Low-cost Internet-of-Things security protection method and terminal equipment
An IoT network and security protection technology, applied in the field of network information security, can solve the problems of unguaranteed wireless public network transmission security, small capacity of distributed photovoltaic power plants, and network architecture security vulnerabilities.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
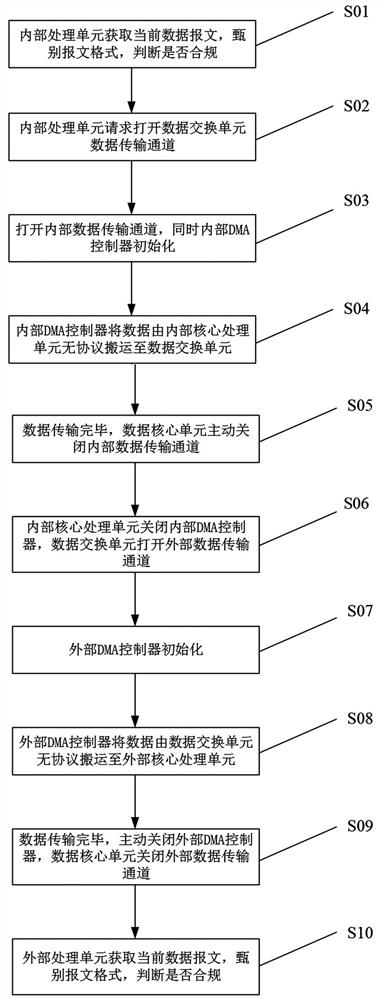
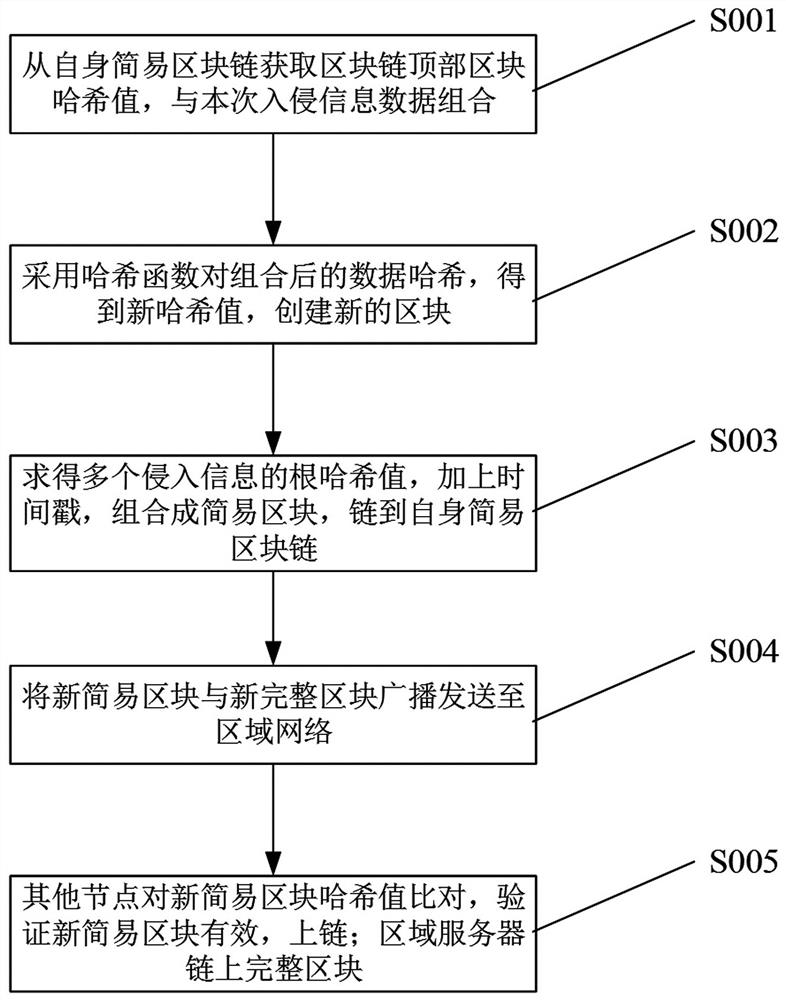
[0034] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
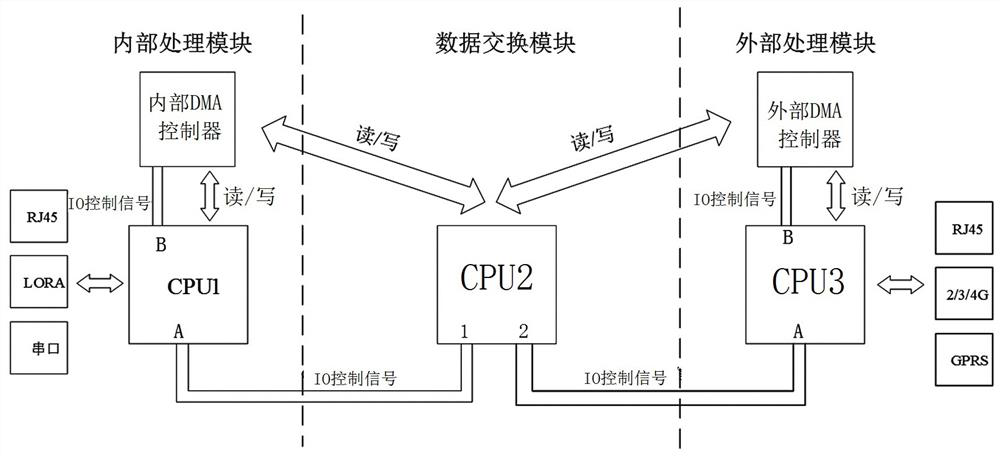
[0035] An embodiment of a miniature terminal device, such as figure 1 :
[0036] Among them, the CPU chip adopts the MPC8313 chip of Freescale PowerPC architecture, the DMA chip adopts the 8237 of Intel Corporation, the Ethernet control (PHY) chip adopts the DP83640 of Texas Instruments (Texas Instruments), and the RJ45 network connector Using TE-8P8C from TE Connectivity. How they are connected is:
[0037] Two I / O interfaces (hereinafter referred to as I / O interface 1 and I / O interface 2 for short) and two TTL ports are constructed by CPU2 of the data exchange module, and these two TTL ports are referred to as TTL1 and TTL2 later. Among them, the I / O interface 1 is connected to the CPU1 of the internal processing module through the internal bus, and the I / O interface 2 is connected to the CPU3 of the external processing module to transmi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com