AK context cache method for wireless communication system
A wireless communication system and context technology, applied in the field of wireless communication, can solve the problems of severe space, equipment environment, poor BS equipment room conditions, no re-authentication, etc., to avoid replay attacks, improve efficiency, and improve performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
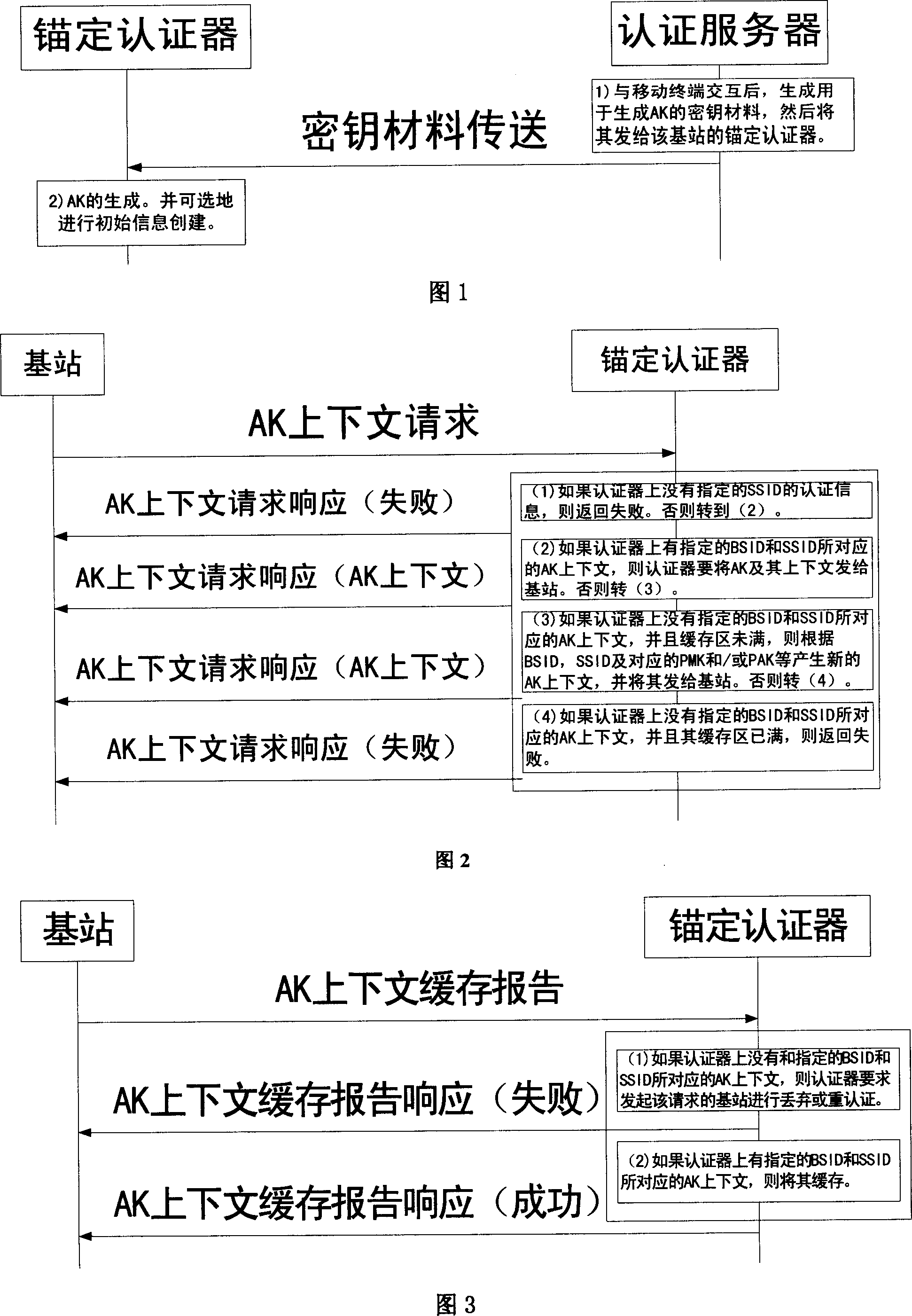
[0060] A method for AK context caching in a wireless communication system. In an authentication period, both the mobile terminal and the authenticator create and store the AK context generated between the mobile terminal and the base station that it passes through. When the mobile terminal returns to a certain When a passing base station, the AK context is reused. The stored AK context content includes BSID, MSID, uplink message prevention replay attack packet sequence number, downlink message prevention replay attack packet sequence number, and Including AK and AKID.
