Method for realizing network virtual magnetic disk
A virtual disk and network virtualization technology, applied in the field of computer networks, can solve problems such as high hardware resource requirements, easy broadcast storms, and performance impacts, and achieve stable and efficient systems, avoid broadcast storms, and high reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] Preferred embodiments of the present invention are described in detail below.
[0031] The realization method of network virtual disk of the present invention, it comprises concrete steps as follows:
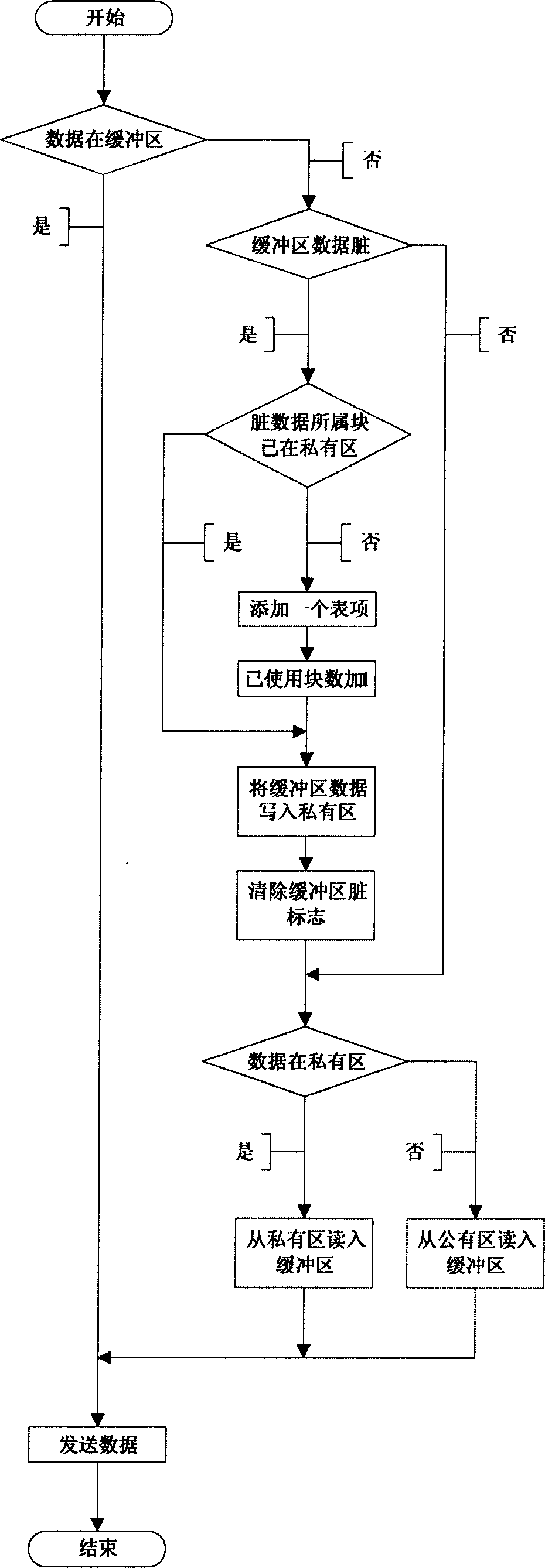
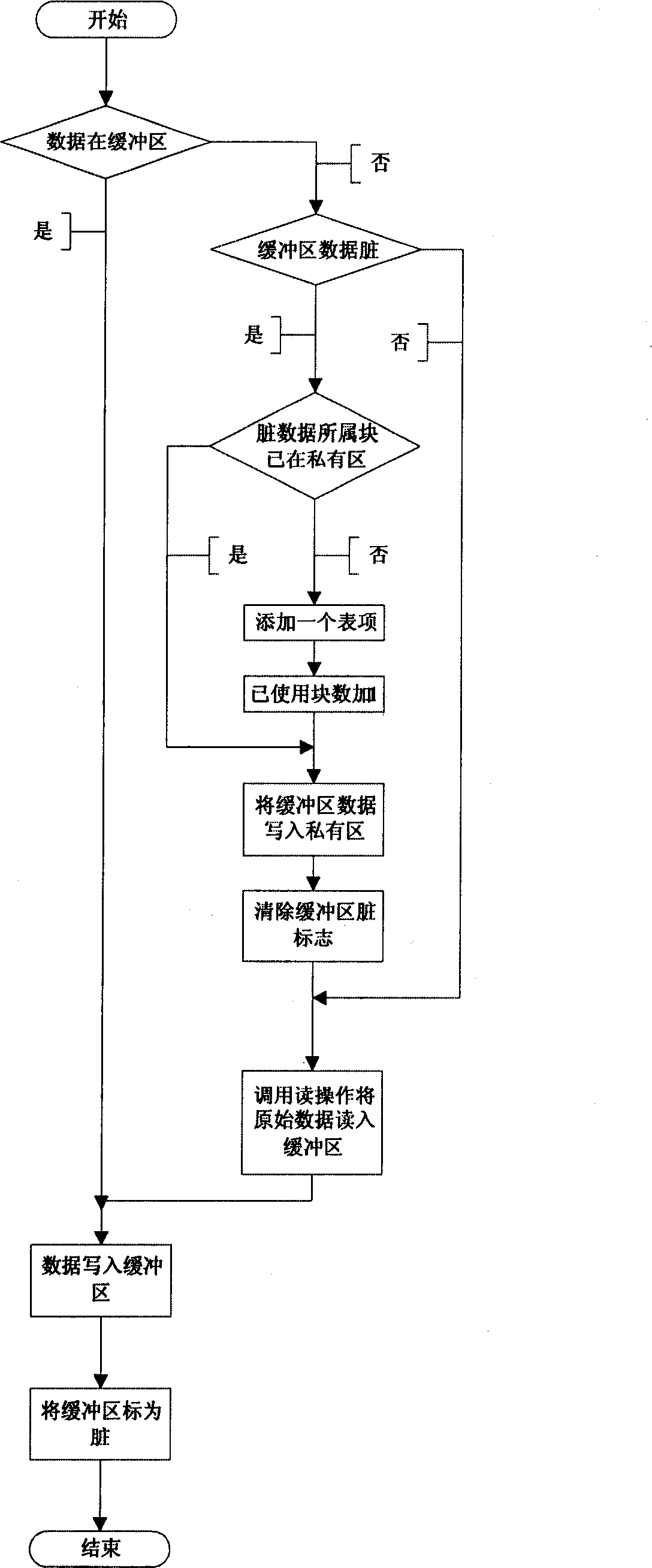
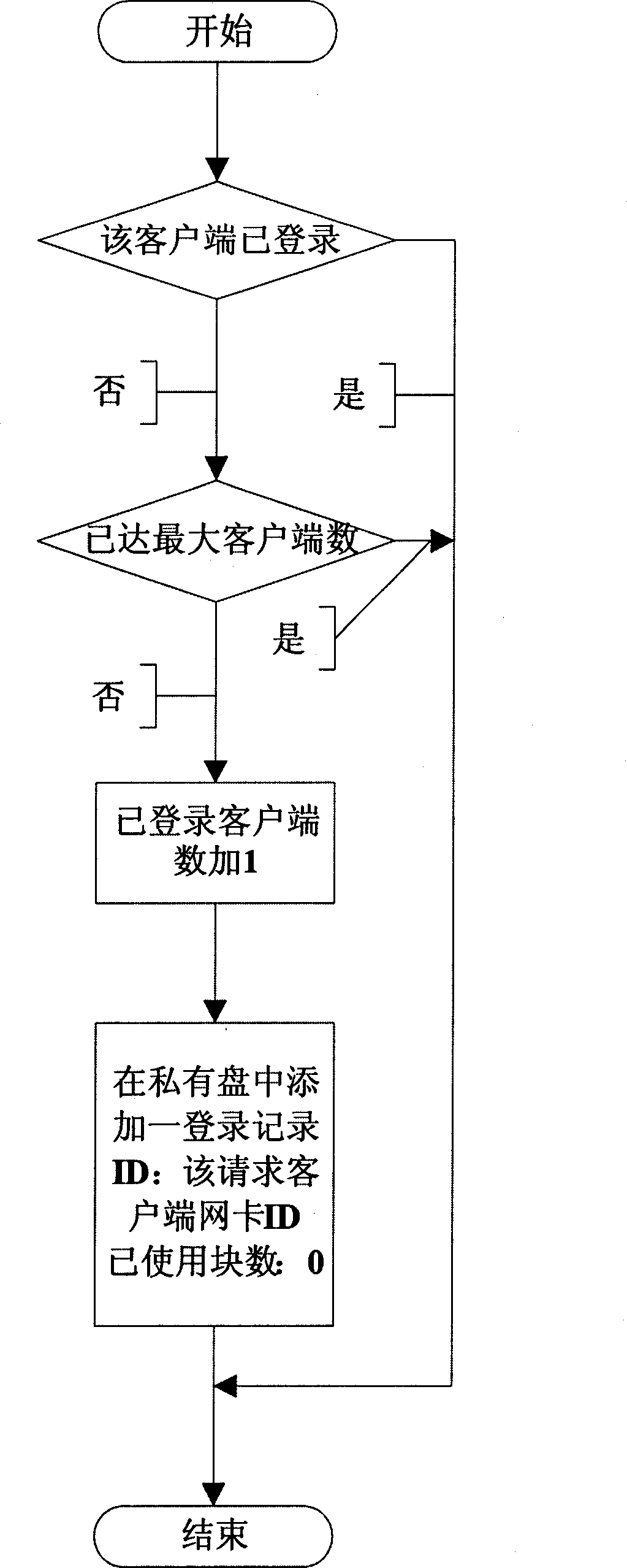
[0032] 1. The client PCIROM intercepts the interrupt INT13 to generate a virtual disk, and sends the sector read and write request to the server by directly operating the network card hardware. The server network card ID number is obtained from the local network card EEPROM;
[0033] 2. The server PCIROM first obtains its working mode through a serial port switch group and reflects its working state. Then directly operate the network card hardware to read the client's request, and call the INT13 of the motherboard BIOS to access the public disk and private disk according to the request, so as to complete the client's request. Finally, the result is sent to the client by directly operating the network card hardware;
[0034] 3 The server has two hard disks, which are di...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap