Network threat detection system based on auto-encoder integration
An autoencoder and threat detection technology, which is applied in the field of network threat detection based on autoencoder integration, can solve the problems of unsatisfactory detection effects of unknown threats, achieve the effect of enhancing generalization performance, simple implementation method, and flexible means
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be described in detail below according to the accompanying drawings.
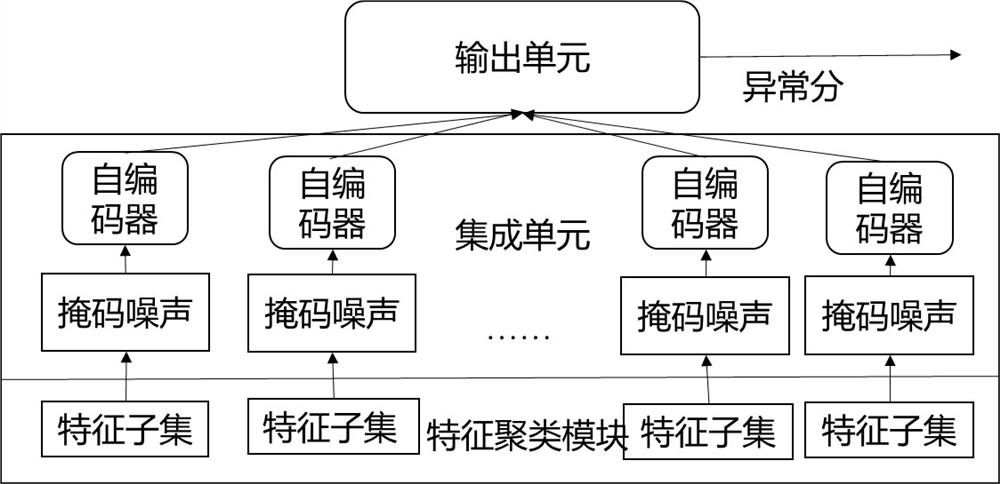
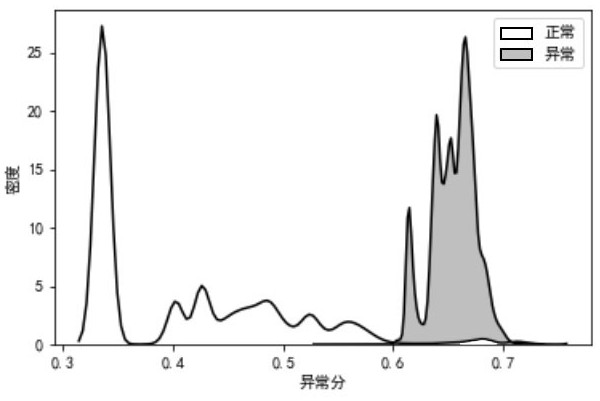
[0035] like figure 1 As shown, the present invention is based on a network threat detection system integrated with an autoencoder, including a network data acquisition module, a feature extraction module, a feature clustering module, and a threat detection module; when the system detects, it specifically includes the following steps:
[0036] Step 1: The network traffic data is saved in the form of a PCAP file through the network data acquisition module.
[0037] Step 2: The feature extraction module performs feature extraction on each session in the original network traffic data, and performs data cleaning and normalization processing; specifically, use the feature extraction module to convert each session in the original network traffic data into five-element Groups are indexed in feature vector form containing 51 features. Wherein, the five-tuple includes source IP ad...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com