Power control instruction execution test method and system
A technology of instruction execution and verification method, applied in the field of power system information physical security, can solve problems that affect the safe and stable operation of the power system, easy to tamper, poor privacy, etc., to improve the ability to resist network attacks, ensure safe and stable operation, solve Effects of Security Flaws
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
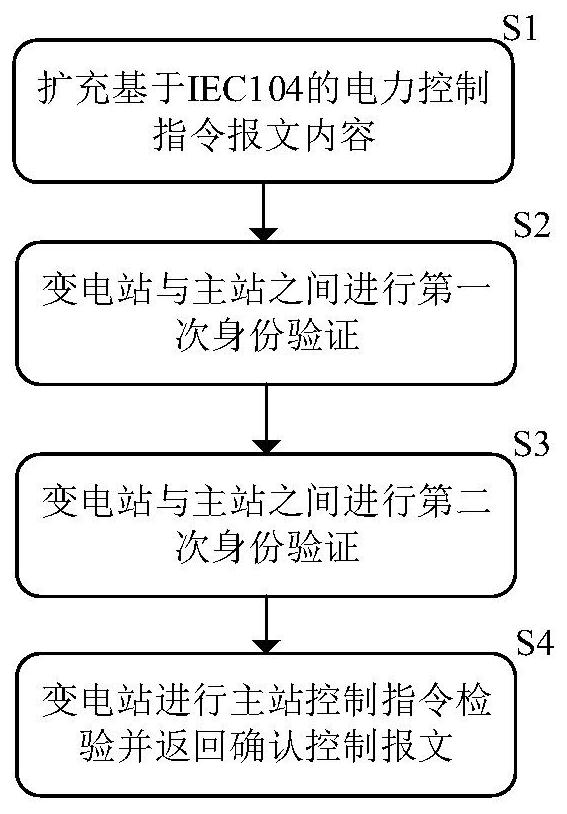
[0070] Further as a preferred embodiment, the step S1 includes:
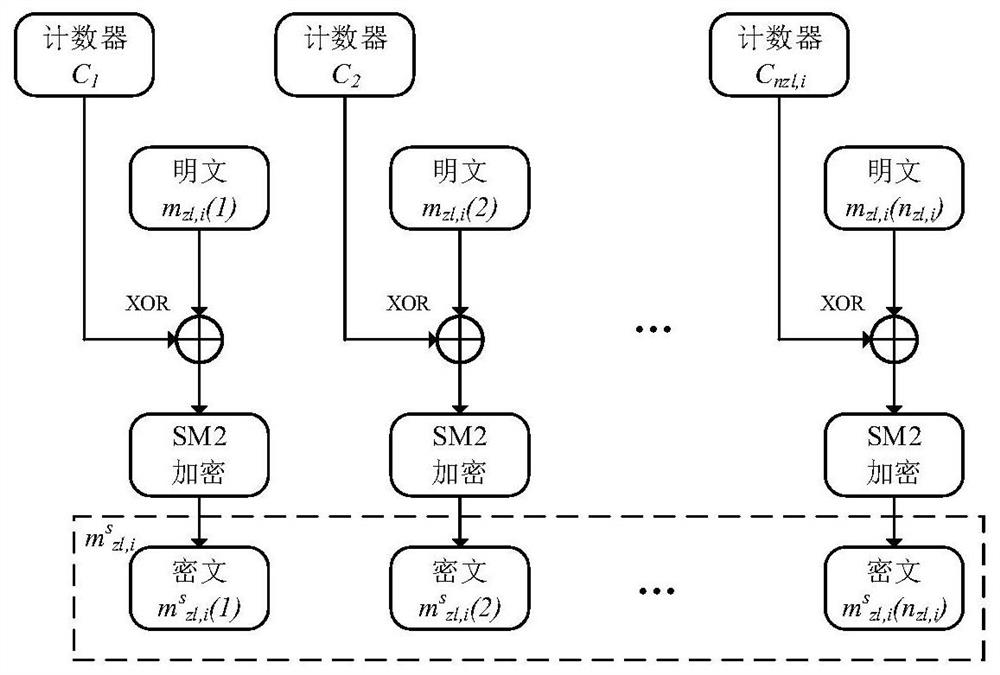
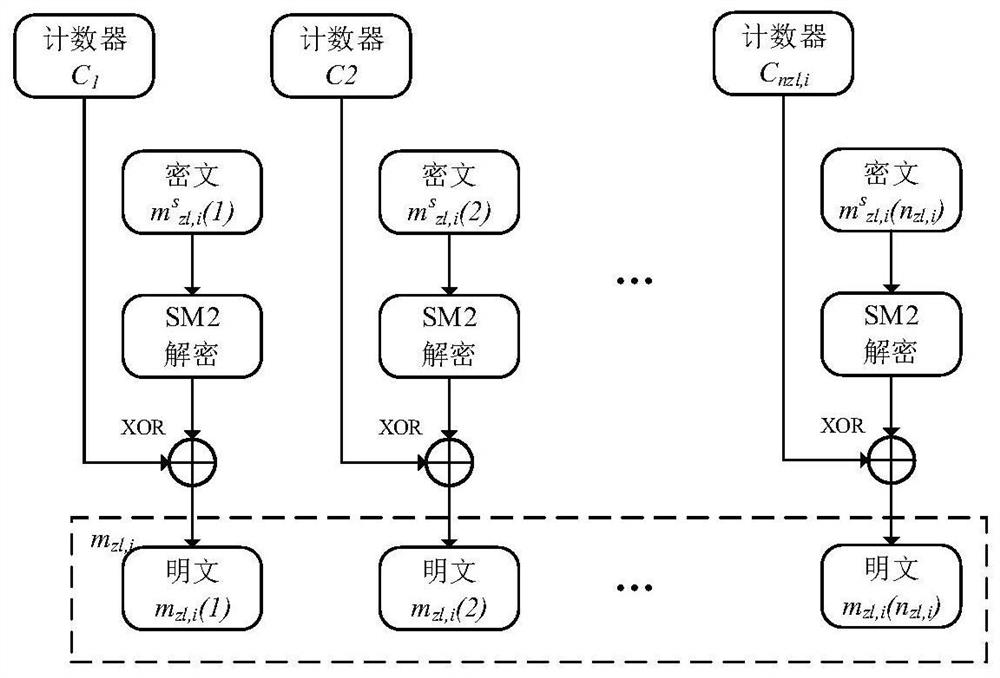
[0071] Step S11: According to the connection message m of the original master station zl,i , the sending time stamp T of the master connection message zl,i , the master digital signature sign of the master connection message zl,i And the random number R of the master connection message zl,i , add the master station connection message after the security domain The specific calculation formula is as follows:
[0072]
[0073] Among them, m zl,i is the connection message of the original master station, i is the serial number of the power control command between the master station and the substation, zl represents the connection of the master station, ·||· is a character connection.
[0074] In one embodiment, the master station sends the sending time stamp T of the connection command zl,i is 20210311120027, the digital signature sign of the master station connection message zl,i For CXSG, the random numb...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com