APT attack identification and affiliation method and system based on homology analysis, and storage medium
A technology of homology analysis and attack identification, applied in systems and storage media, in the field of APT attack identification and attribution methods based on homology analysis, can solve the problems of difficulty in feature extraction, method failure, single static features, etc. Automatic identification efficiency, simple calculation process, and the effect of improving automation efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
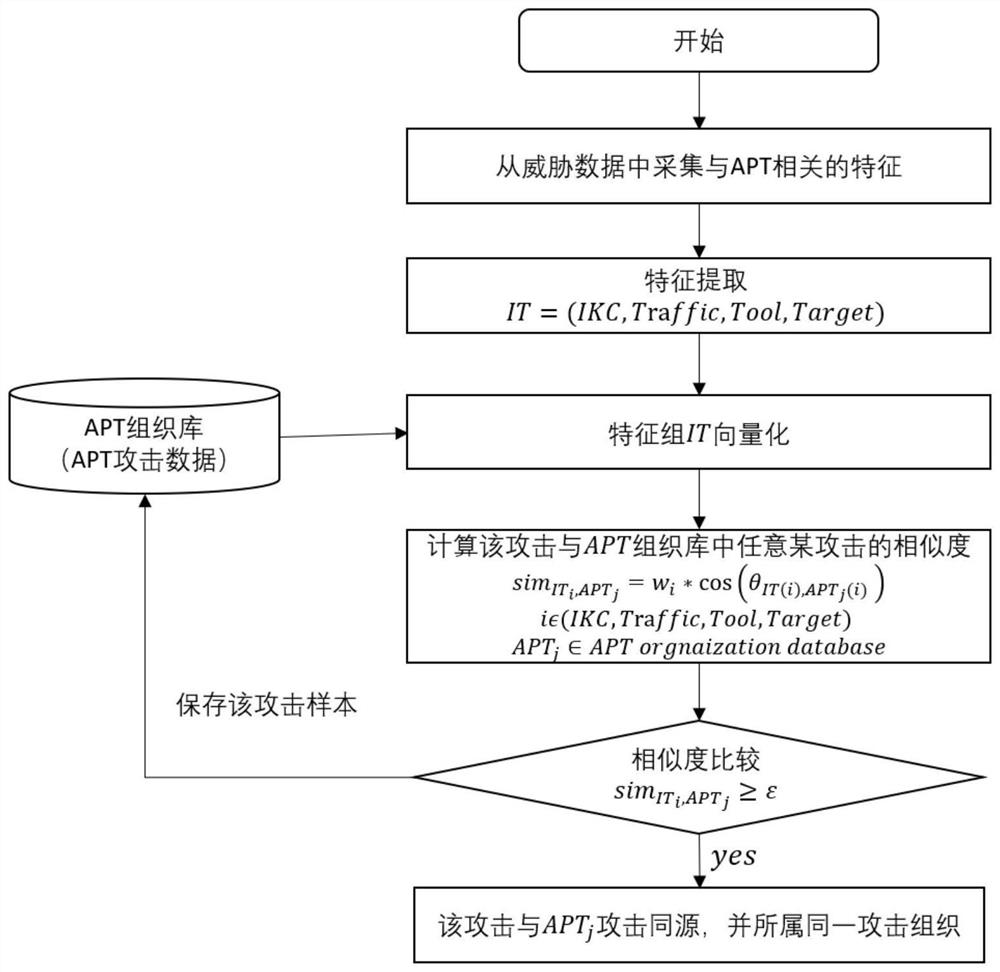
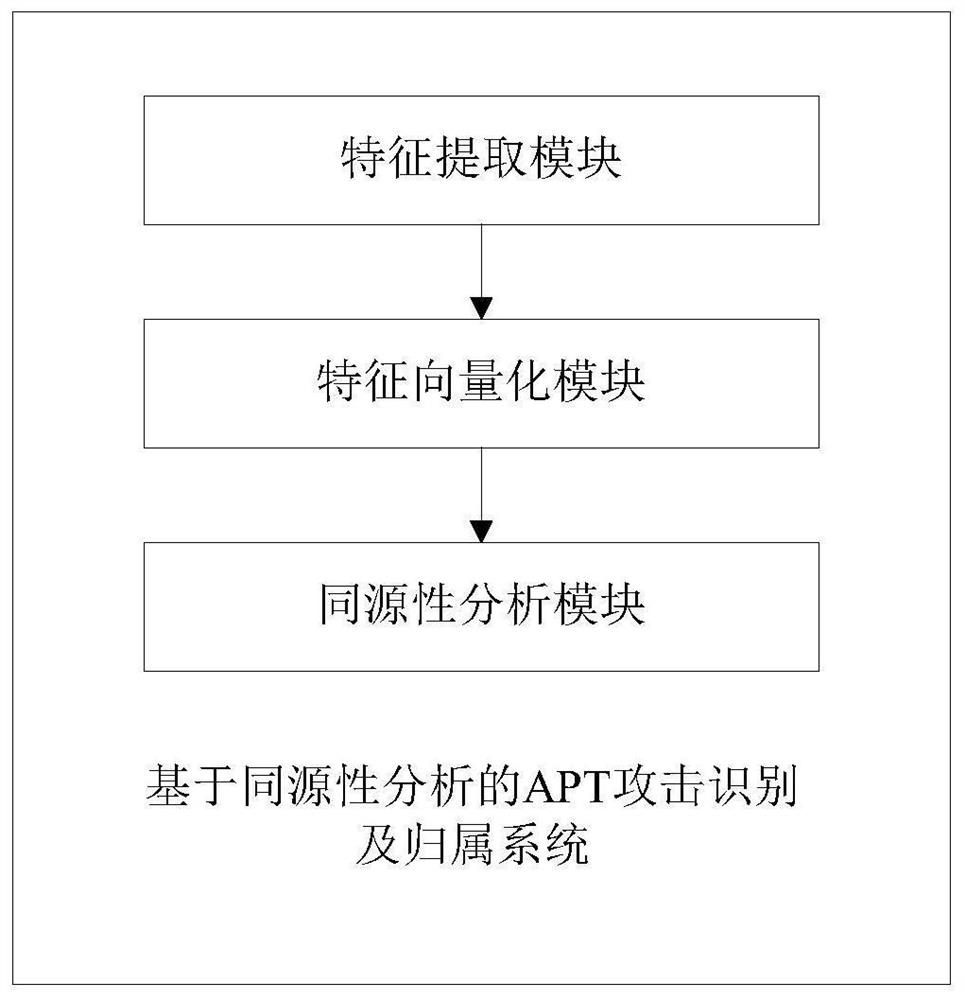
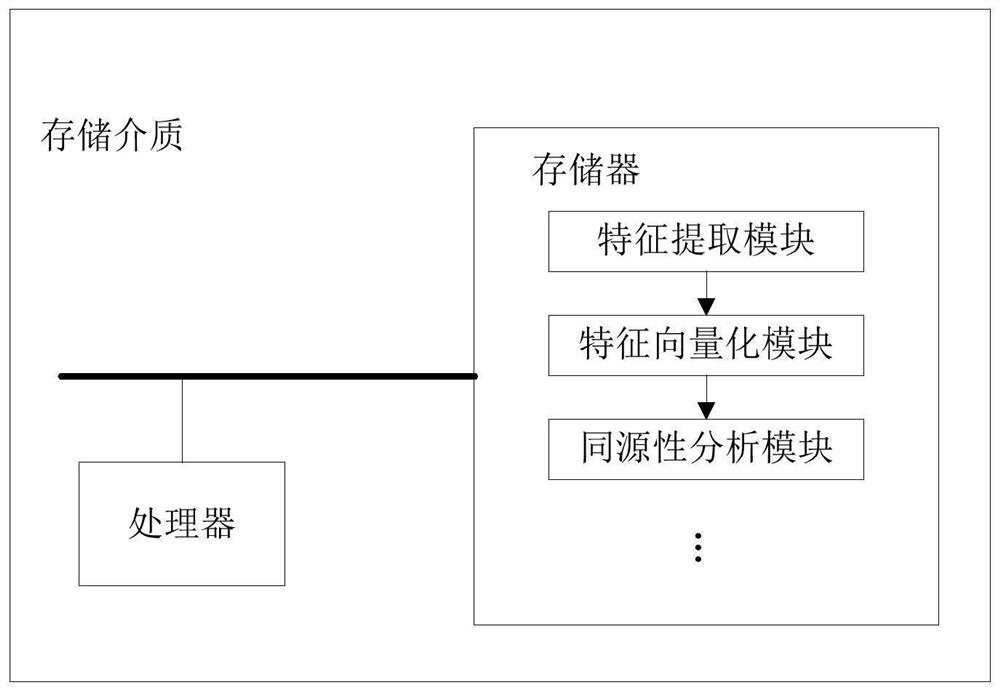
[0048] This embodiment is based on the APT attack identification and attribution method based on homology analysis. First, collect APT-related attack data from a large amount of monitored threat data and extract the characteristic element values in each set in the defined APT quadruple characteristic group; secondly , perform feature vectorization with the APT attack feature tuple in any existing APT organization database; finally, calculate the similarity of the feature vectors of the two groups of attacks, find the relationship between the attack and the selected APT and the organization it belongs to, and Save the attack sample to the APT organization library.
[0049] Such as figure 1 As shown, the method of this embodiment specifically includes the following steps:
[0050] S1. Collect APT-related attack data from the monitored threat data, and extract feature element values in each set of the defined APT quadruple feature group.
[0051] More specifically, in step ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com