Network intrusion detection method
A detection method and network intrusion technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve the problems of no solution, decreased detection accuracy, poor adaptability, etc., to achieve low computational cost, strong adaptability, Good real-time effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
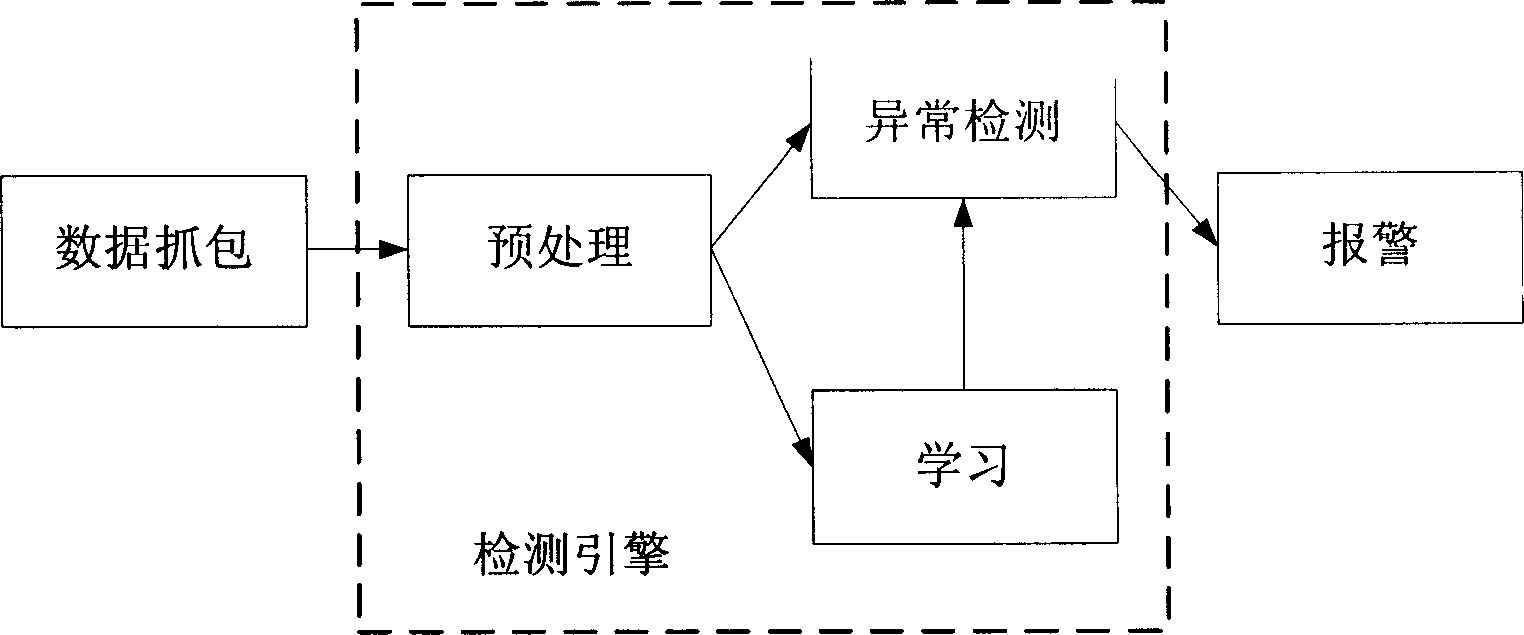
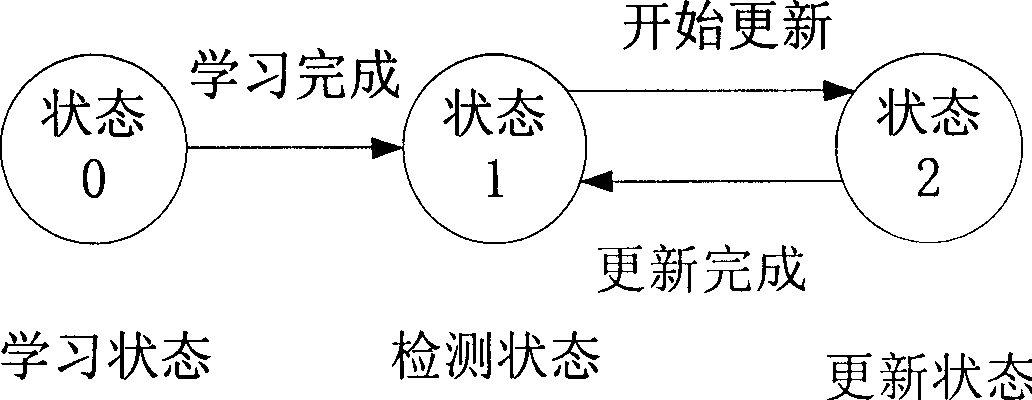
[0028] Embodiment: the network intrusion detection method is made up of data capture step, decoding step, data preprocessing step, learning step, detection step and abnormal alarm step, as figure 1 As shown, the data capture step collects the original data of the network; the decoding step analyzes the data network protocol; the data preprocessing step extracts the traffic characteristics of the data; the learning step collects enough traffic characteristic data to generate a new detection model to replace the original There is a detection model; the detection step uses the detection model generated by the learning step to detect network data; the abnormal alarm step obtains the message of the detection step and generates an abnormal alarm.
[0029] A complete detection process is as follows:
[0030] After the data packet capture step captures network data, it is sent to the decoding step to analyze the network protocol of the data packet; after decoding, it is sent to the pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com