Accelerator for accelerating security hash algorithm
A secure hash algorithm and accelerator technology, applied in the field of computer architecture, can solve the problems of serious dependence on instruction data, large number of instructions, high power consumption, etc., achieve good scalability and compatibility, reduce power consumption overhead, The effect of reducing time overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The specific implementation manners of the present invention will be described below in conjunction with the drawings and specific embodiments.
[0038] In view of the problems existing in the prior art, the inventor intends to make improvements in the following aspects.
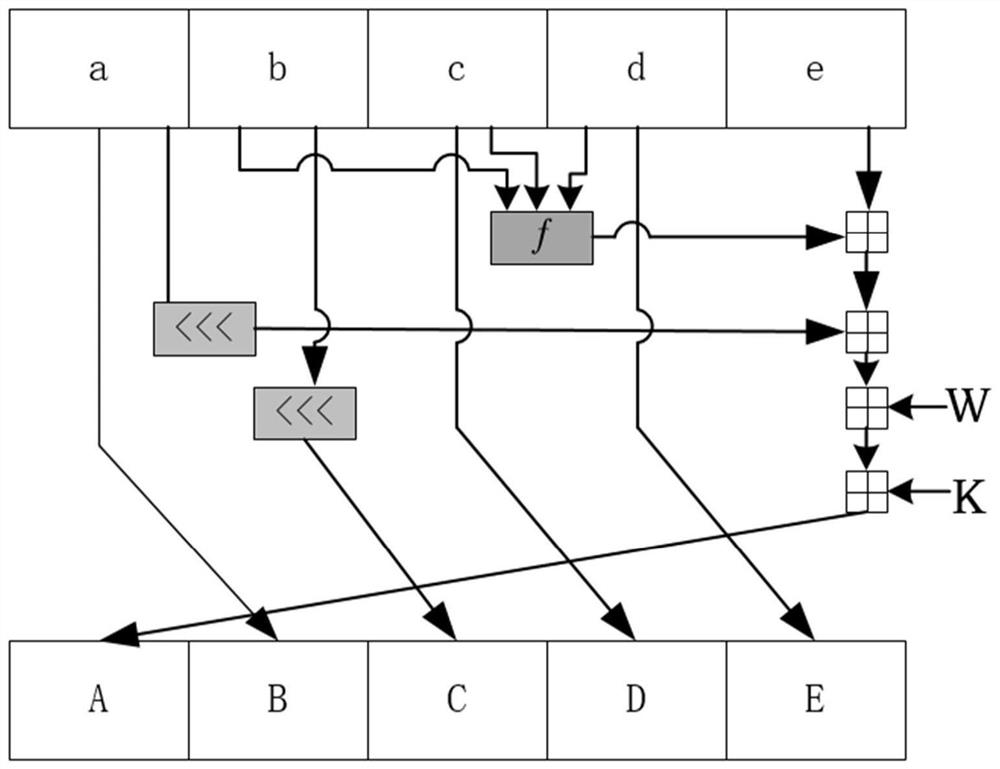
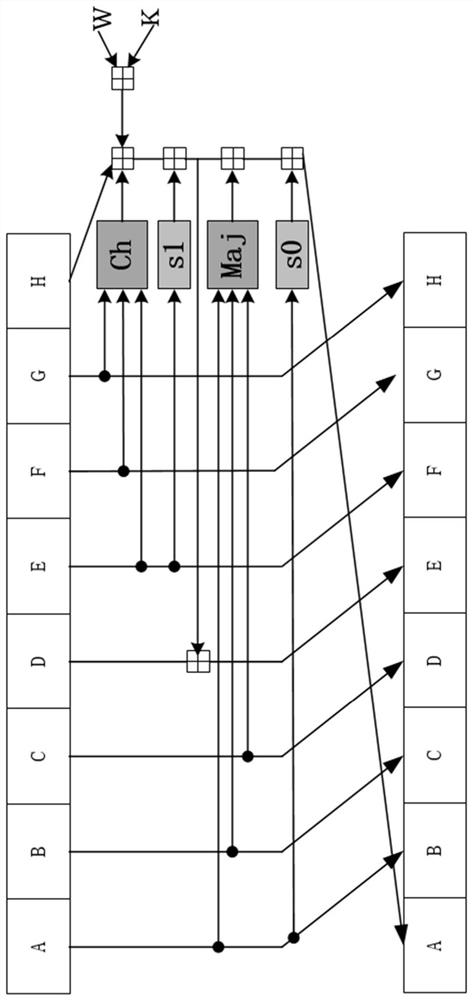
[0039] First, due to the complex operation of the secure hash algorithm itself, the large number of instructions, and the serious data dependence, the effect of optimization is not obvious only through software technologies such as compilation optimization; Although the acceleration of the column algorithm can bring obvious acceleration effects, the special circuit structure is difficult to apply to other secure hash algorithms, and the scalability and compatibility are poor. The inventor believes that only through a complete set of software and hardware cooperating system can the secure hash function be accelerated efficiently.
[0040] Second, the existing method for accelerating the secure hash al...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com