Public key infrastructure system, local safety apparatus and operation method
A technology of public key infrastructure and security equipment, which is applied in the field of public key infrastructure system devices, and can solve problems such as complex certificate management, large amount of calculation, and complex identity management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
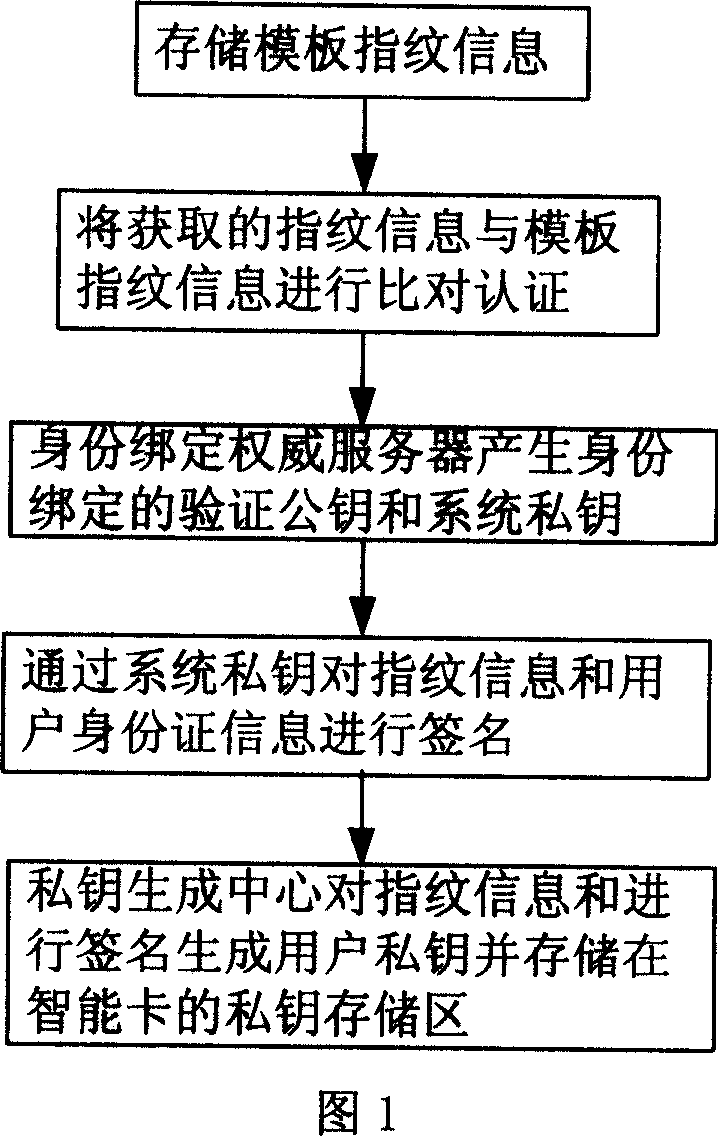
[0097] In order to solve the problems of complex certificate management, large amount of calculation and complex identity management when the user has multiple public keys in the existing public key infrastructure based on digital certificates, this method is to combine a pair of keys with people's The biometric feature is bound locally, and the biometric feature is used as the public key, as shown in Figure 1. The specific steps are as follows:
[0098] Step 101: Store template fingerprint information in the smart card device:
[0099] Under the supervision of a reliable third party, the user uses a smart card device to sample the user's biological characteristics such as fingerprints, obtains the unique fingerprint for digital processing, converts it into a digital code, and further uses these digital codes as template fingerprint information. The digitized fingerprint information is a For larger files, use ID in this embodiment U Indicates that the ID U Stored in the user...
Embodiment 2
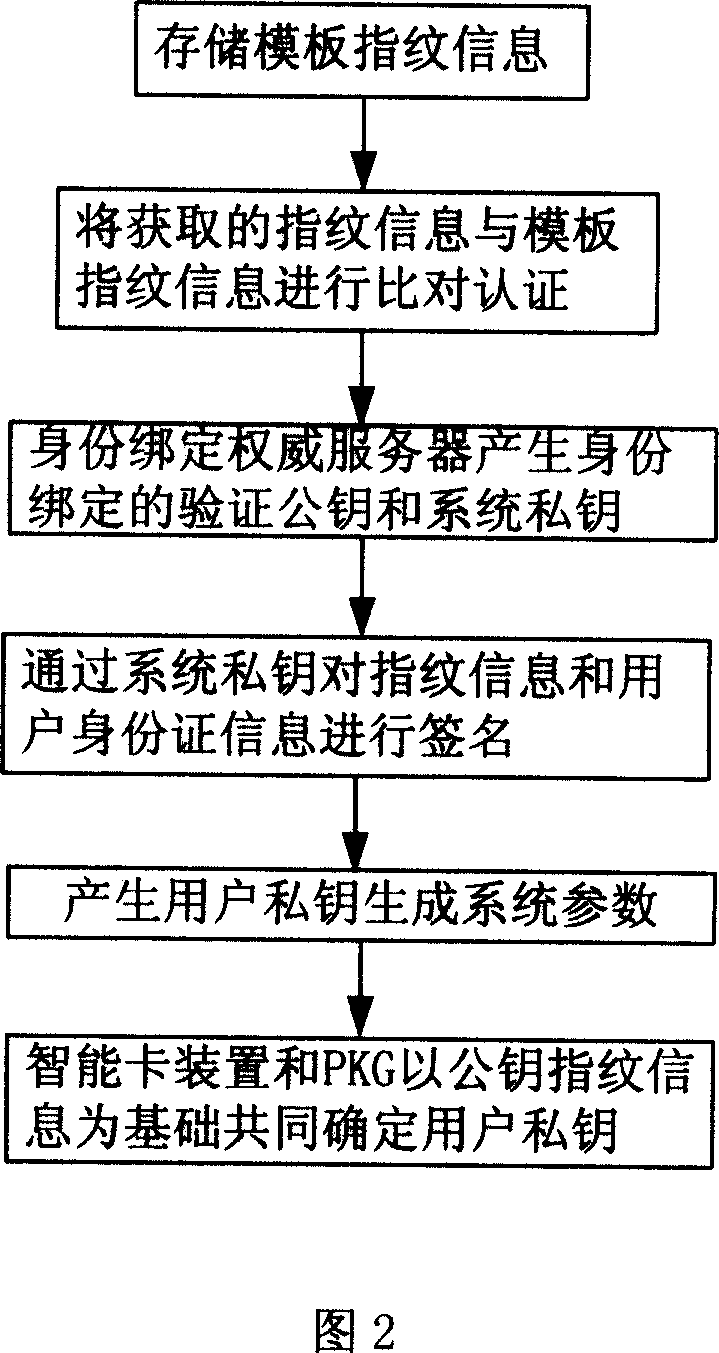
[0116] Embodiment 2: In Embodiment 1, the user's private key is independently generated by the trusted private key generator PKG, so there is a private key custody problem. To solve this problem, as shown in Figure 2, the method of this embodiment uses a smart card The device and the non-trusted private key generation device PKG jointly generate the user's private key. The specific steps are as follows:
