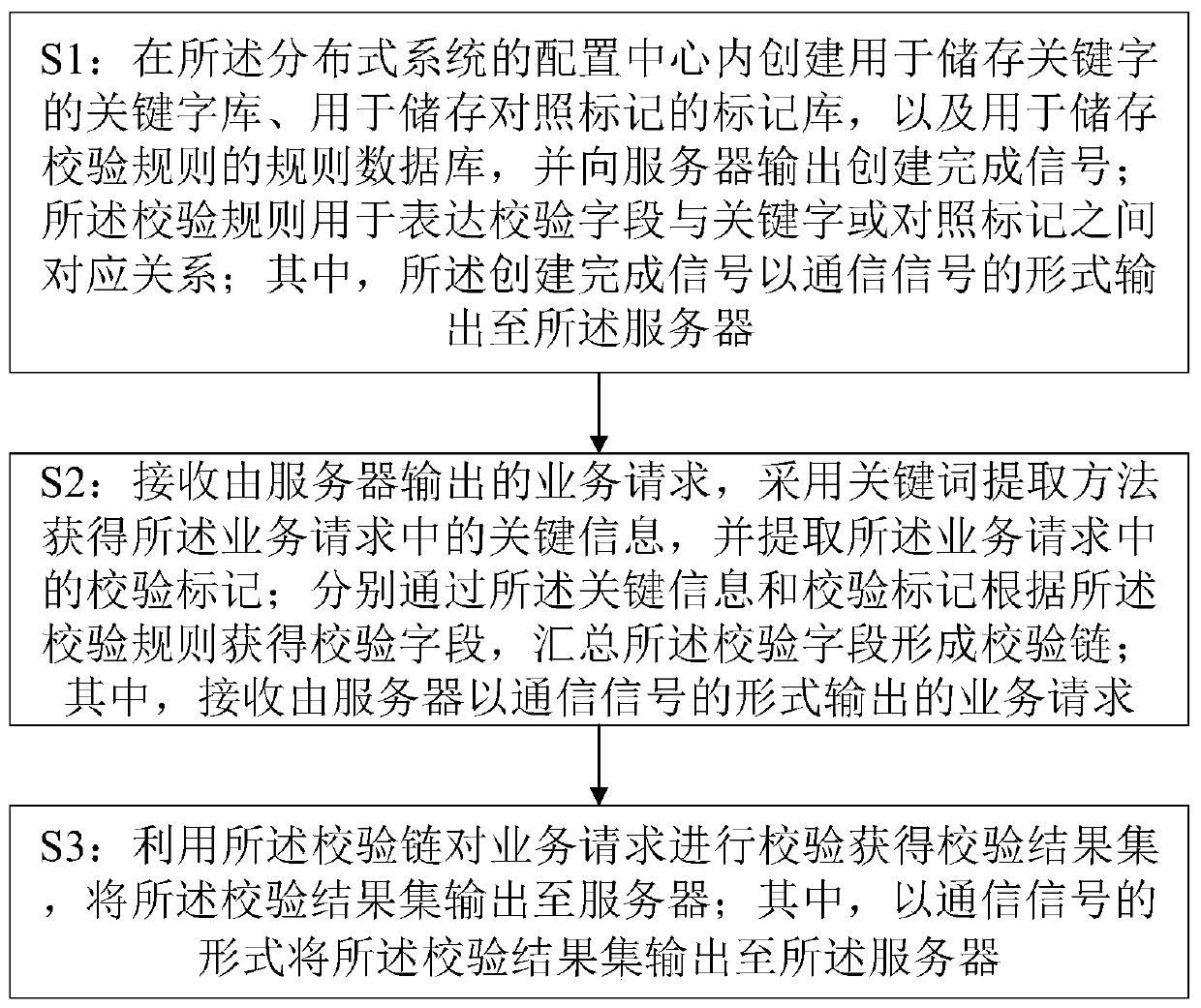
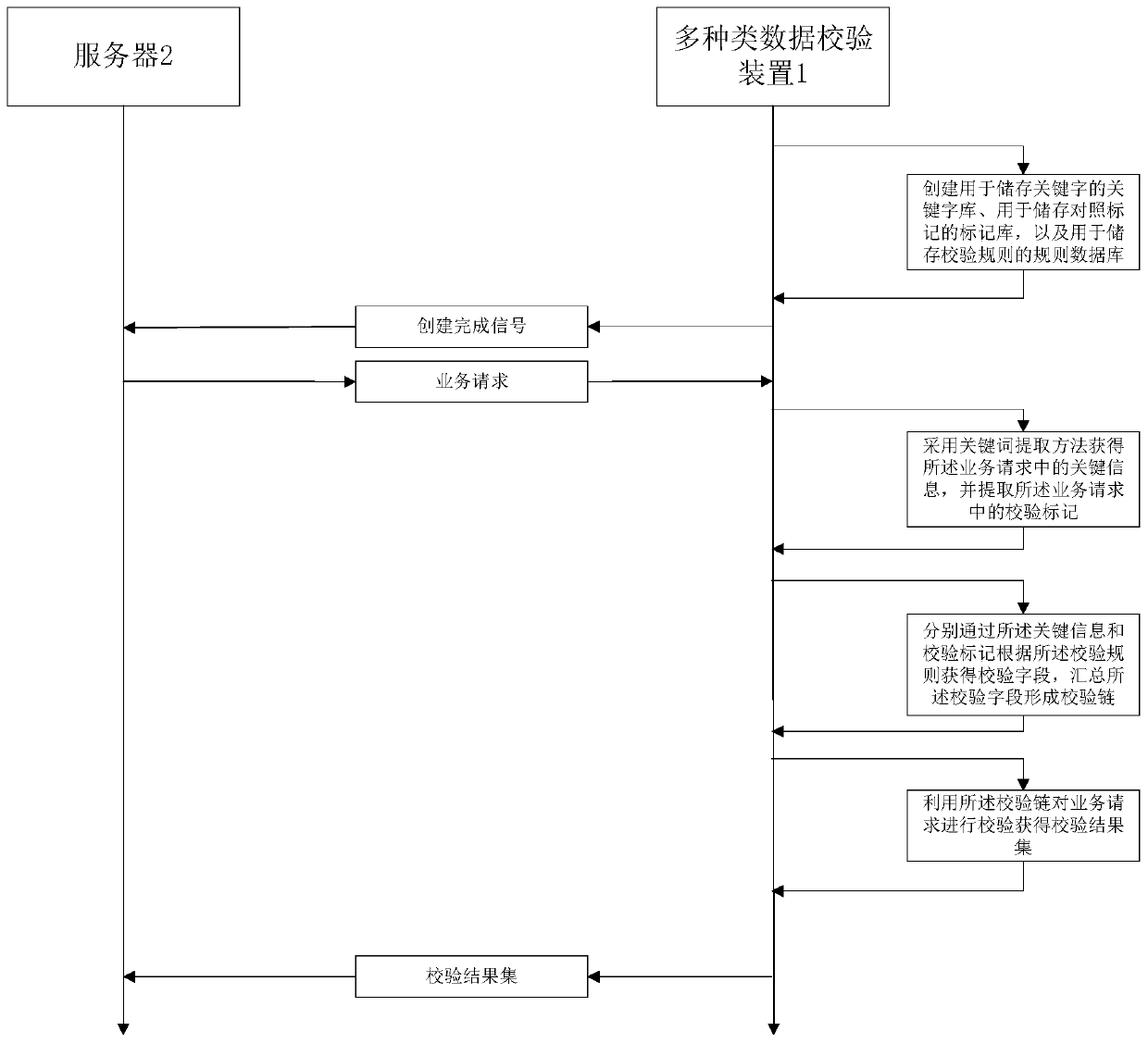
[0052] see figure 1 and figure 2 , a kind of multi-type data verification method of the present embodiment, utilizes multi-type data verification device 1, comprises the following steps:
[0053] S1: Create a keyword library for storing keywords, a tag library for storing comparison tags, and a rule database for storing verification rules in the configuration center of the distributed cluster, and output to the server 2 that the creation is completed signal; the verification rule is used to express the corresponding relationship between the verification field and the keyword or comparison mark; wherein, the creation completion signal is output to the server 2 in the form of a communication signal;
[0054] S2: Receive the service request output by the server 2, use the keyword extraction method to obtain the key information in the service request, and extract the verification mark in the service request; respectively use the key information and the verification mark accordin...
