Write optimization extensible Hash index structure based on nonvolatile memory and insertion, refreshing and deletion methods
A non-volatile memory, hash index technology, applied in the field of write optimization and scalable hash index structure, can solve the problem of low space utilization, and achieve the goal of increasing space utilization, reducing average length, and improving data access performance. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
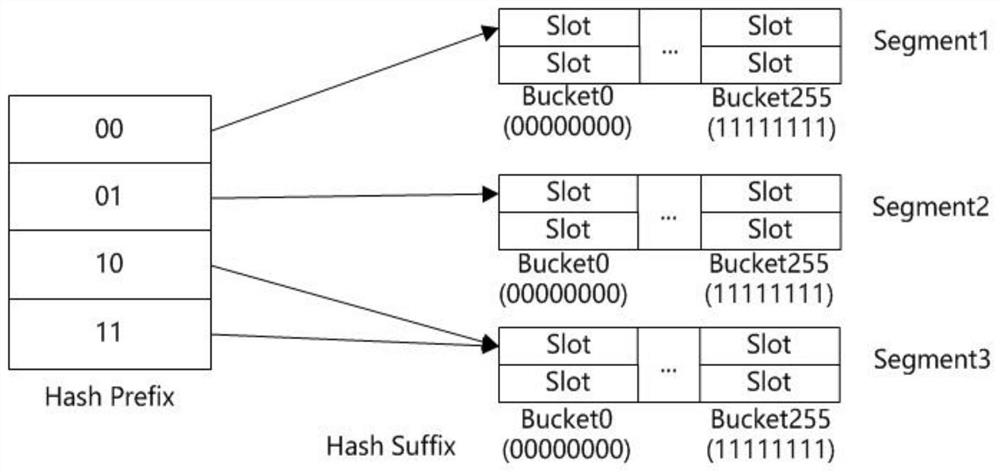
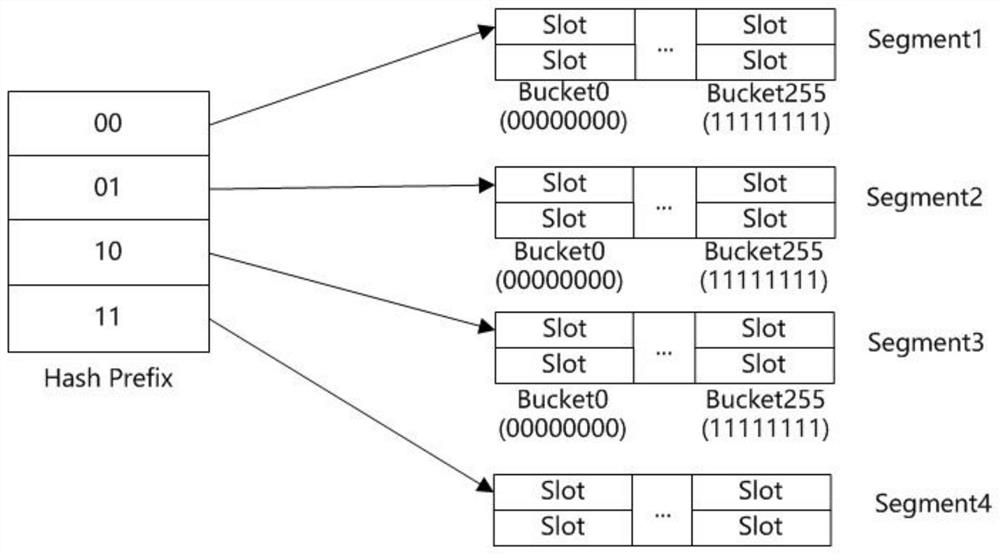
[0033] An embodiment of the present invention provides a write-optimized scalable hash index structure based on non-volatile memory, including: a pointer array, a segment, and a data bucket, wherein the pointer array includes a plurality of directory entries, and each directory entry includes a hash The hash prefix and the pointer to the corresponding segment. The hash prefix is used to match the prefix of the key value calculated by the preset hash function. When the match is successful, the segment pointed to by the pointer corresponding to the hash prefix is the segment to be inserted;
[0034] A segment contains multiple data buckets, and each data bucket has a serial number used to match the suffix of the hash value calculated by the preset hash function, which is the hash function of the virtual neighbor insertion algorithm;
[0035] A data bucket contains several slots, which are used to store data, and the data is key-value pairs.
[0036]Specifically, the hash ind...
Embodiment 2
[0041] Based on the same inventive concept, this application also provides a method for inserting an expandable hash index structure based on an embodiment, including:
[0042] Calculate the first hash value of the data to be inserted by using a preset hash function;
[0043] Match the prefix of the first hash value with the hash prefix stored in the directory entry in the pointer array to locate the segment to be inserted;
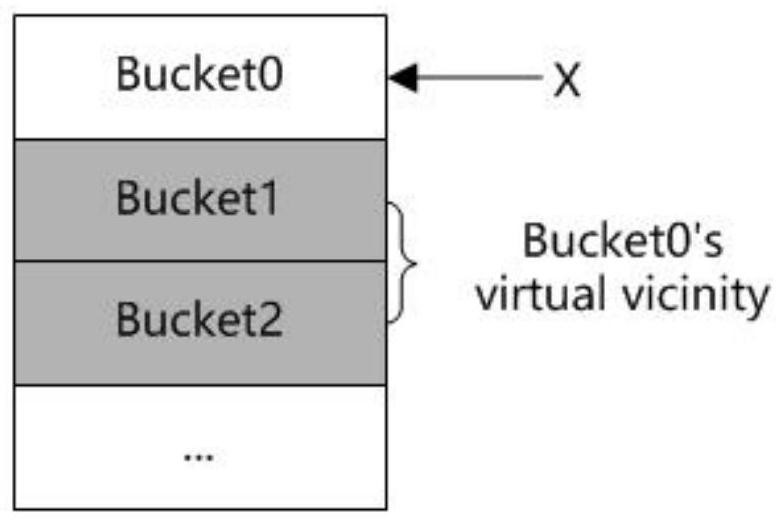
[0044] Determine the data bucket in the segment to be inserted according to the last byte of the first hash value, where the data bucket matching the last byte of the first hash value is used as the target data bucket, and the subsequent Adjacent data buckets are used as virtual data buckets;
[0045] Traverse the target data bucket sequentially. If there is a slot with the same key as the inserted key in the target data bucket, update the value corresponding to the current key in the slot; if there is no slot with the same key as the inserted key in the...
Embodiment 3
[0055] Based on the same inventive concept, the present application also provides a refresh method based on an extensible hash index structure in the embodiment, which adopts in-situ refresh, and during the detection process, the key value to be updated is compared with the key value stored in each slot. Key values are compared, and if they are the same, the key-value pairs in the slot are updated.
[0056] In the prior art, the scalable hash structure based on NVM often uses new data to cover invalid data after the hash table is expanded, so that there will be duplicate key-value pairs, wasting space, and errors in reading data are likely to occur. The application method adopts in-situ refresh, which removes duplicate key-value pairs and improves memory utilization.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com