Implementation method of novel lightweight block cipher CORL
A technology of block ciphers and implementation methods, applied in encryption devices with shift registers/memory, digital transmission systems, electrical components, etc., can solve problems such as complex algorithm decryption process, low encryption performance, and vulnerability to attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
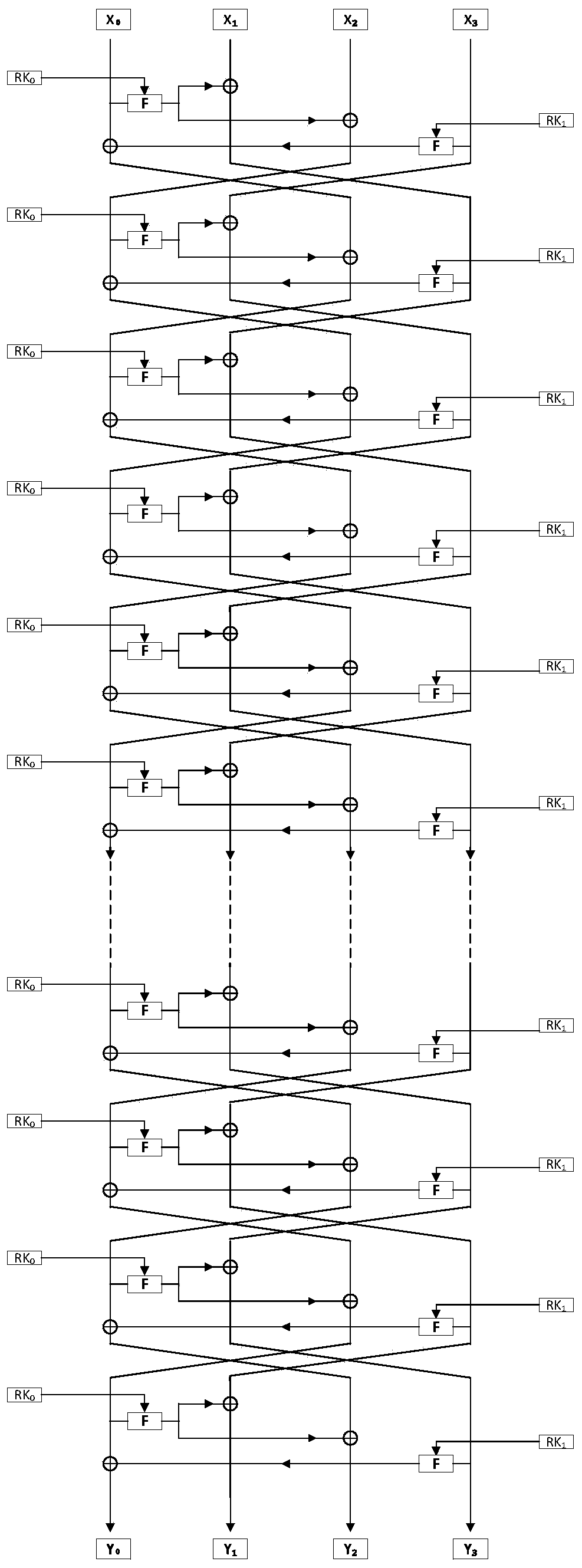
[0059] CORL block cipher implementation method, the block length of the designed cipher algorithm is 64 bits, the key length is 80 bits, and the number of algorithm round iterations is N R It is 22 rounds of operation.
