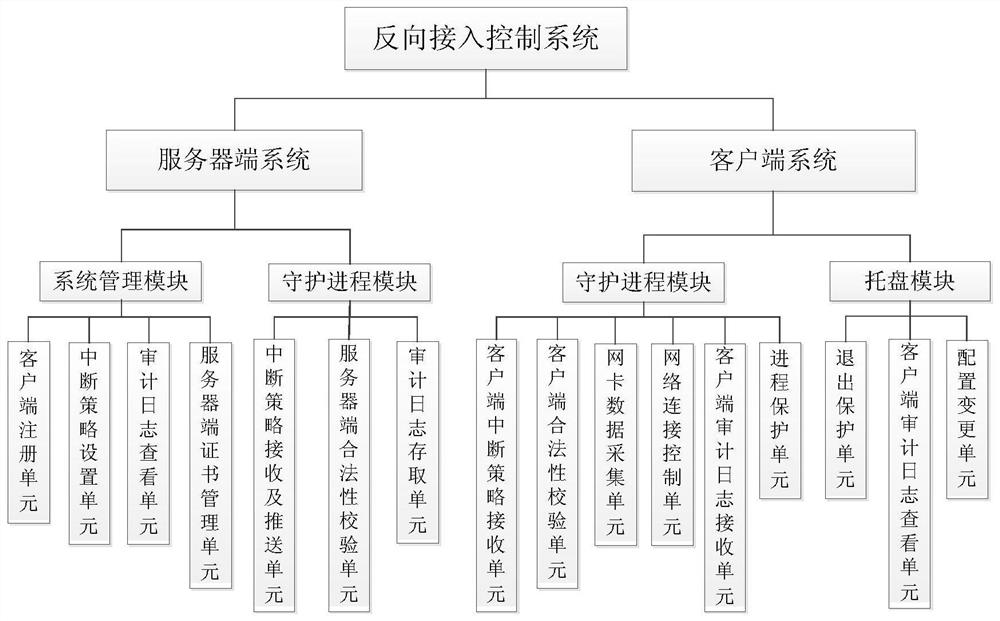
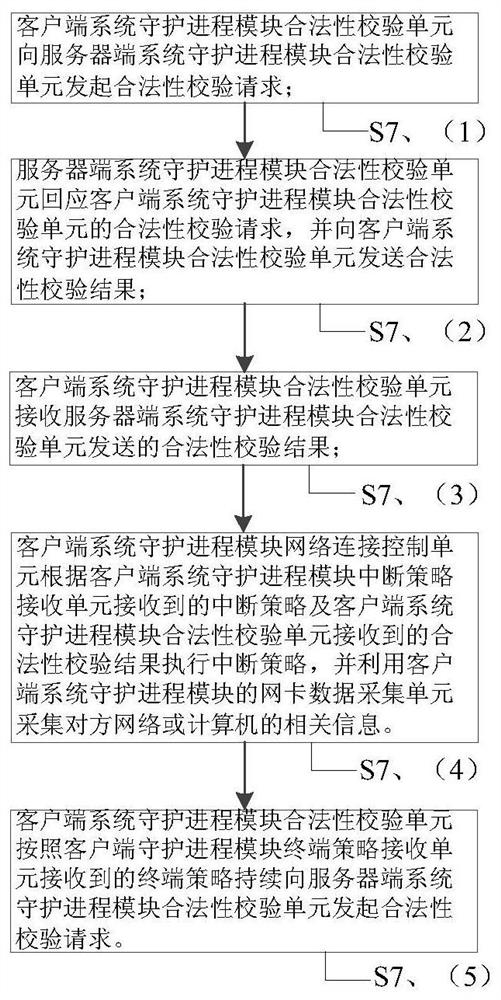
A reverse access control system and method
An access control and reverse technology, applied in transmission systems, digital transmission systems, security communication devices, etc., can solve the problem that network access control technology cannot prevent computer terminals from accessing other networks, and cannot prevent unauthorized devices from connecting to networks. Addressing technology cannot prevent and other problems to achieve the effect of protecting security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
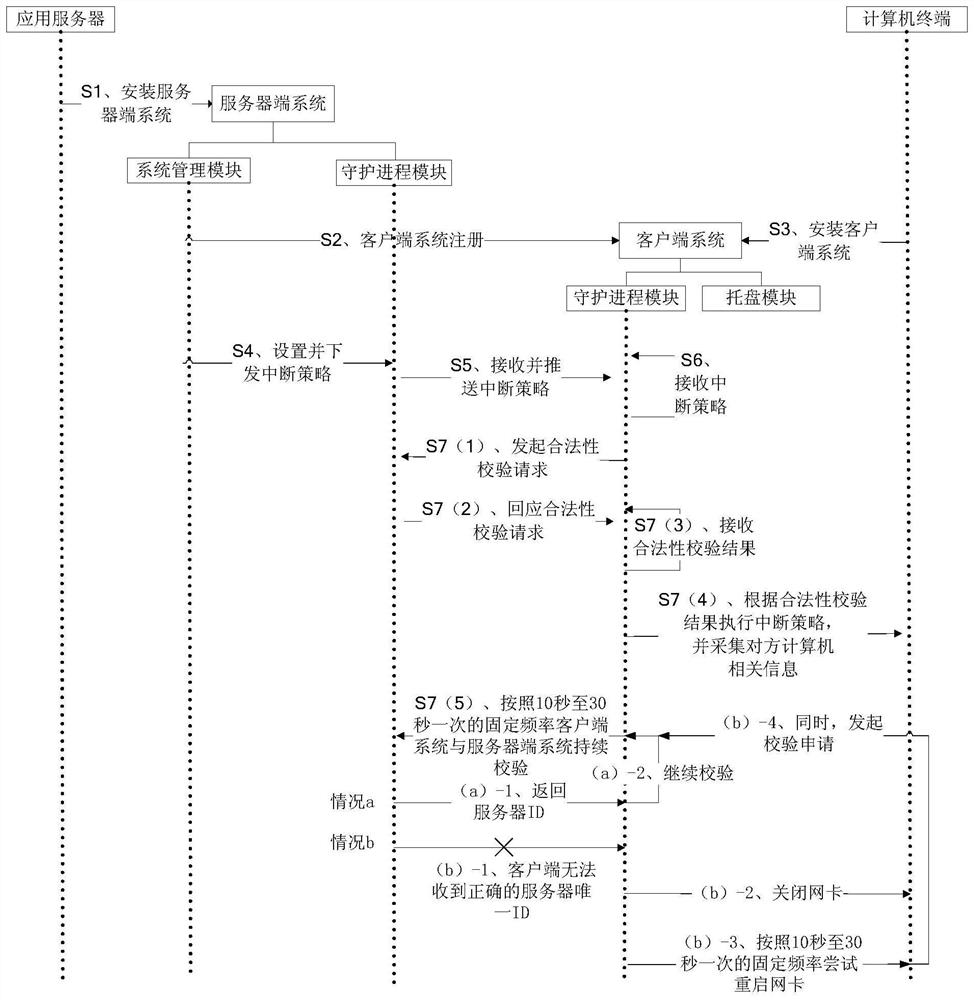
[0090] A reverse access control method, the steps are as follows, such as image 3 shown,
[0091] S1. According to the type of the application server operating system, the application server installs a server-side system;
[0092] S2, the client registration unit extracts the server CPU serial number, generates the server unique ID by encoding, and injects the server unique ID into the installation program of the client system to complete the client system registration;
[0093]S3, the computer terminal installs the client system containing the unique ID of the server, so that the computer terminal becomes the computer terminal in the authorized network;
[0094] S4, the interruption strategy setting unit sets an interruption strategy, and sends interruption strategy information to the interruption strategy receiving and pushing unit;
[0095] The interruption strategy includes the strategy of successful and failed legality verification; if the legality verification is succ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com