Authentication method based on the end-to-end communication of the mobile network
An authentication method and mobile network technology, applied in the field of authentication based on mobile network end-to-end communication, can solve the problems of unsuccessful mutual authentication, non-compliance with business security requirements, and lack of detailed regulations, and achieve increased flexibility and versatility. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0099] The present invention is further described below with reference to the accompanying drawings and embodiments, but is not intended to limit the present invention.
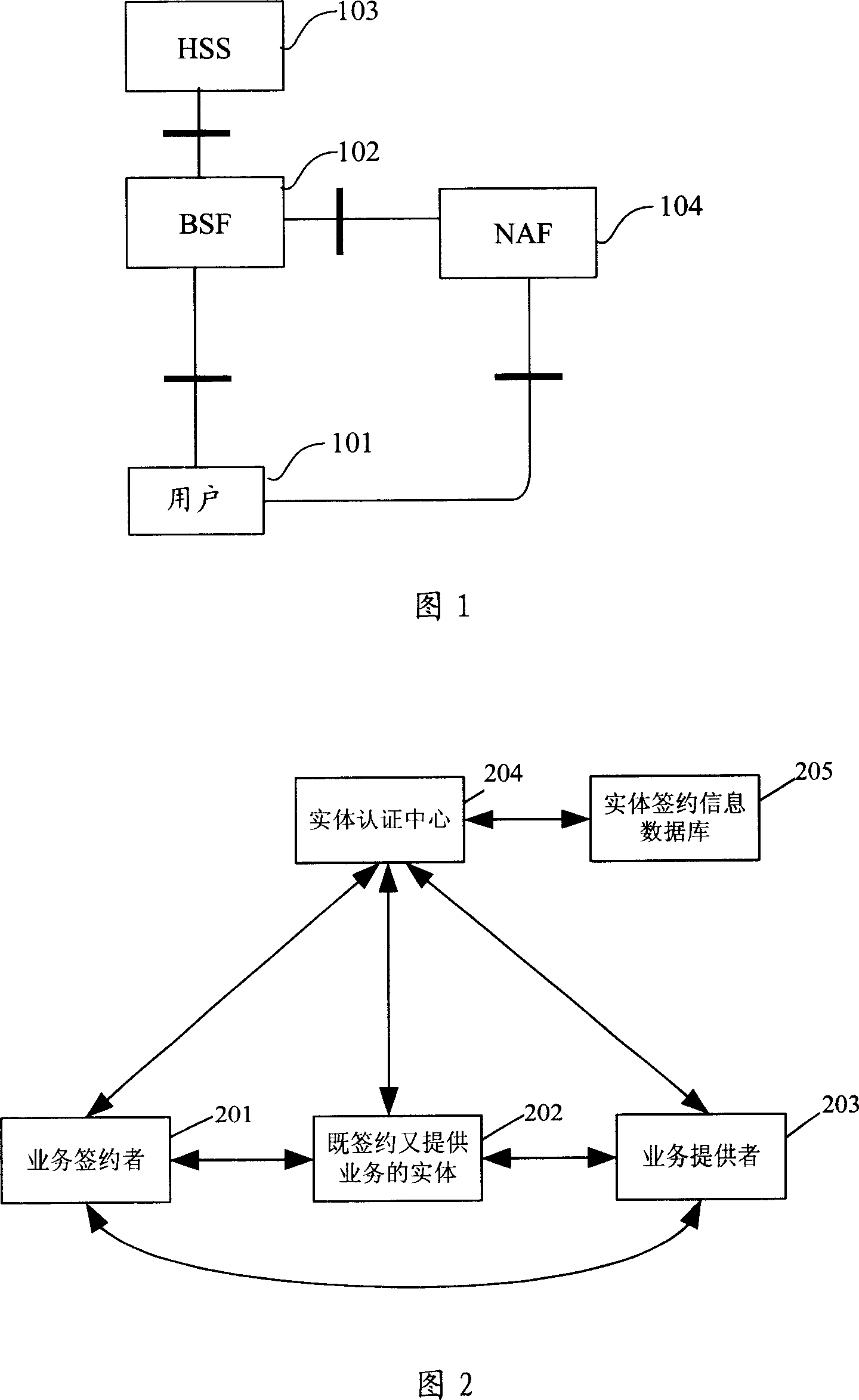
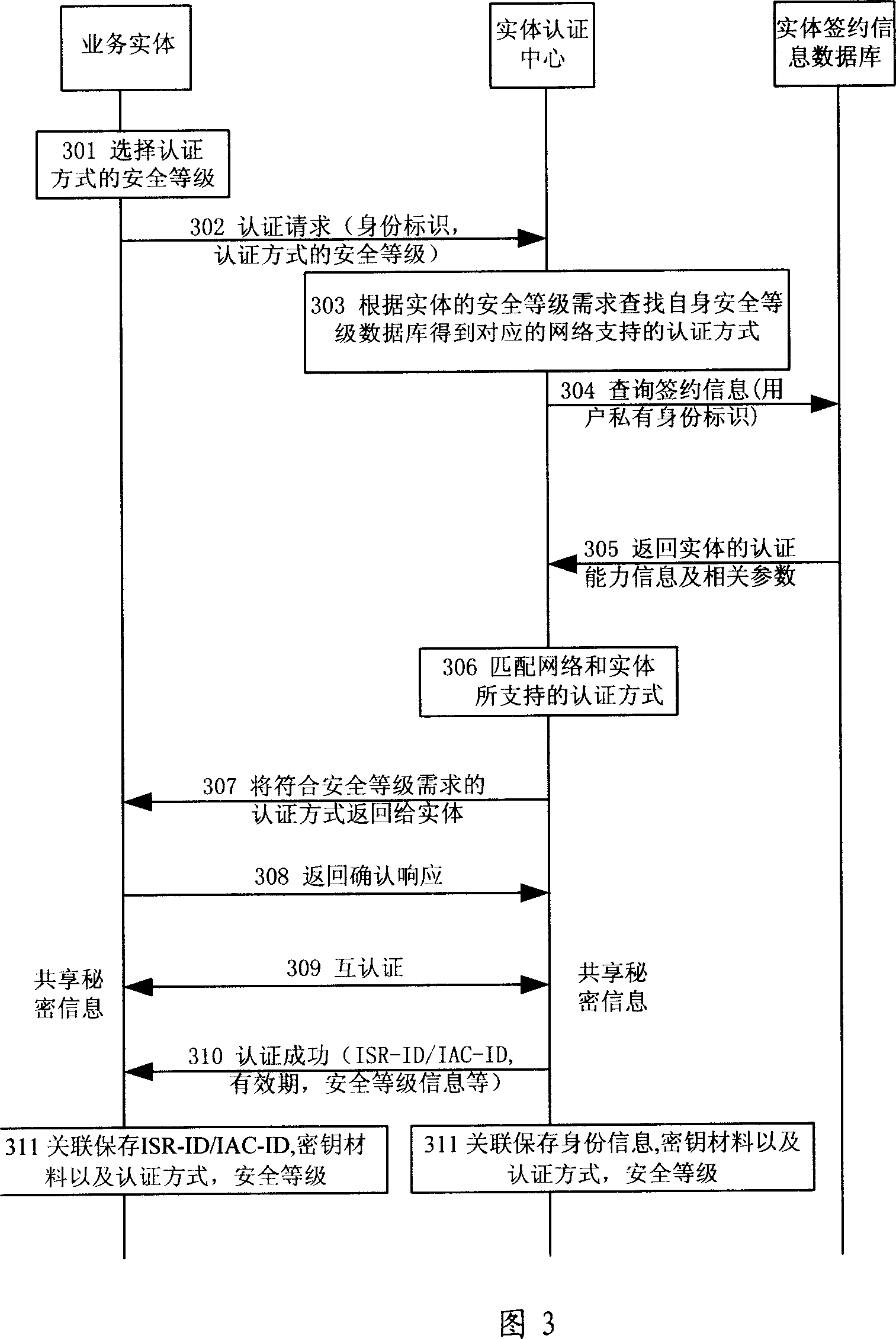
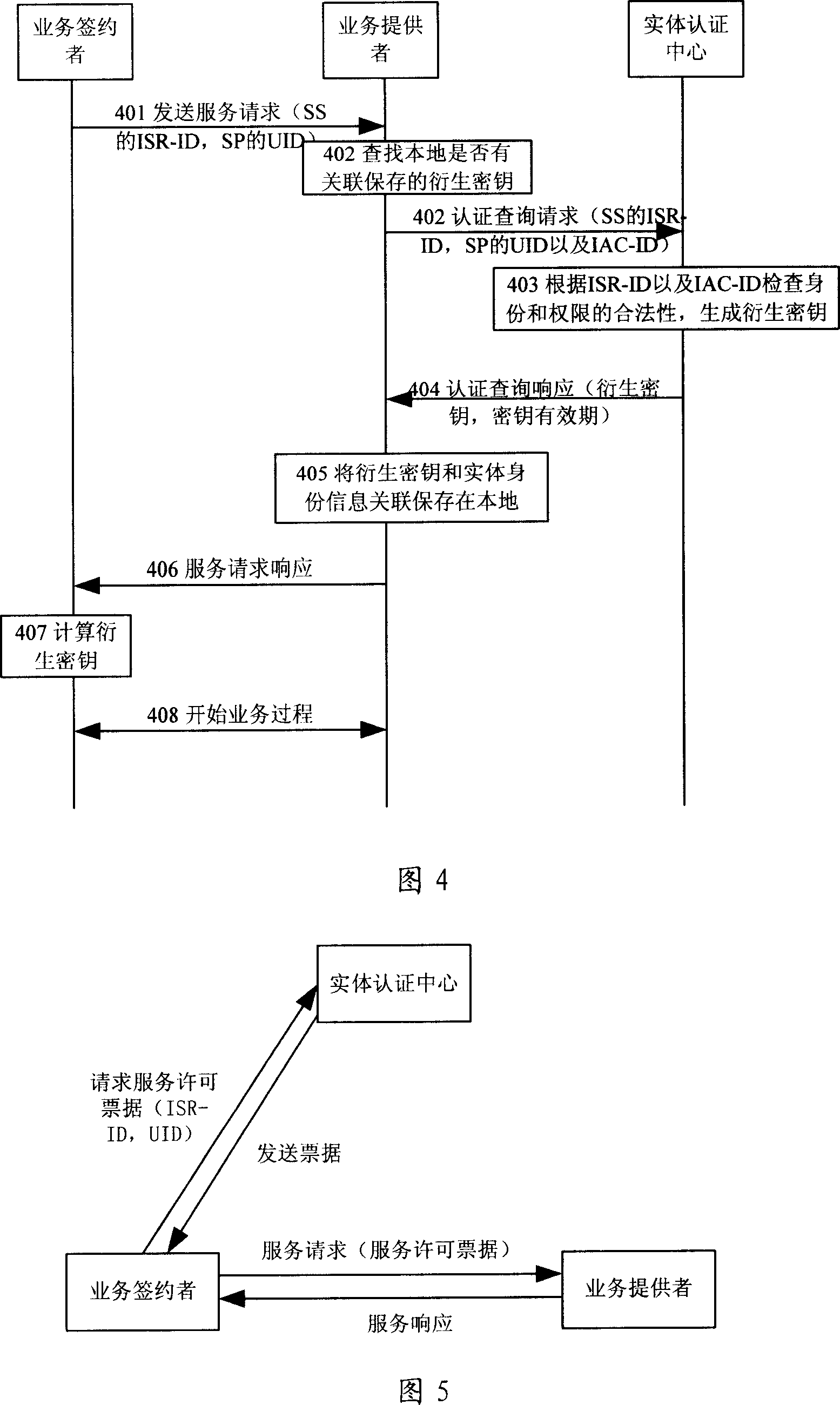
[0100] Figure 2 shows the mobile network-based end-to-end communication authentication framework according to the present invention. This framework is suitable for different mobile network standards, and its function is to establish mutual trust between different types of business entities, and it is a real general authentication framework. The network elements involved are in addition to three types of service entities: Service Subscriber (SS) 201 , Service Subscriber and Provider (SSP) 202 , Service Provider (SP) 203 Besides, in the operator's network, there are also an entity authentication center (Entity Authentication Center, EAC) 204 and an entity subscription information database (Entity Subscription Database, ESD) 205 .
[0101] When most application servers provide a certain service to mobile users,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com