Unknown threat active defense method and system
An unknown threat, active defense technology, applied in the field of network security, can solve the problem that unknown threats cannot be identified and dealt with
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0022] Since traditional network security solutions are mainly rule-based, known threats can be actively discovered and dealt with. In the prior art, the threat processing engine used for discovery and processing of known threats is mainly based on the rule matching technology for known threats to identify and process known malicious files and known malicious traffic. For unknown threats, existing rules cannot be used to discover and deal with them, and active identification technologies and active defense technologies are needed to deal with them.
[0023] Based on file and traffic deep behavior analysis technology, the present invention actively discovers and processes unknown threats, and provides an active defense method for unknown threats.
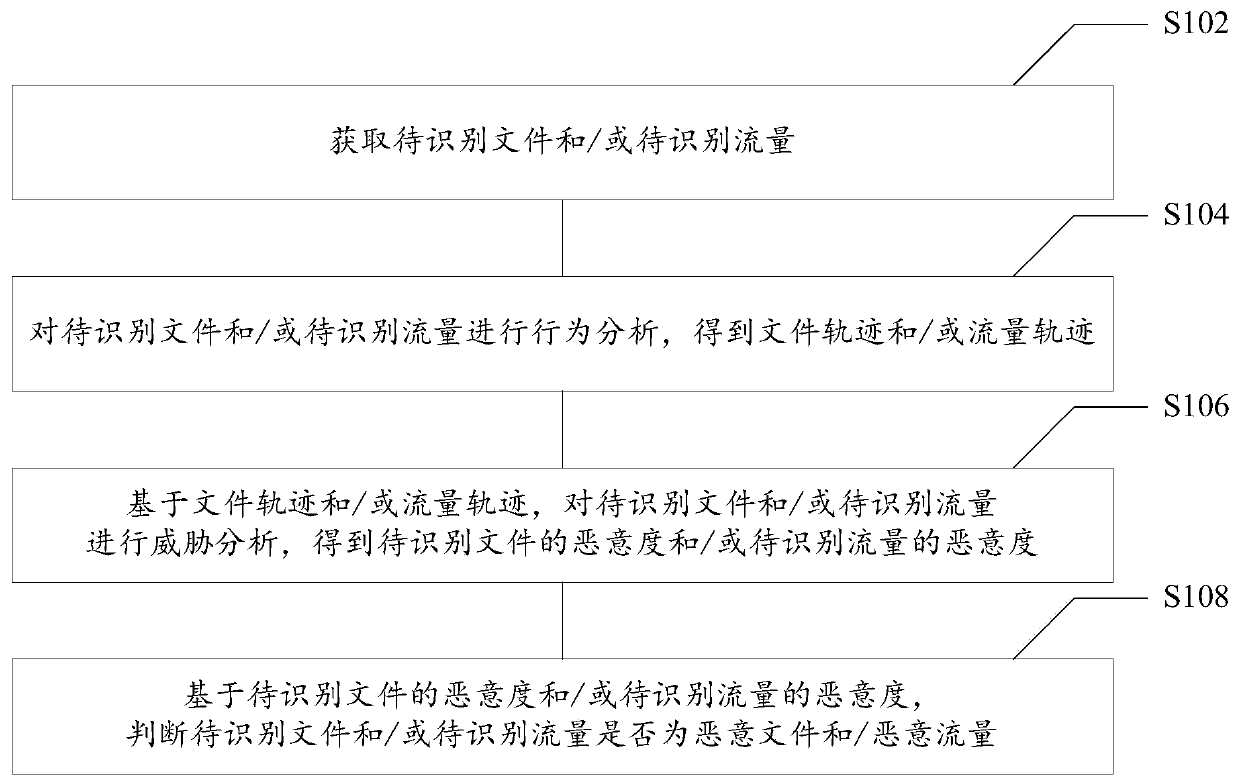
[0024] figure 1 It is a flow chart of an active defense method for unknown threats provided according to an embodiment of the present invention, which is applied to a server. like figure 1 As shown, the method specifically include...
Embodiment 2
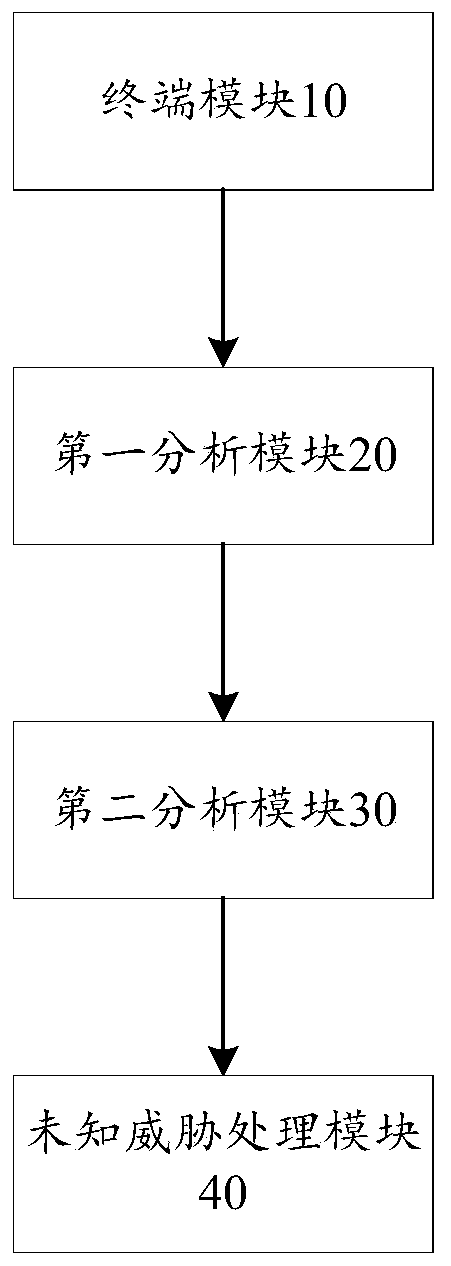
[0098] figure 2 It is a schematic diagram of an unknown threat active defense system provided according to an embodiment of the present invention, which is applied to a server and includes: a terminal module 10 , a first analysis module 20 , a second analysis module 30 and an unknown threat processing module 40 .
