Safety injection automation method and device, electronic equipment and storage medium
An automatic device and security injection technology, which is applied in the field of data security, can solve the problems of complex system controls, labor-intensive manual injection, and inability to analyze results in real time, so as to achieve the effect of improving efficiency and quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
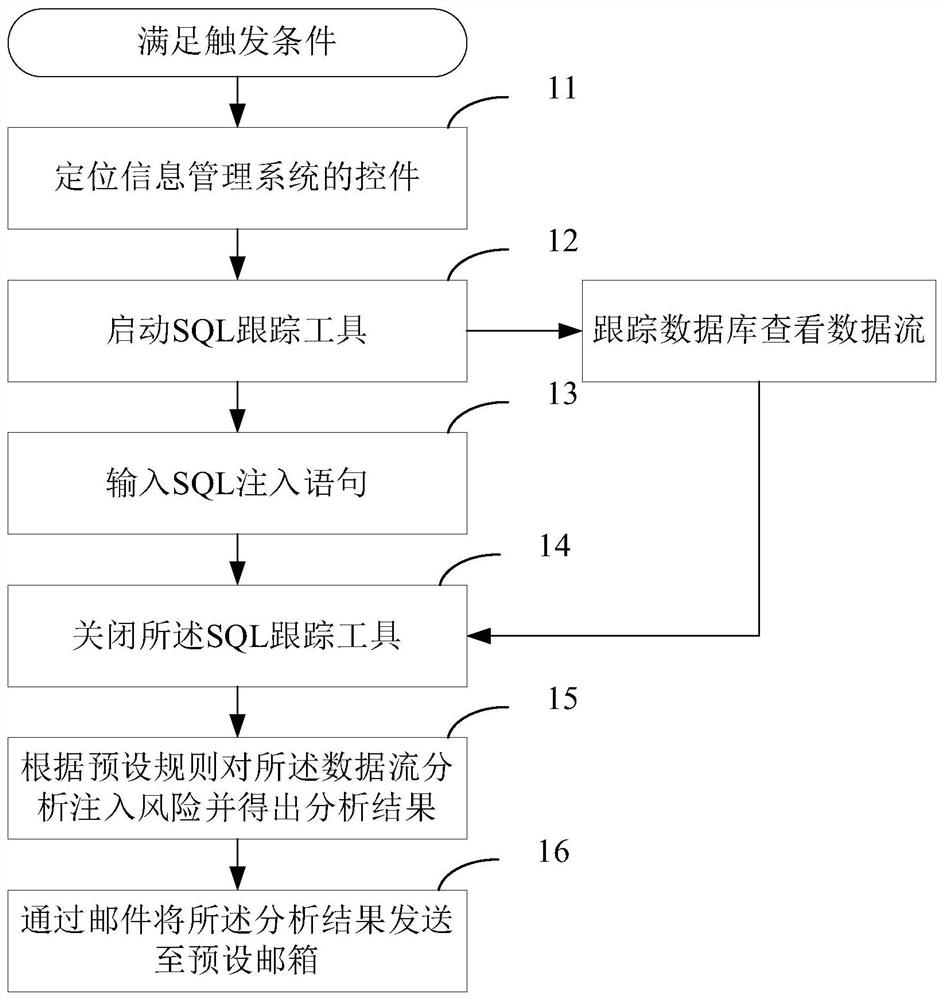
[0045] figure 1 A security injection automation method of an information management system based on a C / S architecture in this embodiment is shown. Wherein, the information management system may be any applied information management system, such as an information management system for personnel file management, an information management system for borrowing books in a library, and the like. Security injection automation methods include:
[0046] When the trigger condition is met, the trigger condition can be a timing trigger, and the following steps are performed:
[0047] Step 11: Locate the controls for the information management system. If the information management system is designed based on the Windows system, the controls can be classified into Windows standardized controls and Windows non-standardized controls. The positioning of Windows standardized controls is relatively simple and can be realized by using autoit. The positioning of Windows non-standardized contro...
