Identity authentication method and system based on EAP-MD5 improved protocol
An EAP-MD5 and identity authentication technology, which is applied in the field of identity authentication methods and systems based on the EAP-MD5 improved protocol, can solve problems such as replay attacks, deciphering, and EAP-MD5 not recommended to use, etc., to reduce violence The probability of cracking, prevention of replay attacks, and the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
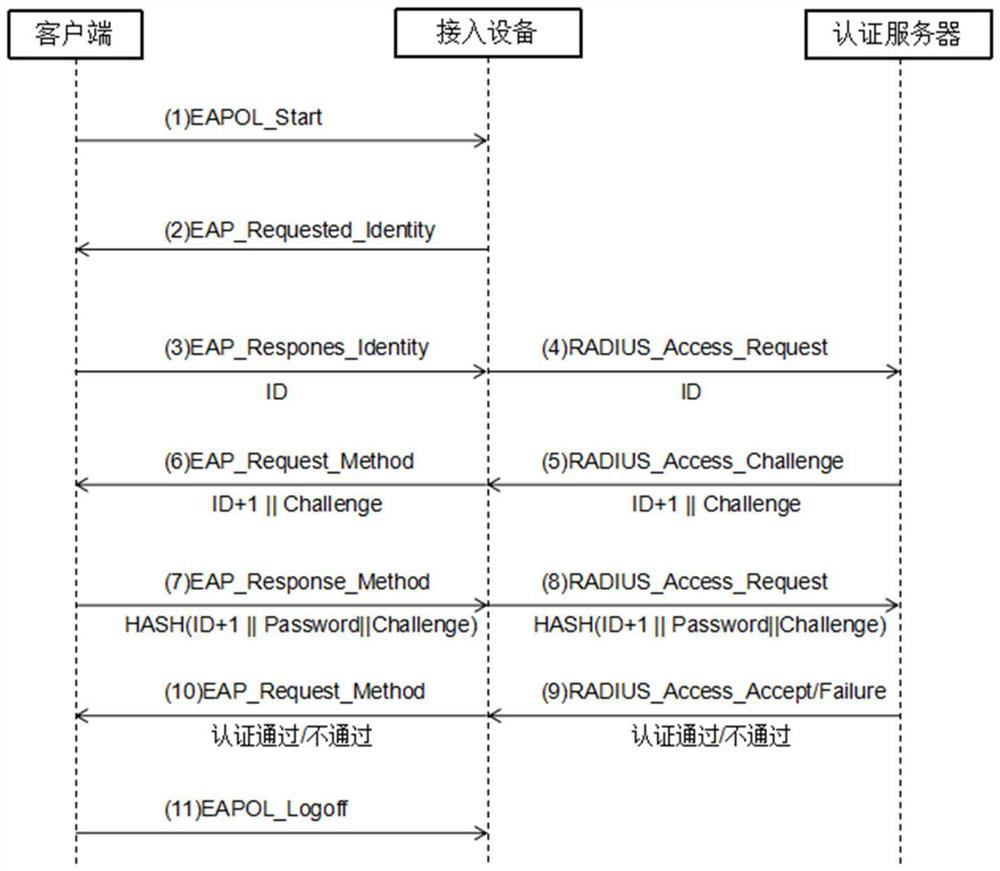
[0027] refer to figure 1 , the traditional EAP-MD5 protocol identity authentication process is as follows:
[0028] (1) The client sends an EAPOL_Start message to the access device to start 802.1x authentication access;
[0029] (2) The access device sends an EAP_Request_Identity message to the client, requiring the client to send the user name (ie user ID) to the access device;
[0030] (3) The client responds with an EAP_Response / Identity request to the access device, including the user ID;
[0031] (4) The access device encapsulates the user name in the EAP_Response_Identity message into the RADIUS_Access_Request message and sends it to the authentication server;
[0032] (5) The authentication server judges whether the user name belongs to a registered legal user name, if not, access is not allowed; if yes, the authentication server generates a Challenge, and the user name ID+1, and the Challenge and ID+1 Return to the access device through the RADIUS_Access_Challenge m...
Embodiment 2
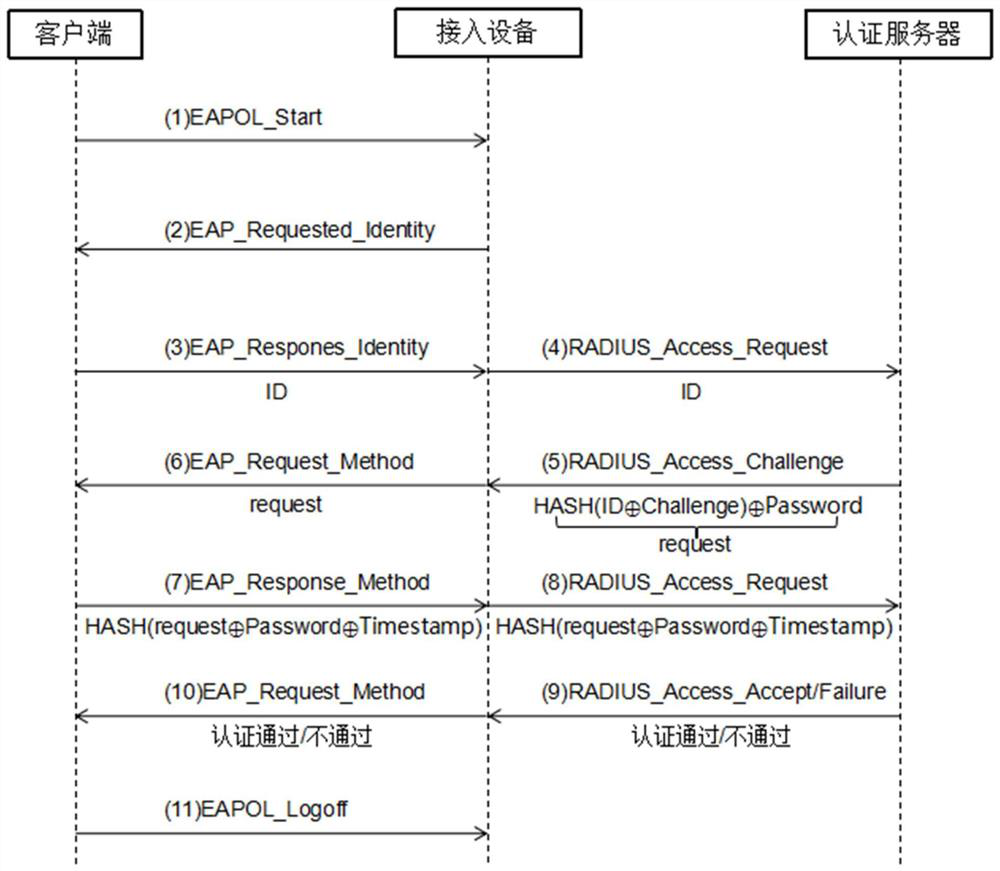
[0055] The present invention also provides an identity authentication system based on the improved EAP-MD5 protocol, including a client, an access device, and an authentication server, and the client, the access device, and the authentication server all include a processor, a memory, and a device stored in the A computer program in the memory and running on the processor, when the processor executes the computer program, implements the steps in the above method embodiment of Embodiment 1 of the present invention.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com