Network security knowledge graph generation method based on threat intelligence
A network security and knowledge map technology, applied in the field of industrial control network security, can solve the problems of low quality network security knowledge map, high data quality requirements, wrong prediction of network attack behavior, etc., to reduce the false positive rate and improve the overall data The effect of improving quality, improving accuracy and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
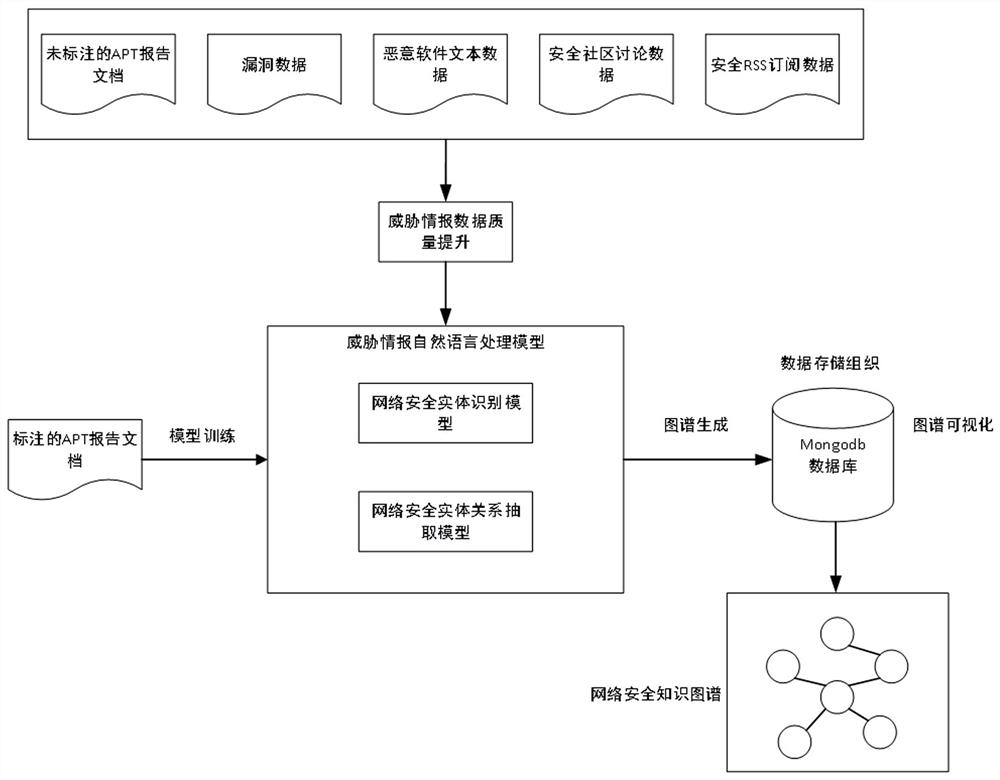
[0101] The present invention is a method for generating network security knowledge map based on threat intelligence, such as figure 1 as shown, figure 1 is a process diagram of the threat intelligence-based network security knowledge map generation method of the present invention. The specific generation process of the network security knowledge map of the present invention includes the following steps: high-efficiency distributed threat intelligence data collection, network security data set production, network security threat intelligence data quality improvement, network security entity identification, network security entity relationship extraction and data organization . The steps are described in detail below:
[0102] Step 1. Efficient distributed threat intelligence data collection.
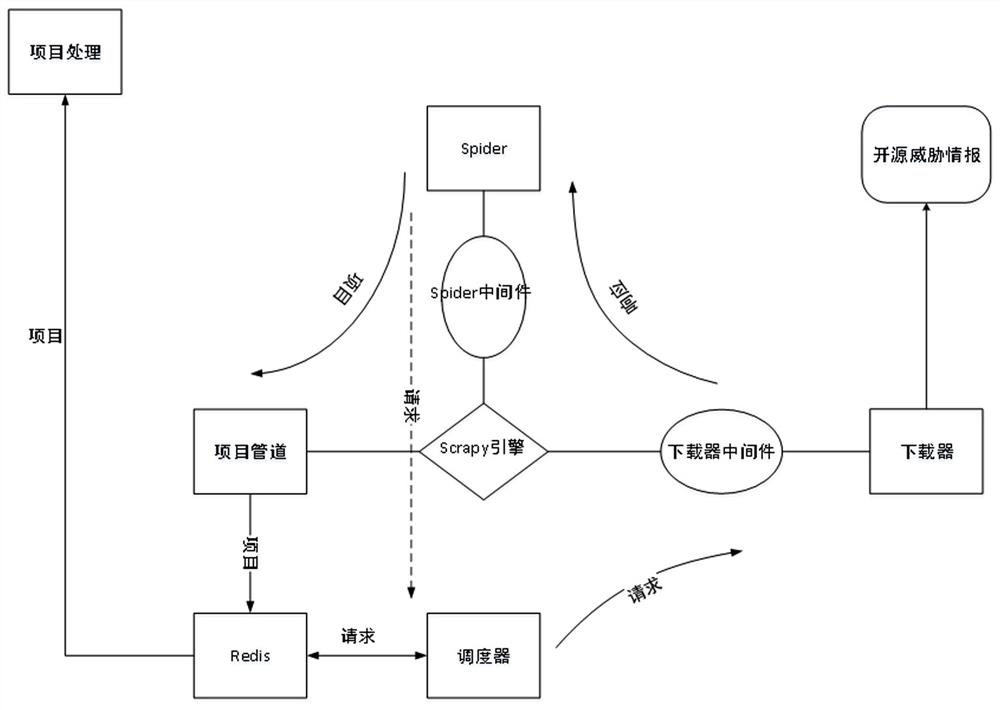
[0103] Generating a network security knowledge map requires a large amount of network security threat intelligence data. In order to collect open source threat intelligence data on the...
Embodiment 2
[0178] This embodiment provides a method for generating a network security knowledge map based on threat intelligence, which is tested for a distributed threat intelligence crawling system.
[0179] The present invention compares the developed distributed threat intelligence crawling system with the stand-alone threat intelligence collection system, and verifies that the developed distributed threat intelligence crawling system has higher efficiency than the stand-alone threat intelligence collection system. Taking common open source threat intelligence sources as an example, the distributed crawler system has 1 master node and 2 slave nodes. After 5 days of continuous operation, the database has stored a total of more than 110,000 web page data. The number of pages crawled at each time point such as Figure 7 as shown, Figure 7 It is the data collection time chart of the distributed crawler system developed in the present invention for threat intelligence data collection. ...
Embodiment 3
[0182] This embodiment provides a method for generating a network security knowledge map based on threat intelligence, and compares the effects of algorithms for improving the quality of threat intelligence data.
[0183] The present invention compares the effect of improving the quality of entity attributes of threat intelligence data by using the proposed algorithm of the present invention and other truth value discovery algorithms on threat intelligence data. The test standard selects the precision rate, recall rate and F1 value commonly used in the truth discovery model. The truth-finding algorithms for comparison are 3-Estimates, Voting, and LTM. The comparative effect is shown in Table 1. It can be seen that the quality improvement algorithm proposed in the present invention is better than the existing algorithm in improving the quality of threat intelligence data.
[0184] Table 1 is a table of comparison results of different data quality improvement algorithms in the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com