Embodiment 2
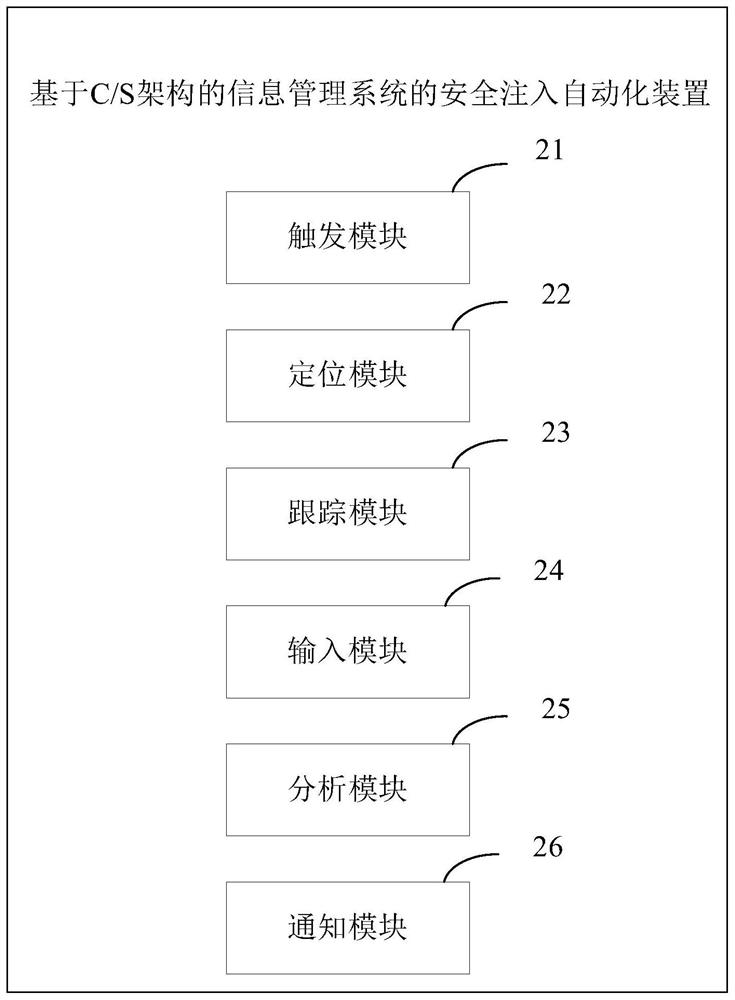
[0070] figure 2 It shows a security injection automation device for an information management system based on a C / S architecture in this embodiment. Wherein, the information management system may be any applied information management system, such as an information management system for personnel file management, an information management system for borrowing books in a library, and the like. The security injection automation device includes: a trigger module 21 , a location module 22 , a tracking module 23 , an input module 24 , an analysis module 25 and a notification module 26 .
[0071] The triggering module 21 is configured to invoke the positioning module 22 when a triggering condition is met. The trigger condition may be a timing trigger.
[0072] The locating module 22 is used to locate the control of the information management system, and then calls the tracking module 23 to start the SQL tracking tool, and the SQL tracking tool is used to track the database viewing...
Embodiment 3
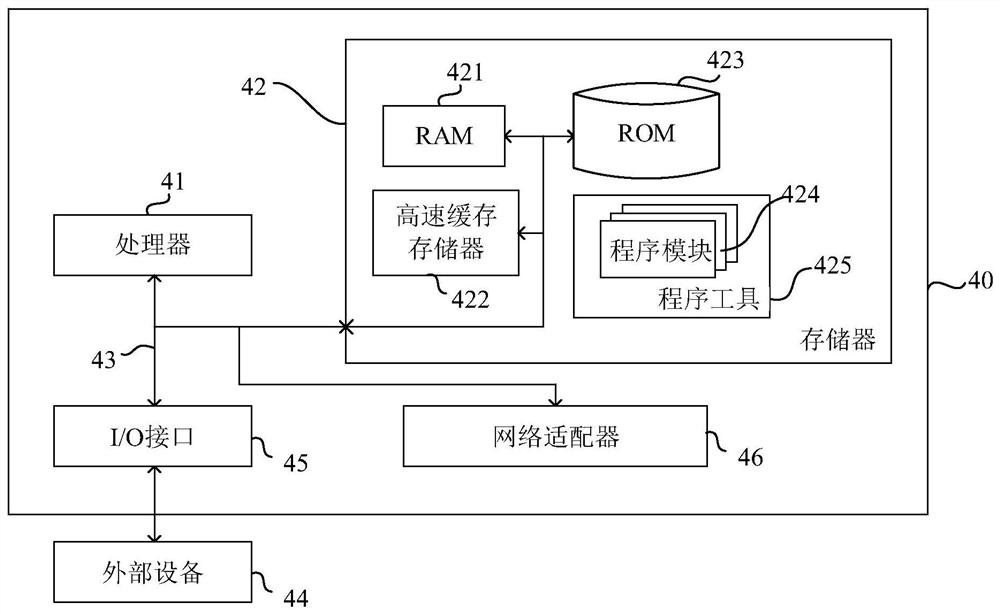
[0080] image 3 It is a schematic structural diagram of an electronic device provided by Embodiment 3 of the present invention. The electronic device includes a memory, a processor, and a computer program stored on the memory and operable on the processor, and the processor implements the method in Embodiment 1 when executing the program. image 3 The electronic device 40 shown is only an example, and should not impose any limitation on the functions and application scope of the embodiments of the present invention.
[0081] Such as image 3 As shown, electronic device 40 may take the form of a general-purpose computing device, which may be a server device, for example. Components of the electronic device 40 may include, but are not limited to: at least one processor 41 , at least one memory 42 , and a bus 43 connecting different system components (including the memory 42 and the processor 41 ).
[0082] The bus 43 includes a data bus, an address bus and a control bus.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com