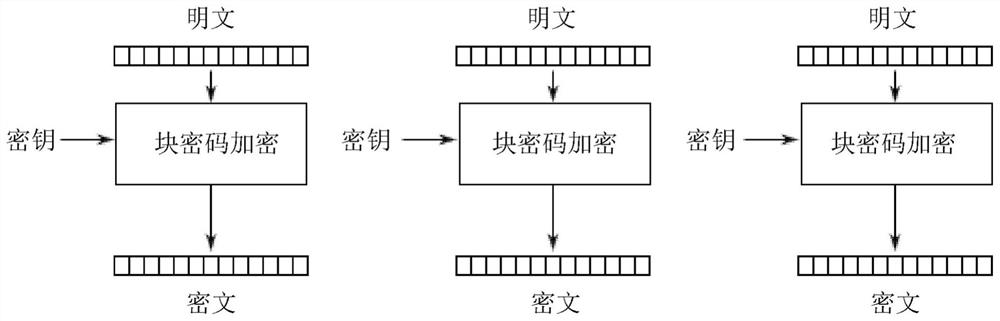
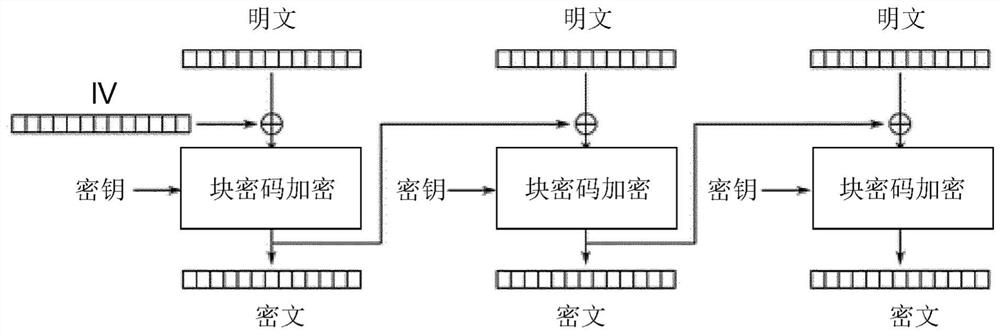
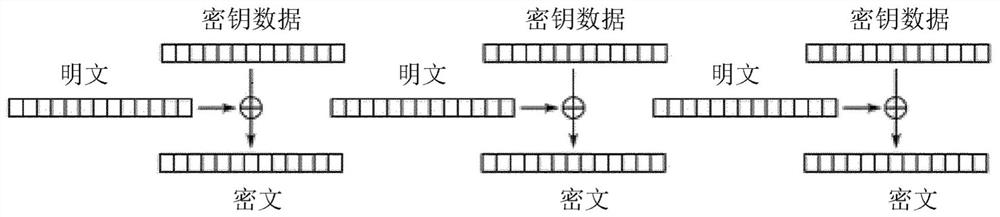
Memory-efficient hardware cryptographic engine
A hardware encryption and memory technology, applied in encryption devices with shift registers/memory, instruments, internal/peripheral computer component protection, etc., can solve the problems of large area and complex integrated circuit occupation, and achieve less memory and less occupation. The effect of less space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] Figure 4 A wireless temperature sensor 1 is shown containing an integrated radio chip 2 , a battery 3 and a thermometer 4 . The temperature sensor 1 also contains other components, such as PCB, oscillator, capacitors, resistors, etc., which are omitted here for simplicity. The radio chip 2 includes a processor 5, memory 6 (which may include volatile and non-volatile memory types), an LTE Cat-M1 (LTE-M) radio 7, a hardware SNOW-3G cryptographic engine 8 (embodied as described above A disclosed hardware encryption engine) and an input / output peripheral 9 such as a USB interface. Of course, the radio chip may have other integrated peripherals and components. Processor 5 , memory 6 and peripherals 7 , 8 , 9 are connected to a memory bus 10 . The memory bus 10 can be an Arm TM AMBA bus system, including one or more Advanced High Performance Bus (AHB) and Advanced Peripheral Bus (APB). Memory bus 10 supports direct memory access (DMA) to memory 6 . The temperature sen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com