[0099] Specifically, the terminal module 10 is configured to acquire files to be identified and / or traffic to be identified.
[0100] The first analysis module 20 is configured to perform behavior analysis on the files to be identified and / or the traffic to be identified, and obtain file traces and / or traffic traces.
[0101] The second analysis module 30 is configured to perform threat analysis on the file to be identified and / or the traffic to be identified based on the file track and / or the traffic track to obtain the malicious degree of the file to be identified and / or the malicious degree of the traffic to be identified.
[0102] The unknown threat processing m...
Embodiment 3
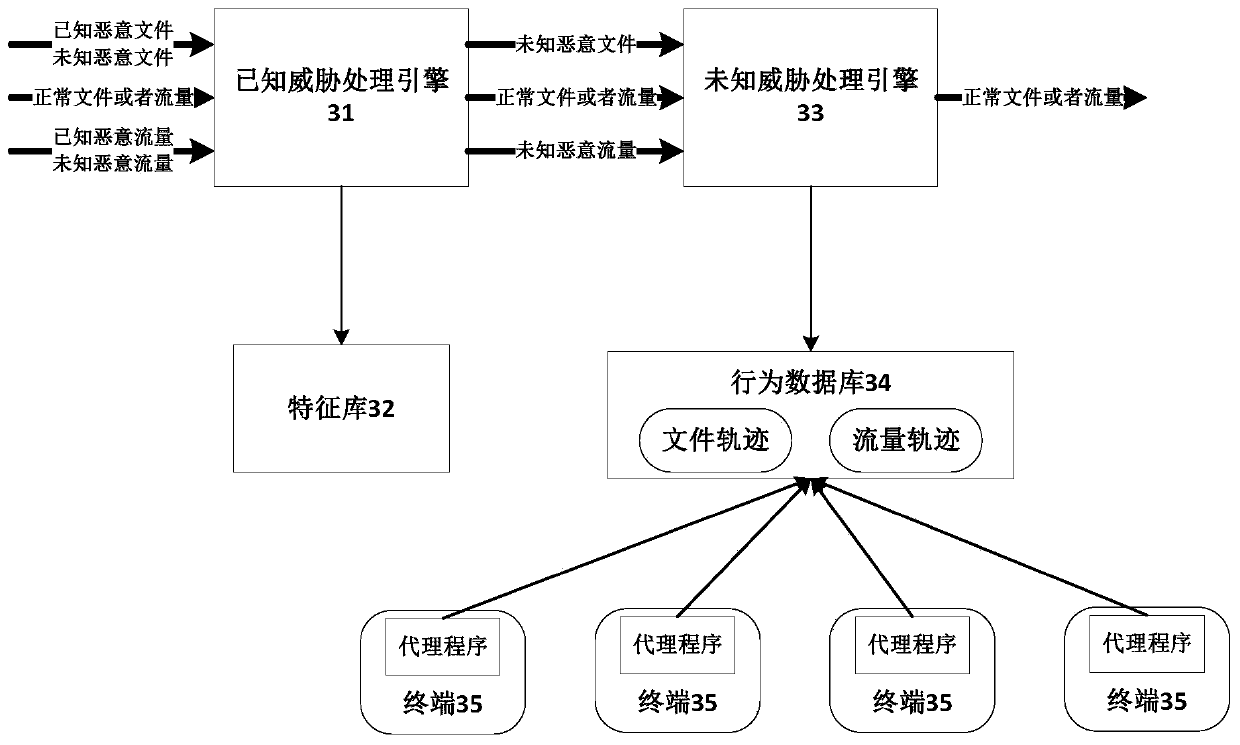
[0117] The embodiment of the present invention also provides another active defense system against unknown threats, such as image 3 As shown, the system includes: a known threat processing engine 31 , a feature library 32 , an unknown threat processing engine 33 , a behavior database 34 and a terminal 35 . Among them, such as image 3 As shown, the number of terminals 35 may be multiple.
[0118] Specifically, the known threat processing engine 31 is configured to: identify and process known malicious files and known malicious traffic.
[0119] Feature storehouse 32 is used for: recording the fingerprint feature (for example can be MD5 value) of known malicious file, is used for file matching to find malicious file; Record the fingerprint feature (for example can be IP mode or domain name mode) of known malicious traffic , used for traffic matching to detect malicious traffic.
[0120] The signature library 32 provides a known threat processing engine to match known threat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com