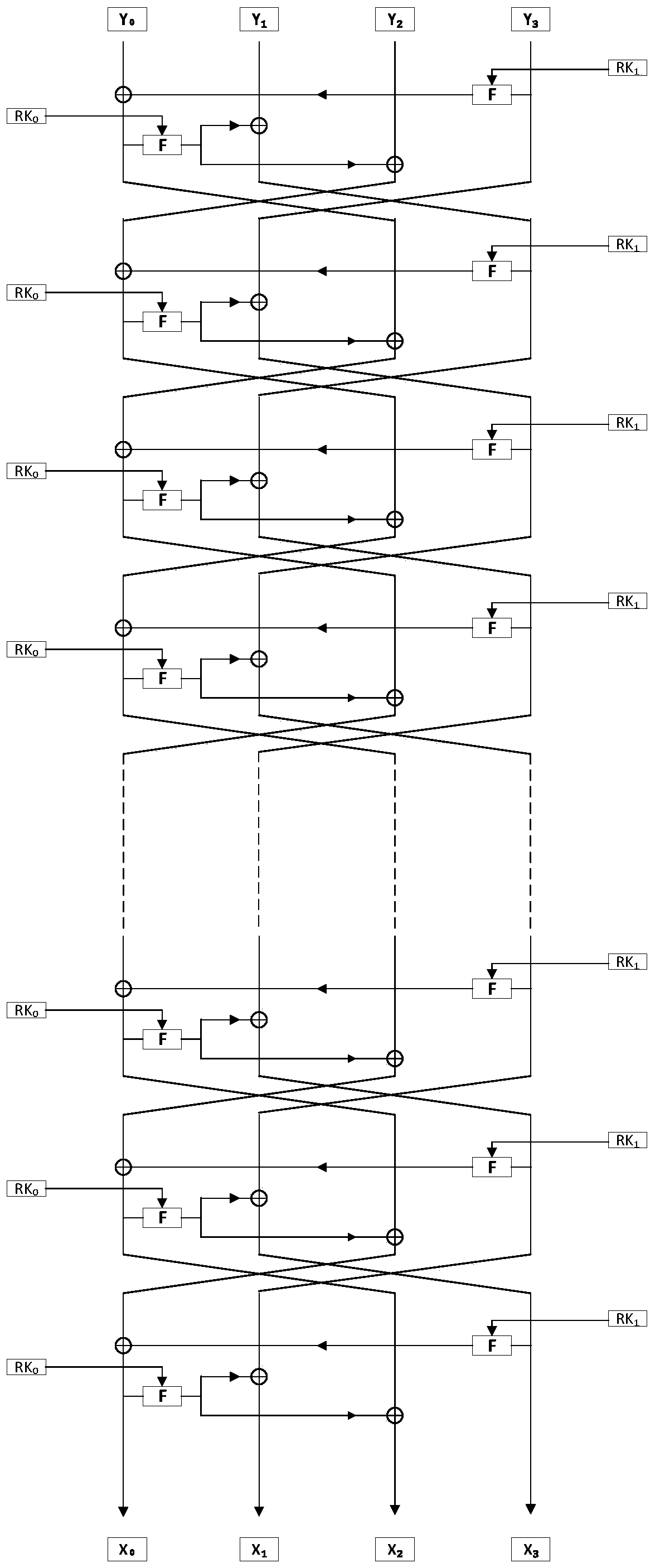
[0060] The encryption structure of the CORL block cipher algorithm is as follows: figure 1 As shown, the decryption structure of the CORL block cipher algorithm is as follows figure 2 shown;
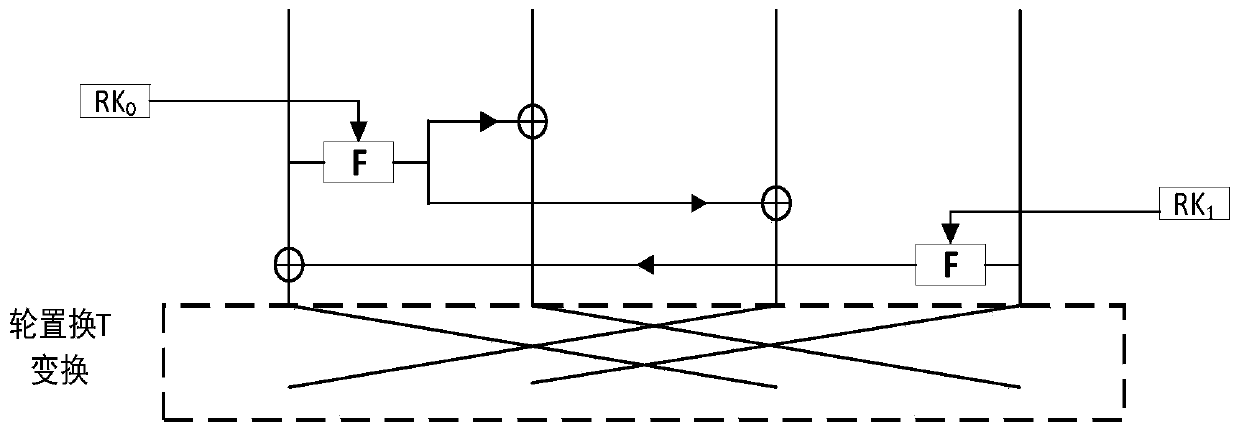
[0061] The round function operation of the algorithm mainly includes F-function transformation (F-Function) and round transposing T transformation (RoundTransposing); but the last round of function operation does not perform round transposing T transformation, see image 3 shown.
[0062] The F function transformation process is row shift transformation (Rowshift)→round key plus transformation (AddRoundKey)→S box replacement transformation (S...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com