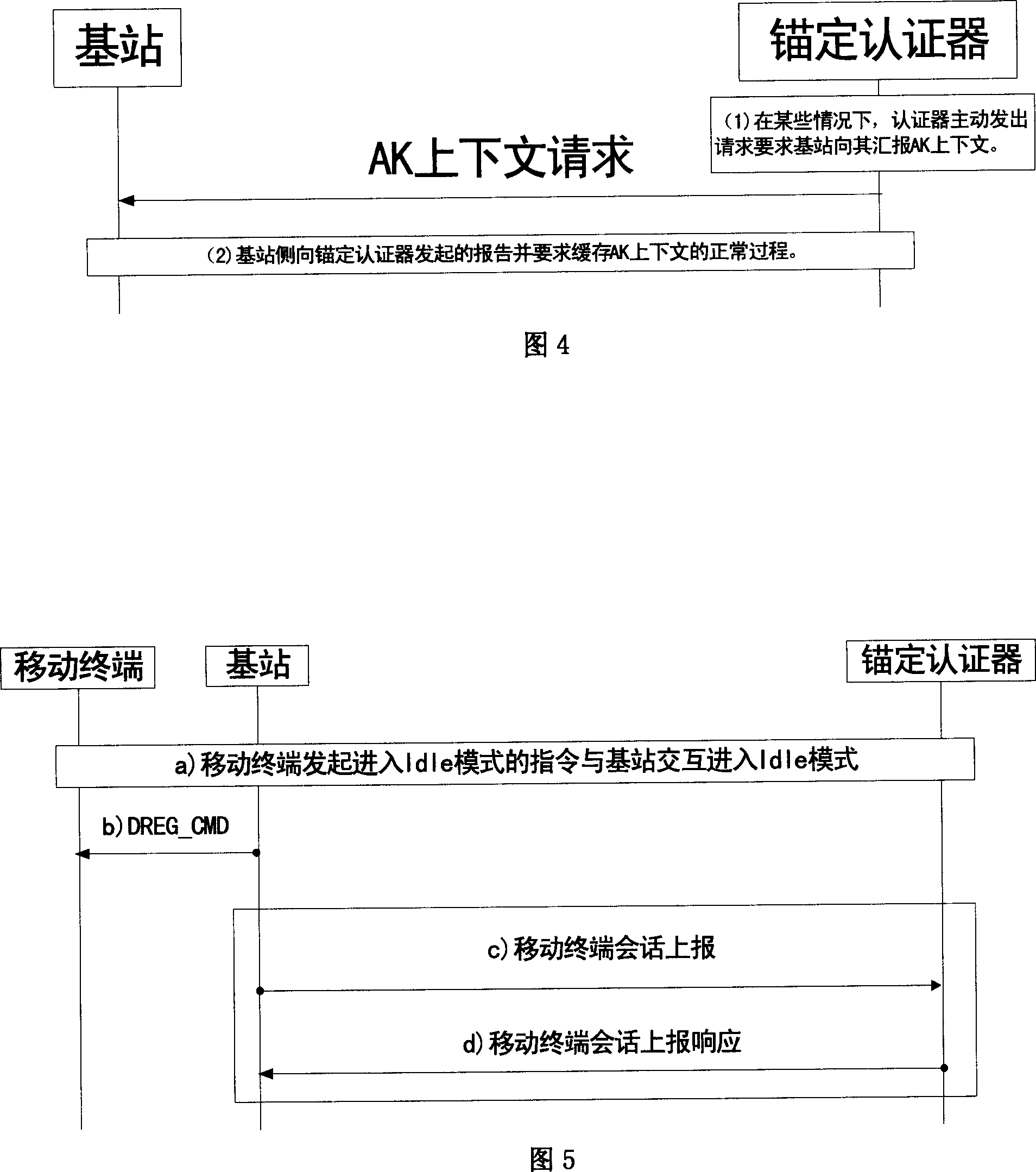
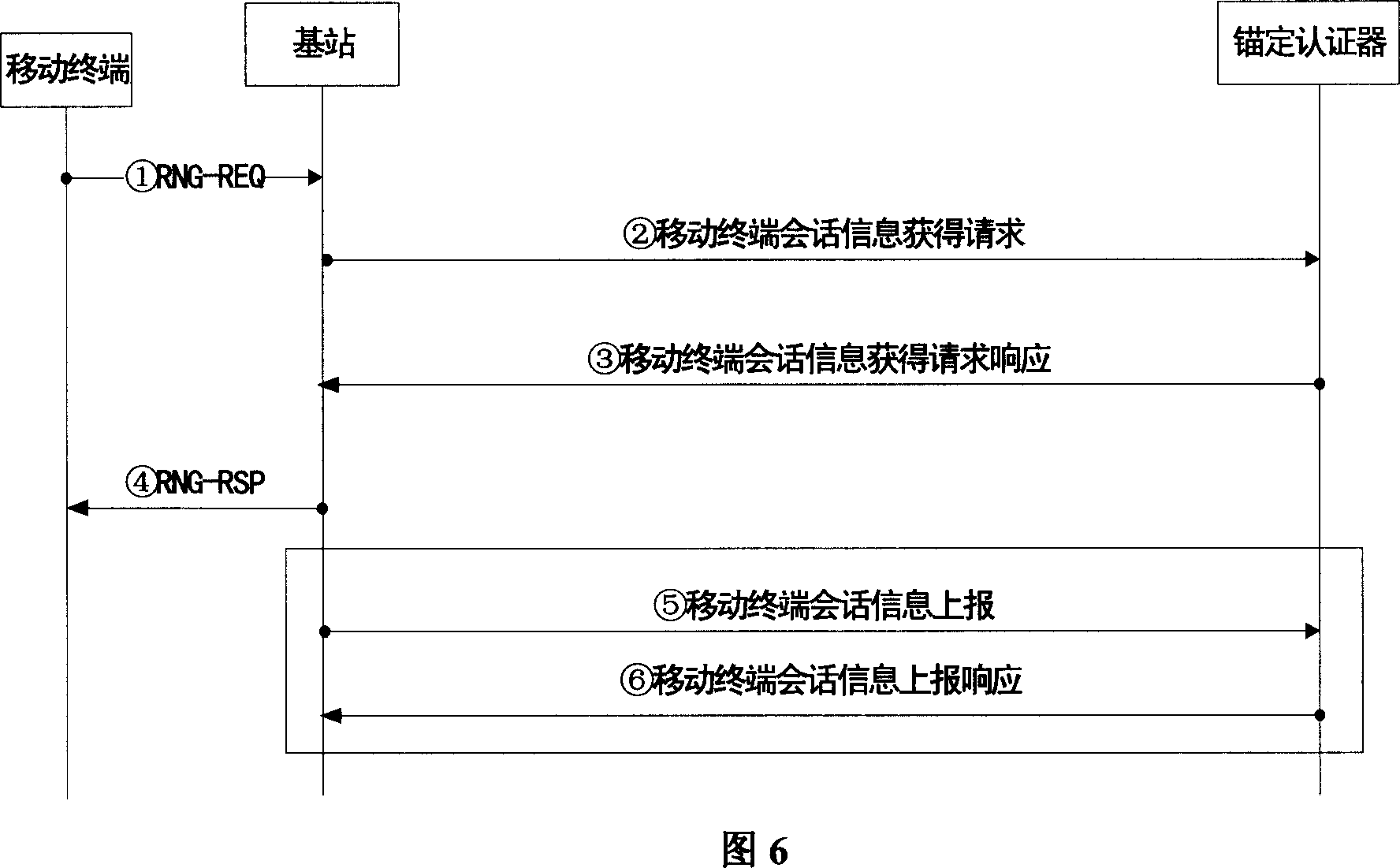
[0061] In the communication process, the possible situations and the corresponding AK context caching methods are described as follows:
[0062] 1) AK cache on the authenticator side during the initial authentication or re-authentication of the mobile terminal
[0063] As shown in Figure 1, during the initial authentication or re-authentication of the mobile terminal, when the authenticator receives the key materia...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com