A Filtering Method for Real-time Intrusion Detection System
A technology of intrusion detection system and filtering method, applied in transmission systems, electrical components, etc., can solve problems such as difficulty in ensuring real-time detection and accuracy at the same time, inability to accurately intercept, and inability to quickly detect and access users.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The present invention is described in further detail now in conjunction with accompanying drawing.
[0049] It should be noted that terms such as "upper", "lower", "left", "right", "front", and "rear" quoted in the invention are only for clarity of description, not for Limiting the practicable scope of the present invention, and changes or adjustments in their relative relationships, without substantial changes in the technical content, shall also be regarded as the practicable scope of the present invention.
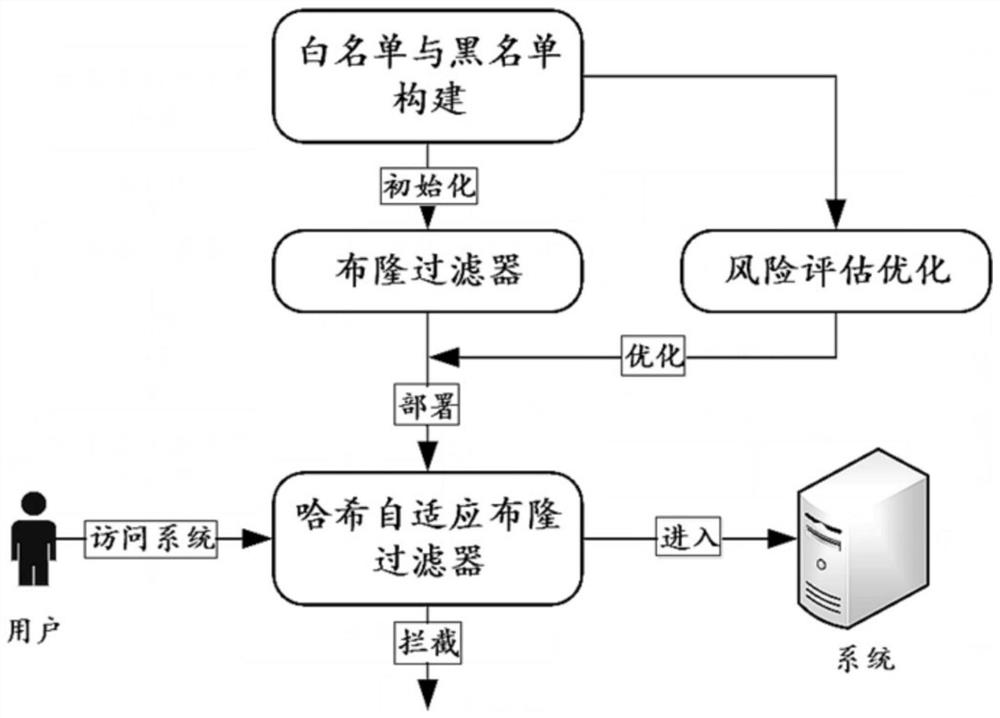
[0050] The present invention mentions a kind of filtering method for real-time intrusion detection system, and described filtering method comprises the following steps:
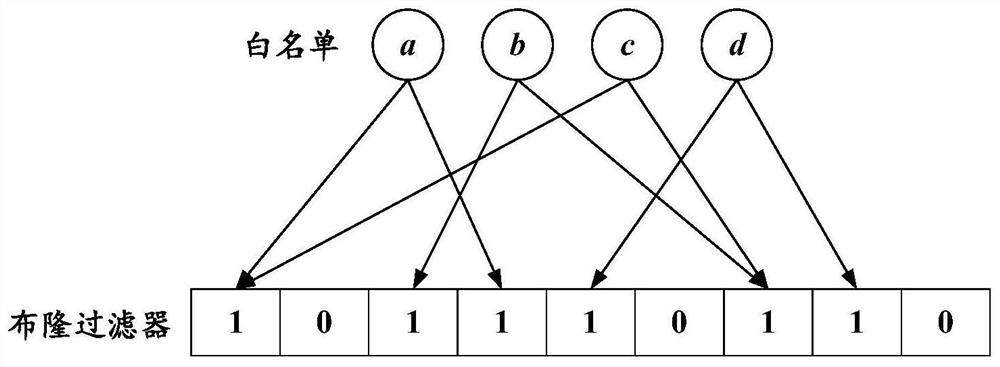
[0051] S1, construction of whitelist and blacklist: collect the user lists corresponding to the detection system that are allowed to enter the system and those that are prohibited from entering the system, and define them as whitelist users and blacklist users respectively.
