Intranet security risk identification method and device
A security risk, intranet technology, applied in the field of communications, can solve problems such as high misjudgment rate, dependence on feature database, etc., to achieve the effect of improving accuracy and facilitating large-scale deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] In order to describe in detail the technical content, structural features, achieved objectives and effects of the technical solution, the following detailed descriptions are given in conjunction with specific embodiments and accompanying drawings.
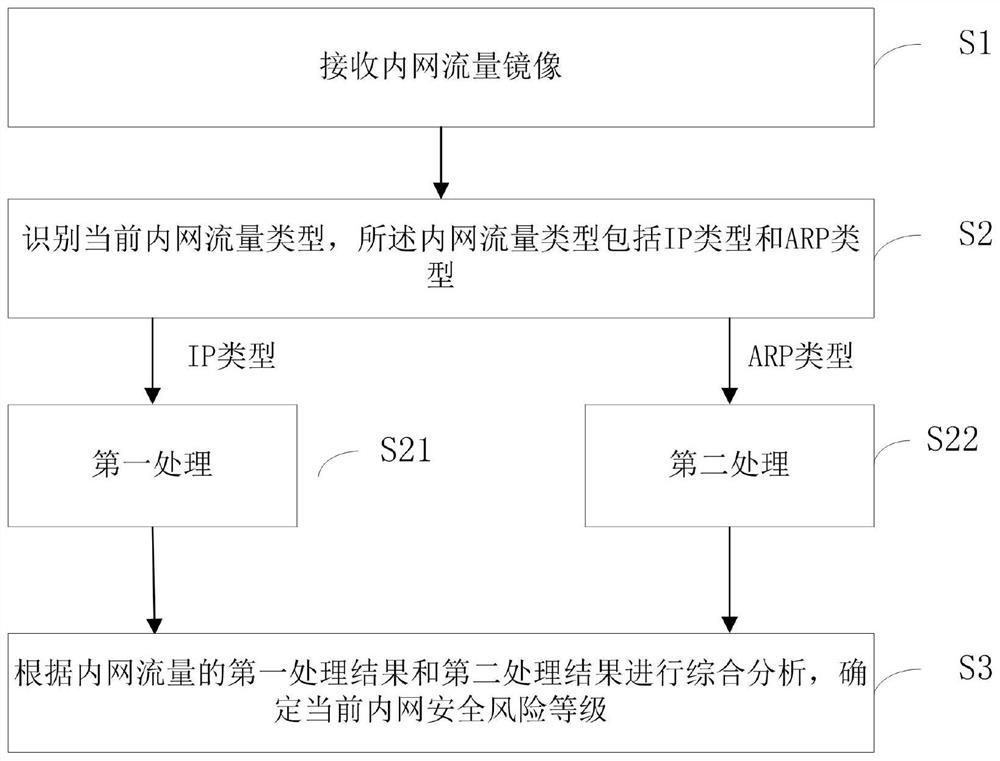
[0035] Such as figure 1 As shown, this application provides a method for identifying an intranet security risk, and the method includes the following steps:
[0036] S1: Receive intranet traffic mirroring.
[0037] Traffic mirroring refers to transferring a copy of traffic data to a designated port to realize real-time monitoring and analysis of intranet traffic.
[0038] S2: Identify the current intranet traffic type. The intranet traffic type includes an IP type and an ARP type. If it is an IP type, perform step S21: first processing, and if it is an ARP type, perform step S22: second processing.
[0039] When the computer is connected to the Internet, the ISP (Internet Service Provider) will automatically assign an IP to each compu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com