Malicious traffic detection method based on image analysis, terminal equipment and storage medium
A malicious traffic and image analysis technology, applied in image analysis, image enhancement, image data processing, etc., can solve problems such as inapplicability to complex network environments, relying on the integrity of expert knowledge bases, and low false positive rate, to improve detection performance, avoid linear growth, avoid the effect of manual maintenance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
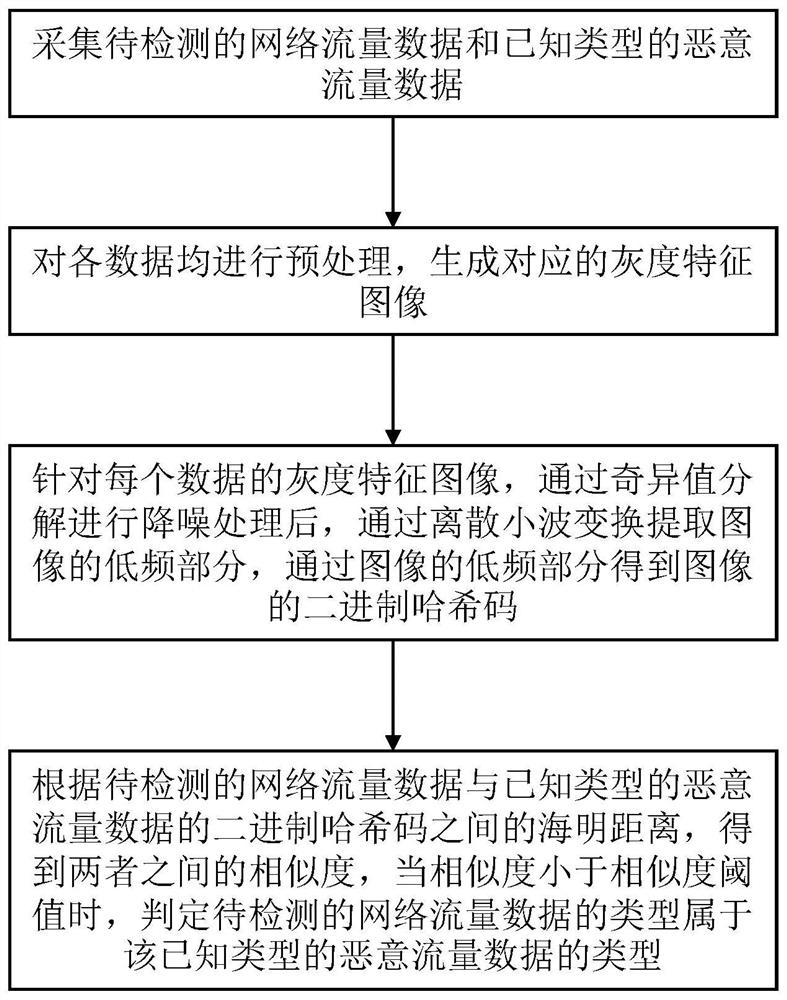
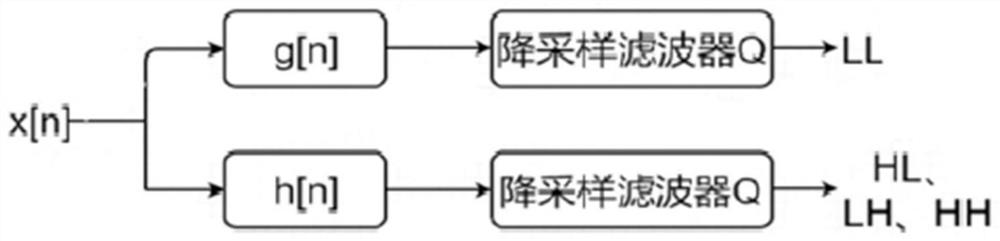
[0034] The embodiment of the present invention provides a method of malicious flow detection based on image analysis, such as figure 1 As shown, the method includes the following steps:
[0035] S1: Collect the network traffic data to be detected and the malicious flow data of known types.
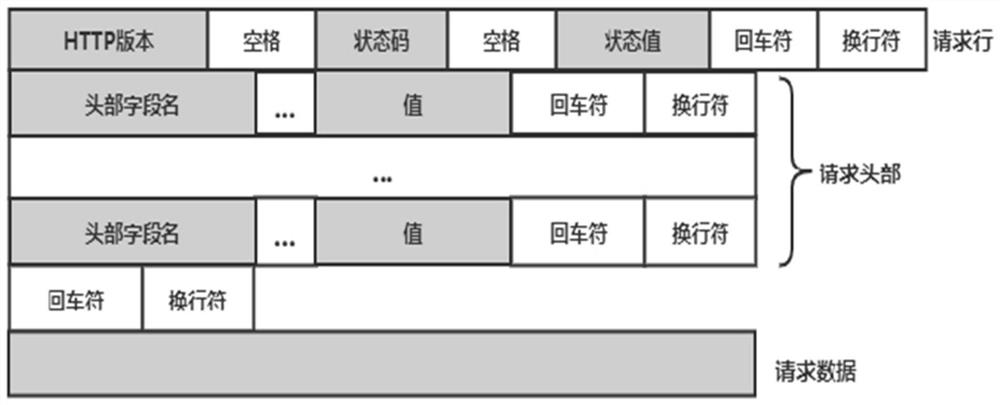
[0036] Network traffic data is generated based on unified HTTP protocols, with structured features, and relatively fixed attribute relationships between fields in the data. According to the data format of network traffic data, its data format is like figure 2 Indicated.
[0037] The structure of network traffic data is divided into four sections: request line, request header, blast, and request data (Request Data). The request line includes: request method, URL (including parameter information), protocol version, etc. The request method includes the following 8 items:
[0038] (1) GET: Requests the resource identified by the Request-URI, which is acquired from the server side.
[0039] (2) POS...
Embodiment 2
[0114] The present invention also provides a malicious flow detecting terminal device based on image analysis, including a memory, a processor, and a computer program stored in the memory and can run on the processor, the processor executes the computer program. The steps in the above method embodiment of the embodiment of the present invention are realized.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com