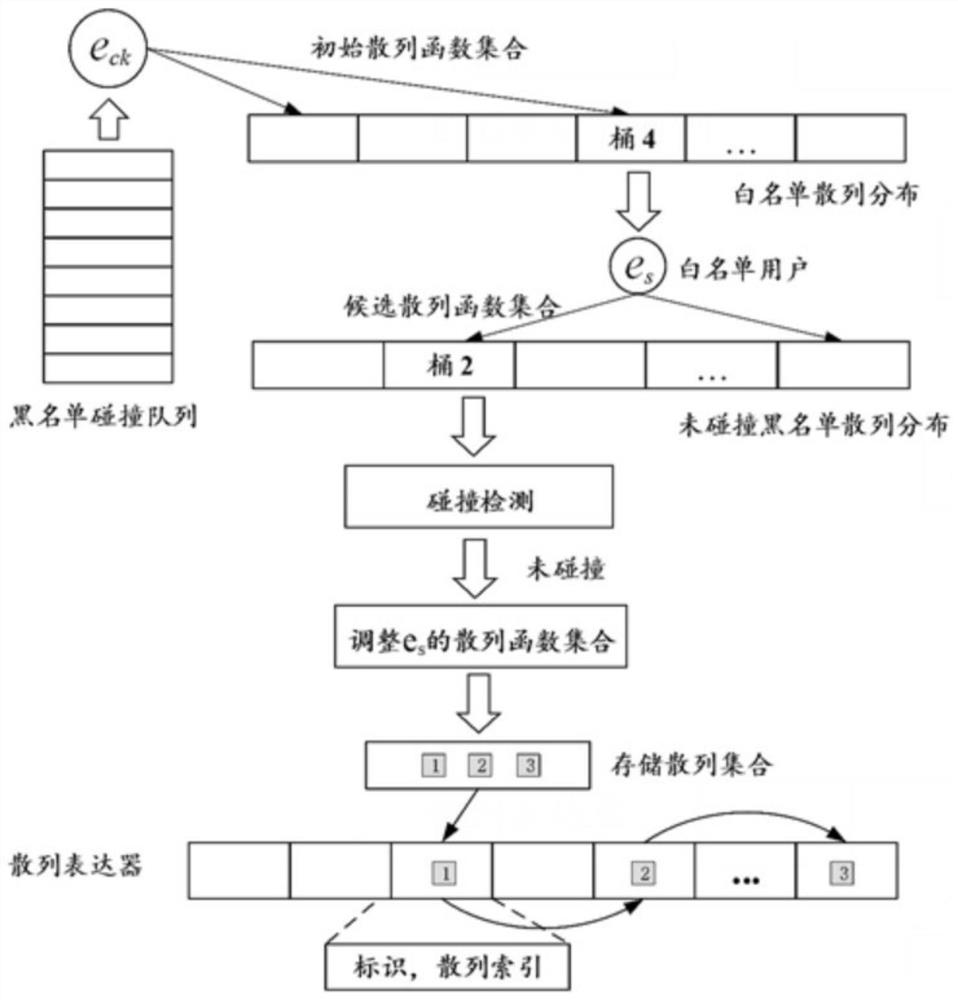
[0052] S2, risk loss...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com