Cross-platform malicious software confrontation sample generation method and system
A malware and anti-sample technology, applied in the field of software security, to achieve the effect of optimizing feature vectors, improving efficiency, and improving robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
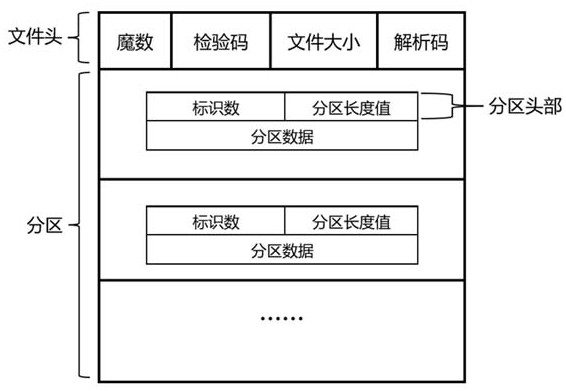
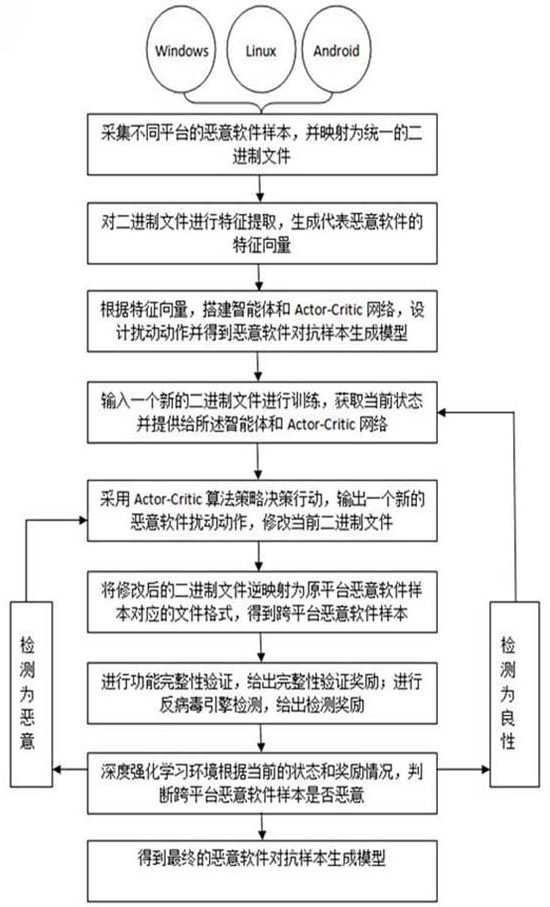
[0068] In an exemplary embodiment, a method for generating cross-platform malware adversarial samples is provided, such as figure 1 As shown, the method includes:
[0069] Collect multiple types of malware samples from different platforms, and map different types of malware samples into unified binary files;
[0070] Perform feature extraction on the binary file to generate a feature vector representing malicious software;
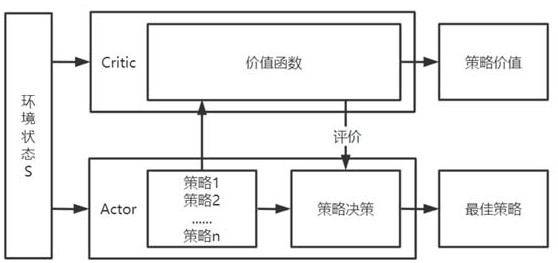
[0071] According to the eigenvectors, build an agent and an Actor-Critic network, design malware disturbance actions and encapsulate them in the deep reinforcement learning action space, and obtain a malware confrontation sample generation model; actions in the action space will act on the eigenvectors, and the action The design will be based on the eigenvector, and we hope to achieve our goal with the smallest disturbance.
[0072] Input a new binary file to train the malware confrontation sample generation model, and the deep reinforcement learning env...
Embodiment 2
[0088] Based on Embodiment 1, a method for generating a cross-platform malware countermeasure sample is provided, and the various types of malware samples include PE executable files on the Windows platform, ELF executable files on the Linux platform, and apk files on the Android platform.
[0089] The full name of PE files is Portable Executable, which means portable executable files. Common EXE, DLL, OCX, SYS, and COM are all PE files. PE files are program files on the Microsoft Windows operating system (maybe indirectly execution, such as a DLL).
[0090] The full name of the ELF file is Executable and Linkable Format, which means an executable and linkable format. ELF files are divided into three categories: 1. Relocatable (relocabtable) files, which store code and appropriate data, used to communicate with other object files together to create an executable or a shared file. 2. The executable (executable) file stores a program for execution, which indicates how exec (BA_...
Embodiment 3
[0102] Based on the above embodiments, for the existing anti-sample generation method, there is a problem that the malware loses its integrity and function after a series of excessive or strong injections, resulting in too redundant model training for the anti-virus engine and malware adversarial samples. For the problem of poor robustness, the present invention provides a method for generating cross-platform malware adversarial samples, designing malware disturbance actions and encapsulating them into the deep reinforcement learning action space, the action space includes:
[0103] String obfuscation: Find strings and function calls by analyzing the abstract syntax tree, then obfuscate the strings, insert variable definitions / assignments at appropriate positions (including functions or global contexts), and hide functions and then obfuscate the code;
[0104] Section table modification: overwrite and append, import and append, rename, add, and append operations to the section ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com