[0117] After following the same steps as steps 101-103,
[0118] Step 201: Using a method similar to that in step 103, finally publish the user private key generation system parameter param=1 , G 2 , e, n, p, p pub , H 1 , H 2 >,
[0119] The generated user private key will generate the system parameter param=1 , G 2 , e, n, p, p pub , H 1 , H 2 >Stored in the system public parameter storage area of the smart card so as to be called by subsequent steps.
[0120] Step 202: smart card device and PKG with public key fingerprint information ID U As a basis, jointly de...
Embodiment 3
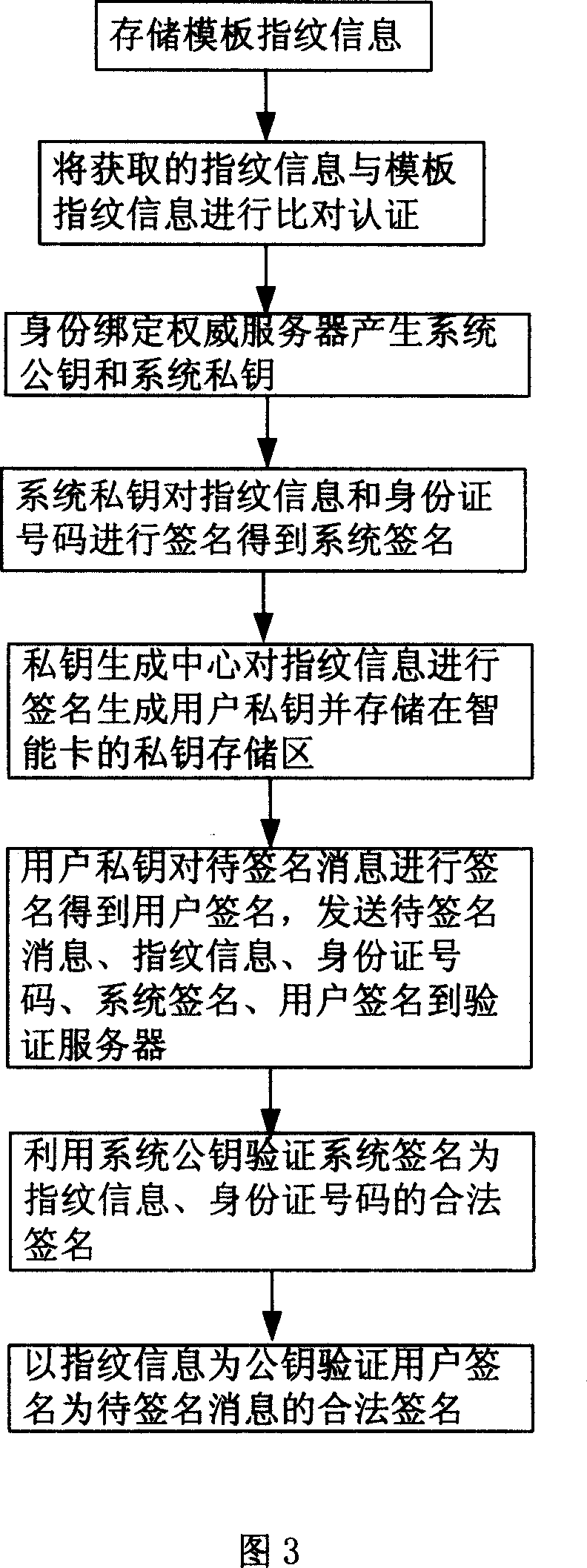
[0127] When the method according to the present invention is applied to securities transactions, further specific instructions will be given below. When users and stock exchanges conduct stock buying and selling transactions through the network, the biometric-based public key infrastructure in embodiment 1 can On the basis of the user’s final signature confirmation of the transaction, that is to say, the signature is implemented on the basis of the fingerprint information as the user’s signature public key. When the user’s securities transaction is signed, the entire transaction system needs to include a private key generation device PKG and The user utilizes the signature device of the biometric signature, such as a smart card device, and also includes a verification server of the stock exchange, as shown in Figure 3, the specific steps of the method of this embodiment are as follows:
[0128] Using the same steps as steps 101-104, after that,
[0129] Step 301: The user invo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com