Detection method for encrypted traffic of confused KCP protocol
A detection method and technology for mixing traffic, applied in transmission systems, electrical components, etc., can solve the problems of inability to confuse KCP protocol traffic identification, inability to meet the supervision needs of network regulators, etc., and achieve the effect of resisting unstable factors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
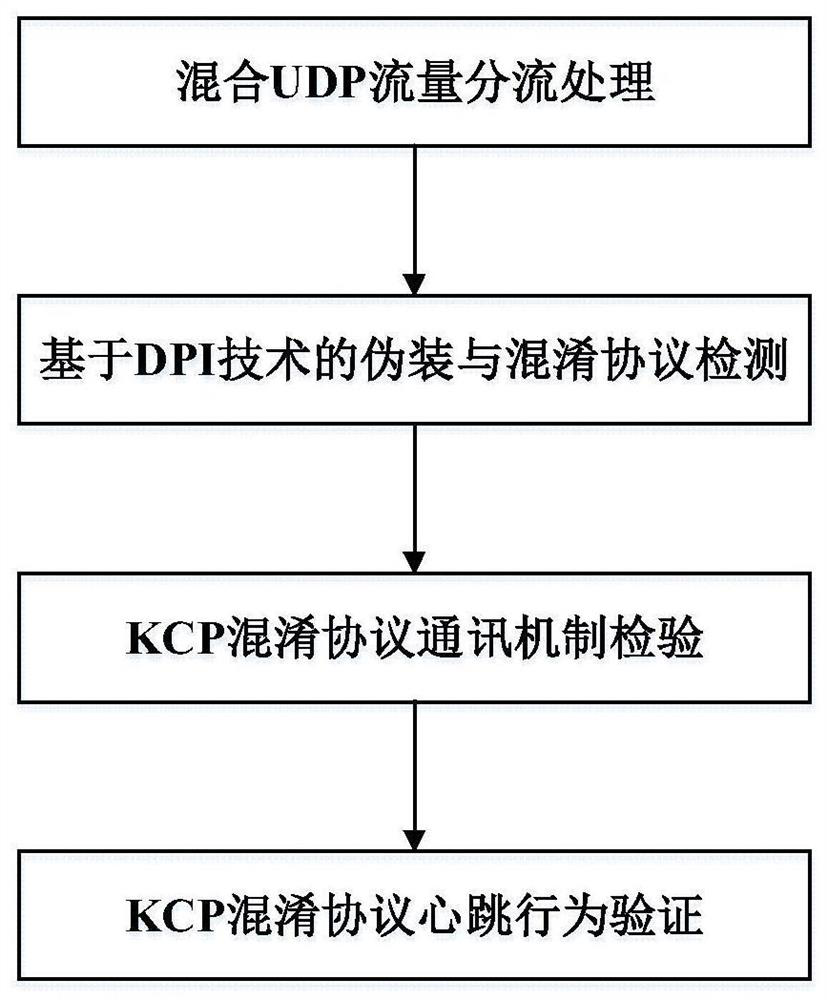
[0015] The present invention is directed to a detection method for an encrypted proxy channel of an obfuscated KCP protocol, which specifically includes the following steps:
[0016] Step 1: Based on the libpcap network library, the UDP mixed traffic is divided according to the source address, destination address, source port, destination port, protocol quintuple and time information, and the UDP data flow information after the division is obtained and sent to the cache one by one. queue.
[0017] Step 2: Read the UDP traffic information of the cache queue one by one, extract the data payload packet load information, and identify the masquerading application type; extract the data packet payload information, filter the application protocol field, extract the 1-22 bytes payload information after the masquerading layer, and detect the KCP Protocol normative, if it does not conform to the KCP protocol format, further identify whether the payload content is the obfuscated KCP prot...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com