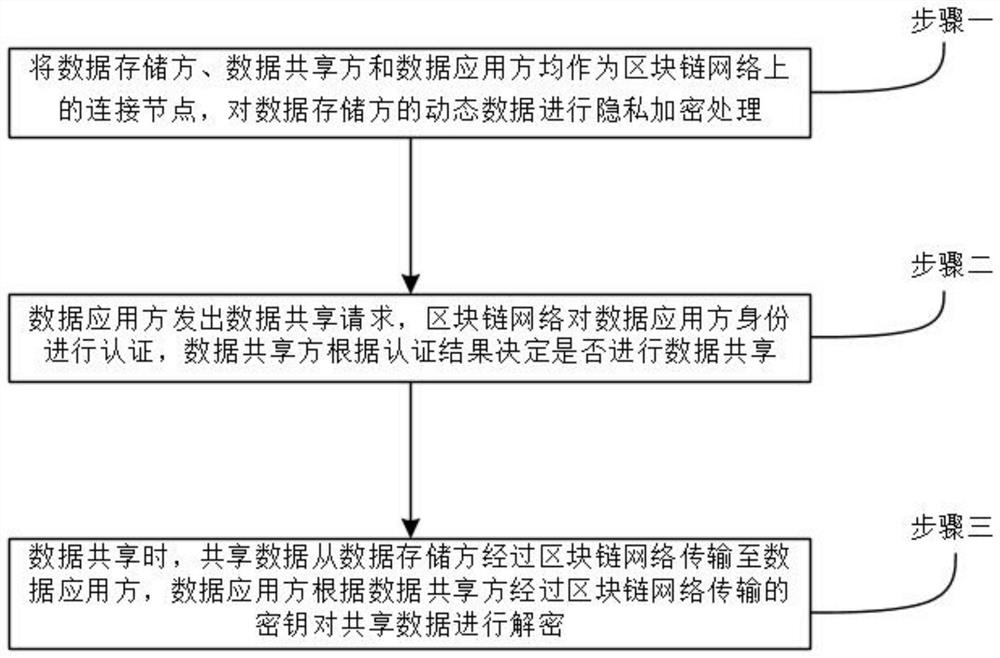
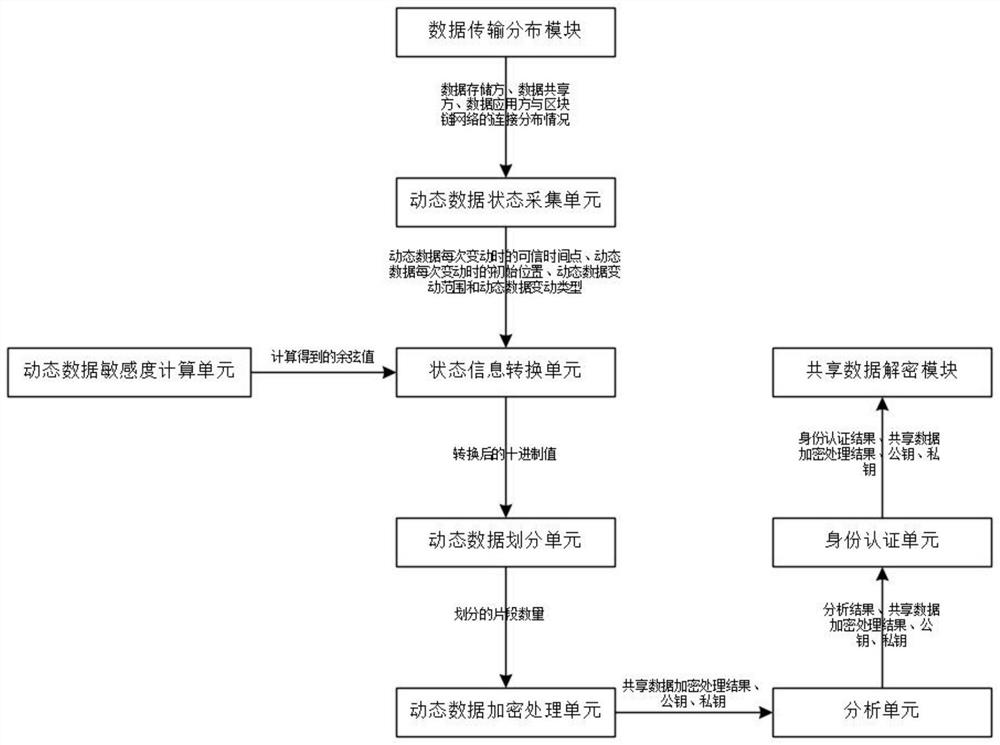
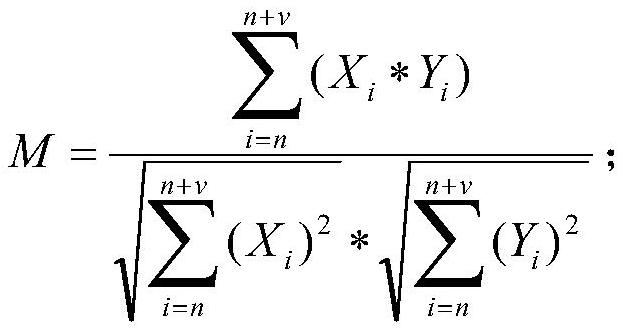Block chain-based big data privacy sharing security protection system and method
A security protection and data sharing technology, which is applied in the field of big data privacy sharing security protection system based on blockchain, can solve the problems of security risks, big data security risks, and low overall security, so as to improve the scope of application and improve privacy Protective, leakage risk reduction effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0097] Example: Let the credible time point when the dynamic data change be 15:06:27 on February 18, 2013, the dynamic data change range is 4, the initial position of the dynamic data change is the 46th, and the dynamic data change type is replacement data , the replacement data is (1,3,7,3), the original data is (2,5,5,7), then the data is converted to decimal value:
[0098] The credible time point of February 18, 2013 15:06:27 is converted to a decimal value: 135\2\12\9\6\15;
[0099] The dynamic data change range is converted to a decimal value: 4;
[0100] The initial position of the dynamic data change is converted to a decimal value: 22;
[0101] If the dynamic data change type is replacement data, the corresponding decimal value is: 1;
[0102] Then, the sets A, B, and C are expressed as:
[0103] A=[1135\2\12\9\6\15], B=[4], C=[22];
[0104] Using the calculation formula M to calculate the sensitivity between the dynamic data and the original data, then:
[0105]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com