Data security management method and system
A data security and data technology, applied in the field of data security governance methods and systems, can solve problems such as staying, lack of systematic and effective solutions, etc., to achieve the effect of easy governance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
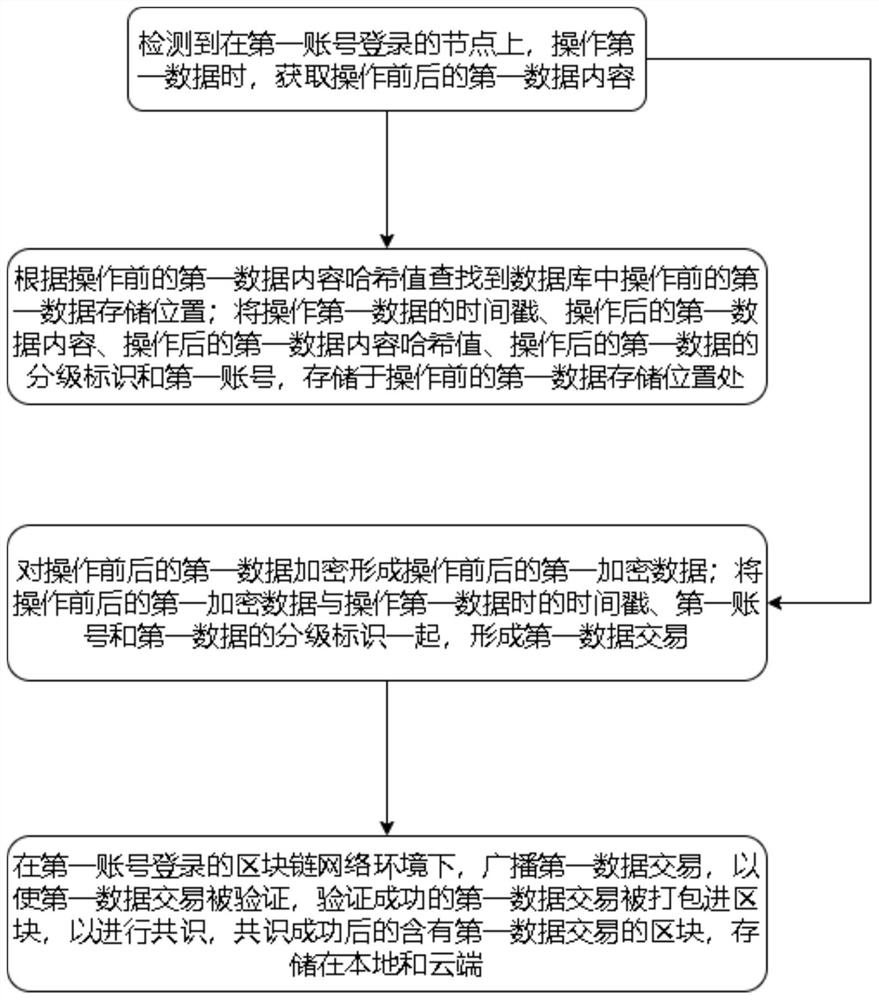
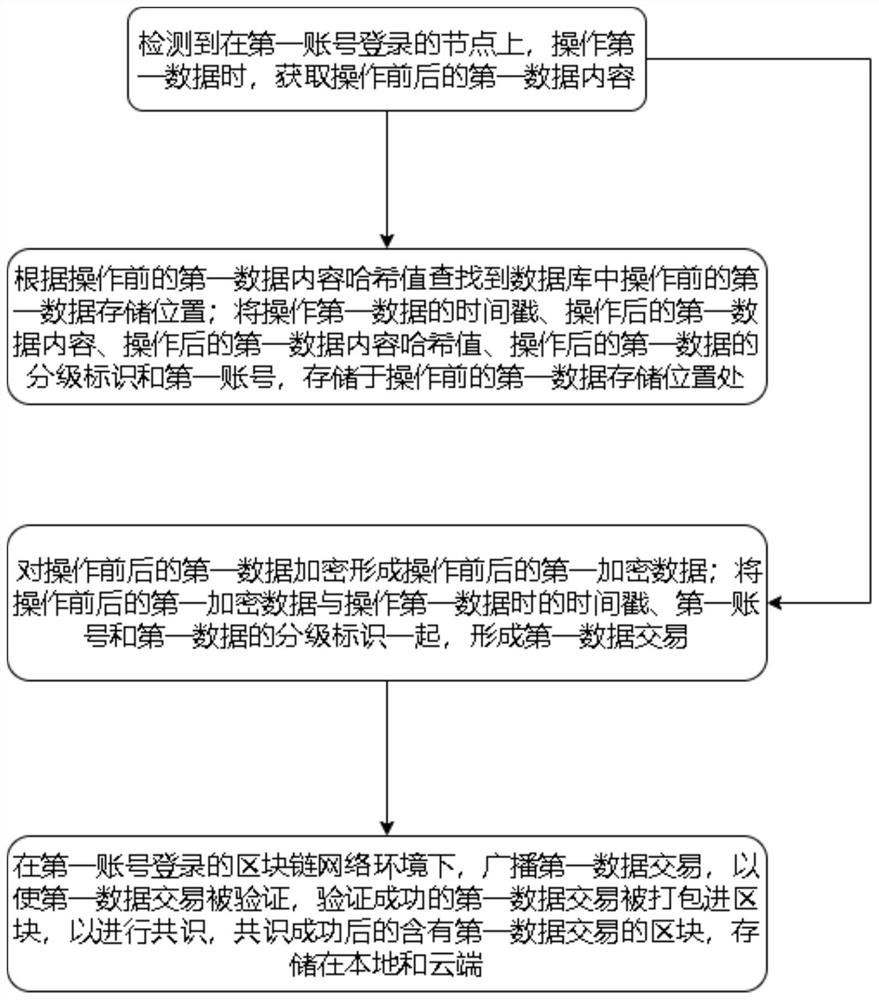
[0072] In the first aspect, this embodiment provides a data security governance method, which can be executed on both ordinary nodes and consensus nodes, such as figure 1 As shown, it includes: detecting that when operating the first data on the node logged in with the first account, obtaining the first data content before and after the operation; finding the first data content in the database according to the hash value of the first data content before the operation A data storage location; store the timestamp of the first data after operation, the content of the first data after operation, the hash value of the content of the first data after operation, the hierarchical identification of the first data after operation, and the first account number in the operation the first data storage location before and after the operation; encrypt the first data before and after the operation to form the first encrypted data before and after the operation; combine the first encrypted data...