Embodiment 2
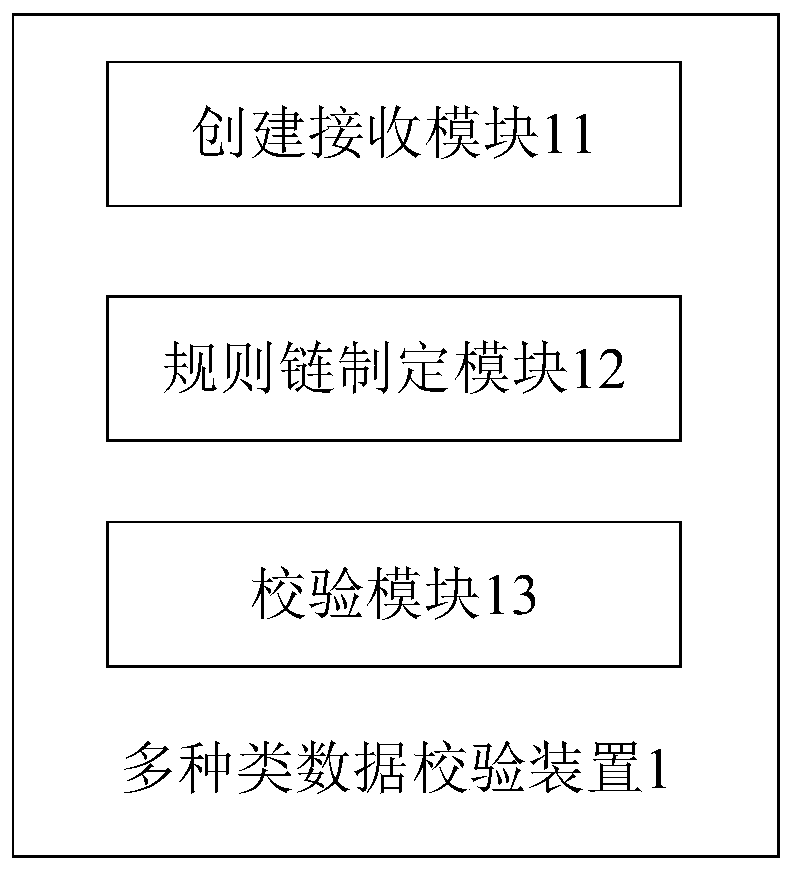
[0137] see image 3 , a multi-type data verification device 1 of the present embodiment, comprising:
[0138] Create a receiving module 11, which is used to create a keyword library for storing keywords, a tag library for storing comparison marks, and a rule database for storing verification rules in the configuration center of the distributed cluster, and send The server 2 outputs a creation completion signal; the verification rule is used to express the corresponding relationship between the verification field and a keyword or a comparison mark; wherein, the creation completion signal is output to the server 2 in the form of a communication signal;
[0139] The rule chain formulating module 12 is used to receive the service request output by the server 2, adopt the keyword extraction method to obtain the key information in the service request, and extract the verification mark in the service request; respectively pass the key information Obtaining the verification field acc...
Embodiment 3
[0143] To achieve the above object, the present invention also provides a computer system, the computer system includes a plurality of computer equipment 3, the components of the multi-category data verification device 1 of embodiment 2 can be dispersed in different computer equipment, and the computer equipment can be It is a smartphone, tablet computer, laptop computer, desktop computer, rack server, blade server, tower server, or rack server (including an independent server, or a server cluster composed of multiple servers) that executes the program. The computer equipment in this embodiment at least includes but is not limited to: a memory 31 and a processor 32 that can communicate with each other through a system bus, such as Figure 4 shown. It should be pointed out that, Figure 4 Only the computer device is shown with the components - but it is understood that implementing all of the illustrated components is not a requirement and that more or fewer components may ins...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com