Energy balance analysis platform safety system based on big data and use method thereof
An energy balance and security system technology, applied in the field of energy balance analysis platform security system based on big data, can solve the problem of inability to protect accounts, data, hosts, and application network security, and cannot guarantee the hardware and virtualization layer security of the cloud platform, Low security performance of cloud products and other issues, to achieve the effect of ensuring core data security, improving reliability and security, and ensuring high availability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
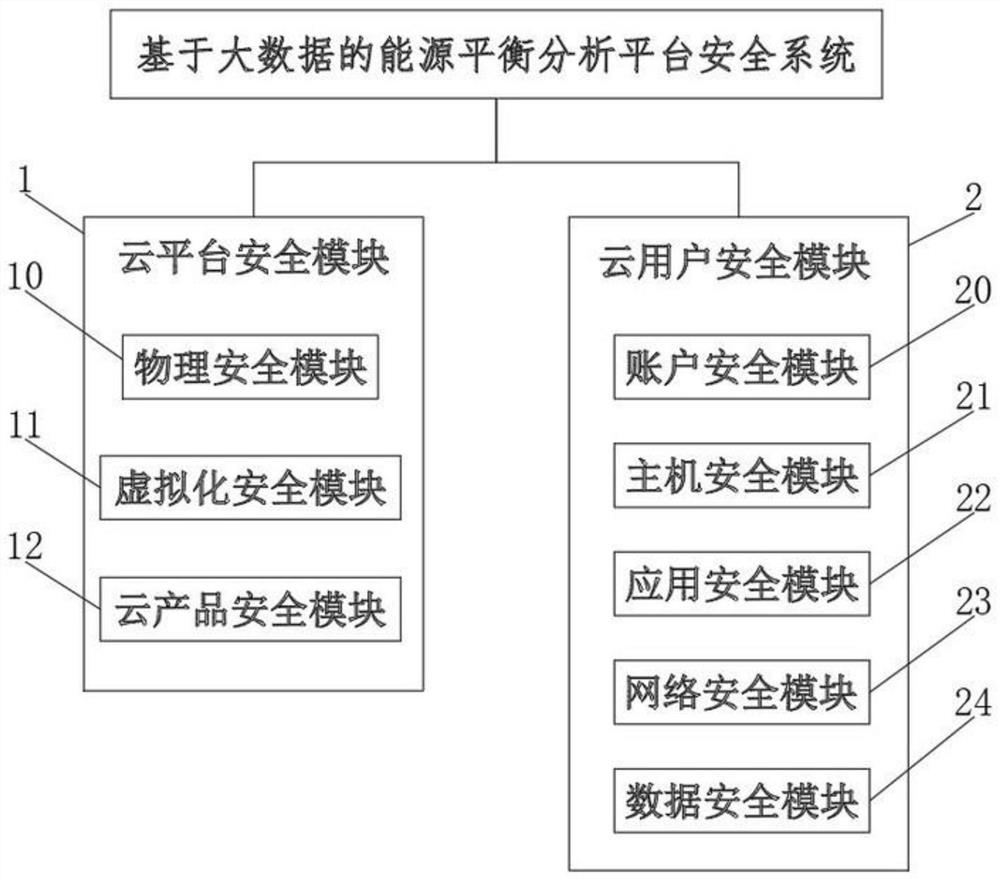
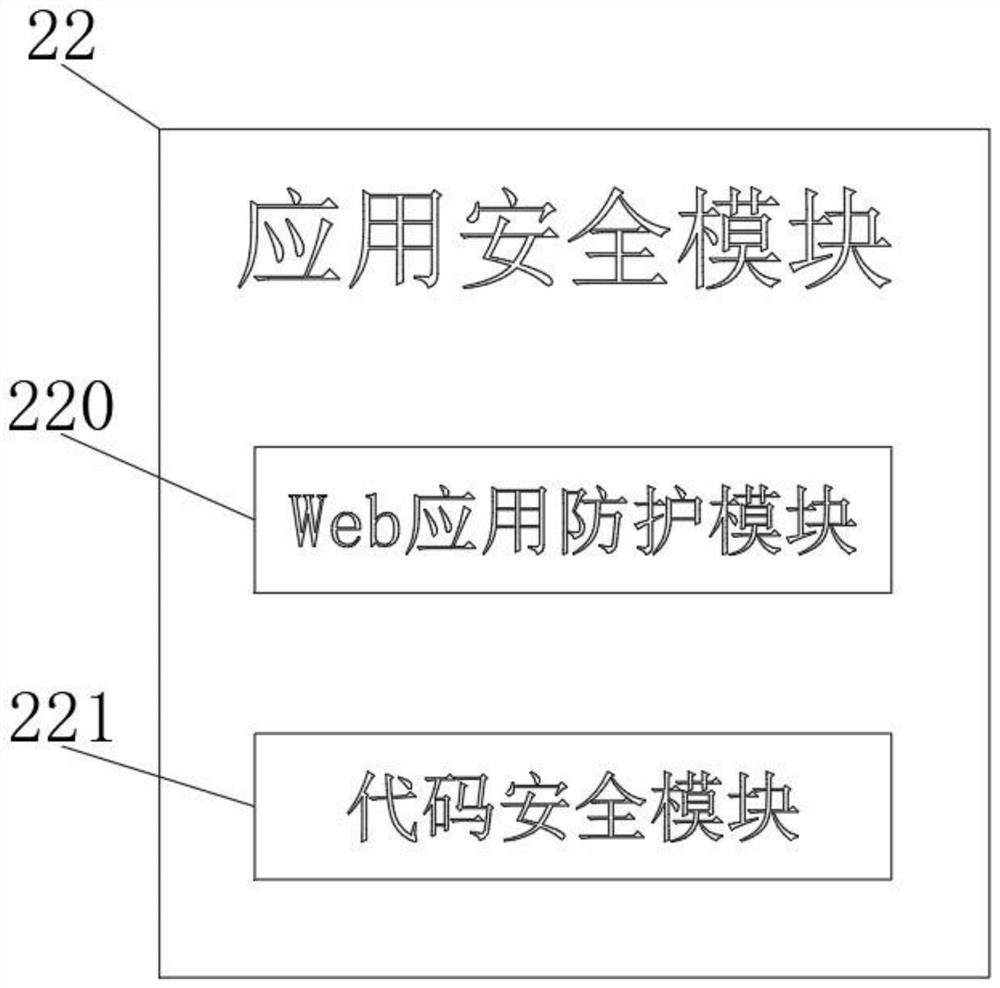
[0052] Please refer to Figure 1-3 As shown, a big data-based energy balance analysis platform security system includes a cloud platform security module 1 and a cloud user security module 2, wherein: the cloud platform security module 1 is used to secure the platform through backup processing, virtualization technology and SPLC For protection, the cloud user security module 2 is used to provide users with data, application, account, host and network security guarantees at five levels. The cloud platform security module 1 includes a physical security module 10, a virtualization security module 11 and a cloud product security module 12. The physical security module 10 is used to ensure that the hardware runs in a safe and stable environment. At the same time, redundant backup processing is performed on devices such as storage computing networks to ensure that no single accident occurs. The virtual security module 11 is used to ensure Multi-tenant isolation, and use three basic v...