Embodiment 2
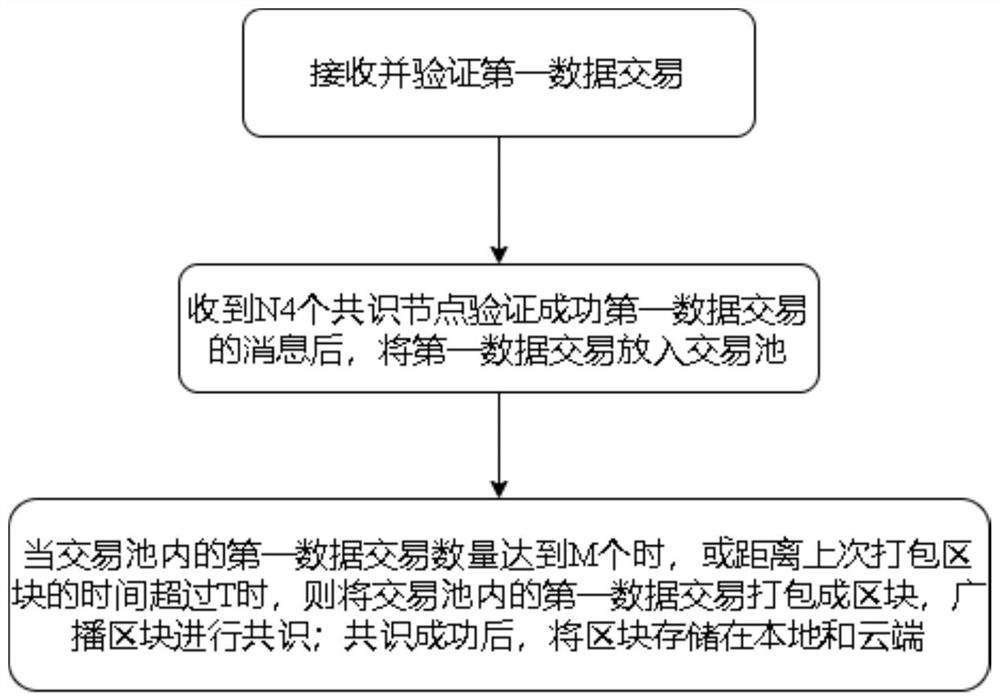
[0116] The first aspect of this embodiment provides a data security governance method, which is executed on consensus nodes, such as figure 2 shown, including:
[0117] receiving and verifying a first data transaction;
[0118] After receiving the message that N4 consensus nodes have successfully verified the first data transaction, put the first data transaction into the transaction pool;
[0119] When the number of first data transactions in the transaction pool reaches M, or when the time from the last packaged block exceeds T, the first data transaction in the transaction pool is packaged into a block, and the block is broadcast for consensus; after the consensus is successful , store blocks locally and in the cloud;
[0120] Among them, N4≥0.51*N, N is the total number of consensus nodes in the blockchain network environment; M, N4 and N are all integers.
[0121] The value of M is set to a fixed value, and blocks are packaged quantitatively or regularly for consensus...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com