Method for detecting and monitoring gusty abnormal network flow
A technology for network traffic and abnormal traffic, applied in the field of detection and monitoring of sudden abnormal network traffic, can solve problems such as insufficient analysis and statistics effect, short-slot sudden abnormal traffic detection cannot be effectively solved, etc. Data processing speed, low cost, and the effect of solving overload problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
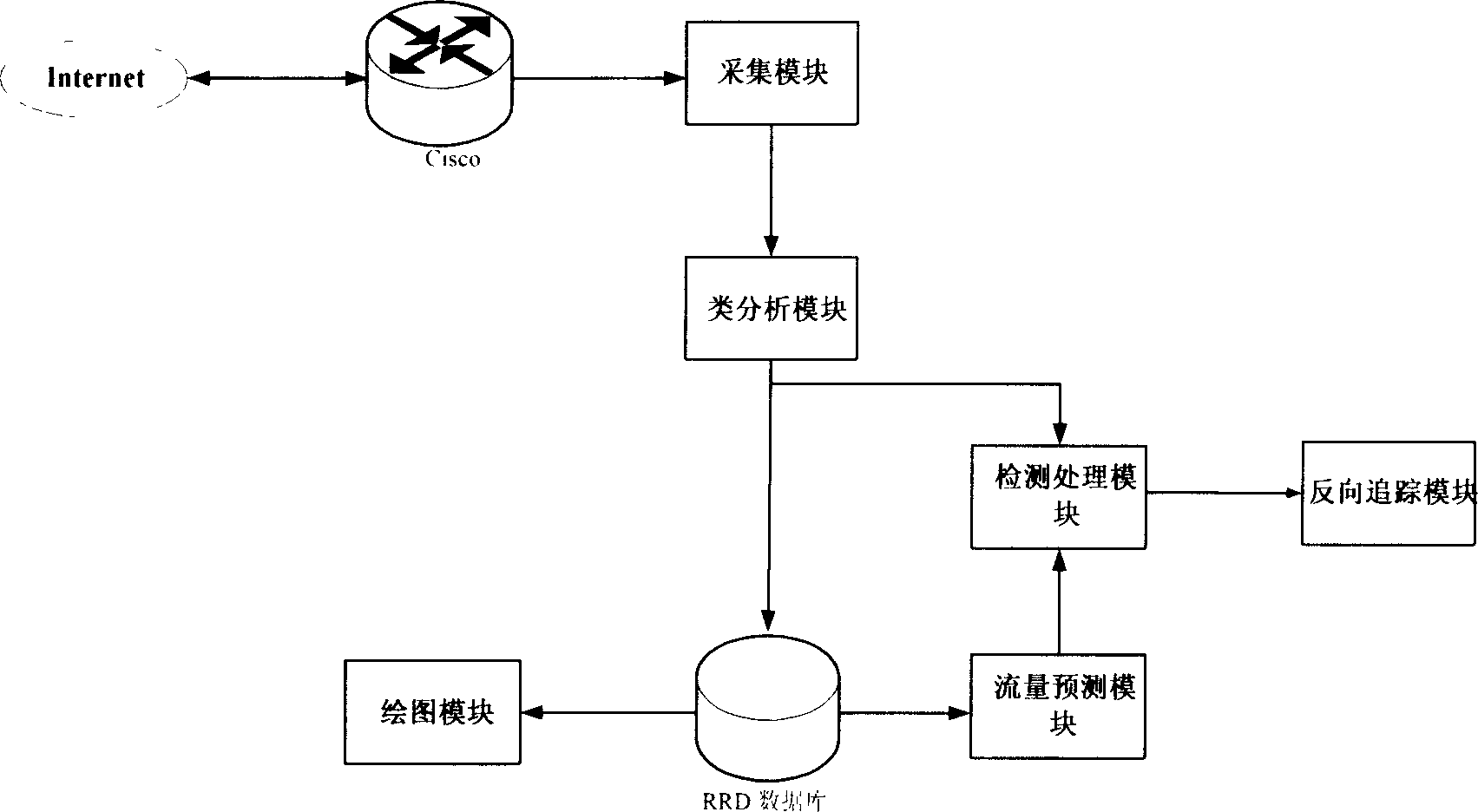
[0017] The implementation of the present invention will be further described below in conjunction with the accompanying drawings. The system based on the method of the present invention is made up of six blocks of acquisition module, class analysis module, detection processing module, flow prediction module, drawing module and reverse tracking module, and the specific implementation and application of each module are as follows:
[0018] (1) Acquisition module——traffic mapping collection, which collects traffic information in the entire network environment through NetFlow in the NS-2 simulation environment;
[0019] (2) Class analysis module - statistics, classification and totalization, classify the traffic according to the different sites visited by users, and make statistics on the classified traffic, and then store it in the corresponding RRD cycle database to establish different areas of the network, different The flow record information of the time period;
[0020] (3) ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com