Embodiment 2
[0057] On the basis of Embodiment 1, the present invention also provides a method for using the security system of the energy balance analysis platform based on big data, comprising the following steps:
[0058] Step 1: Control the security of the management and maintenance of the hardware server, use virtualization security technology and integrate security into the entire product development life cycle.
[0059] Step 2: Manage cloud account login and MFA, create sub-users and centrally manage sub-user permissions, encrypt data transmission, and monitor sub-user operations.
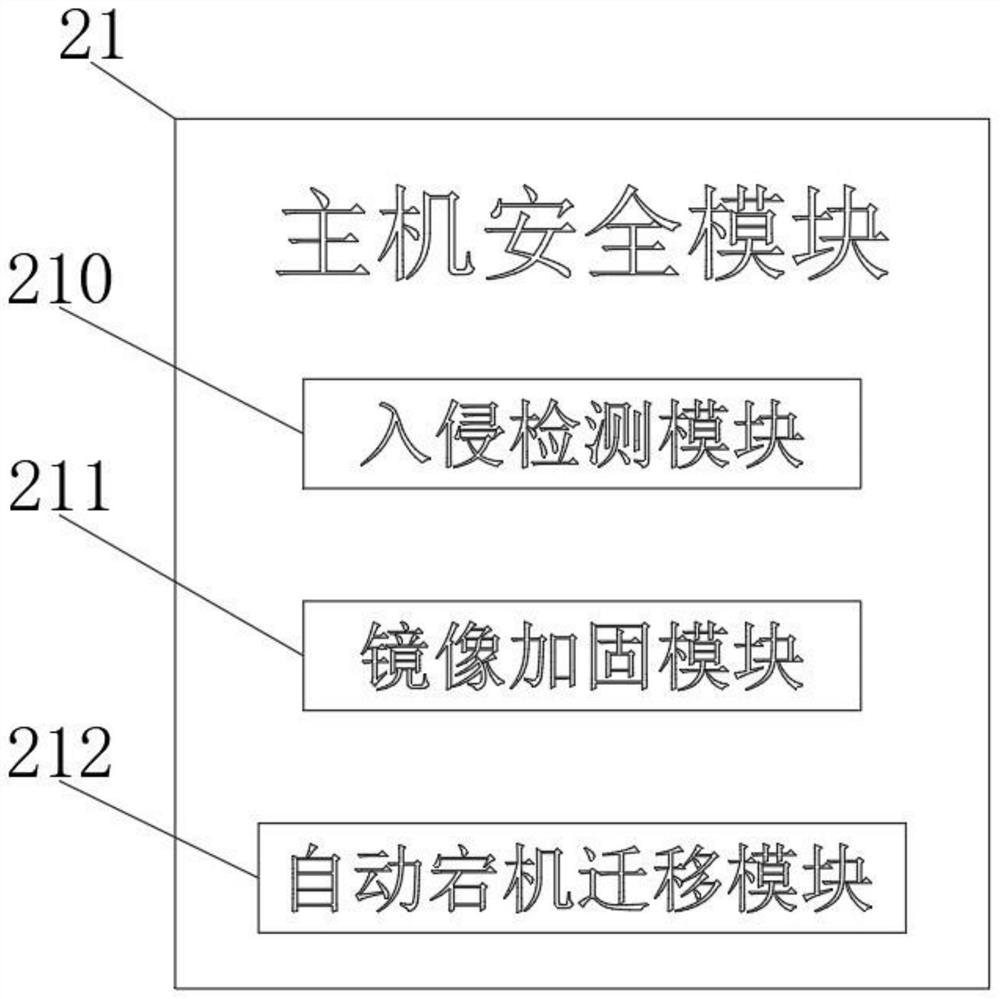
[0060] Step 3: Detect the host, and deploy the cloud server on the host.
[0061] Include the following steps:
[0062] S31. Install the lightweight software Security Knight on the host, which can remind remote logins, identify brute force cracking attacks, check and kill website backdoors, and detect abnormal hosts;
[0063] S32. Use the image to create a new ECS instance and replace the system disk o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com