User authentication method
A user authentication and user terminal technology, applied in the field of user authentication, can solve the problems of reducing user satisfaction, low security, and the authentication method cannot support future services, and achieves the effect of improving user satisfaction and security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
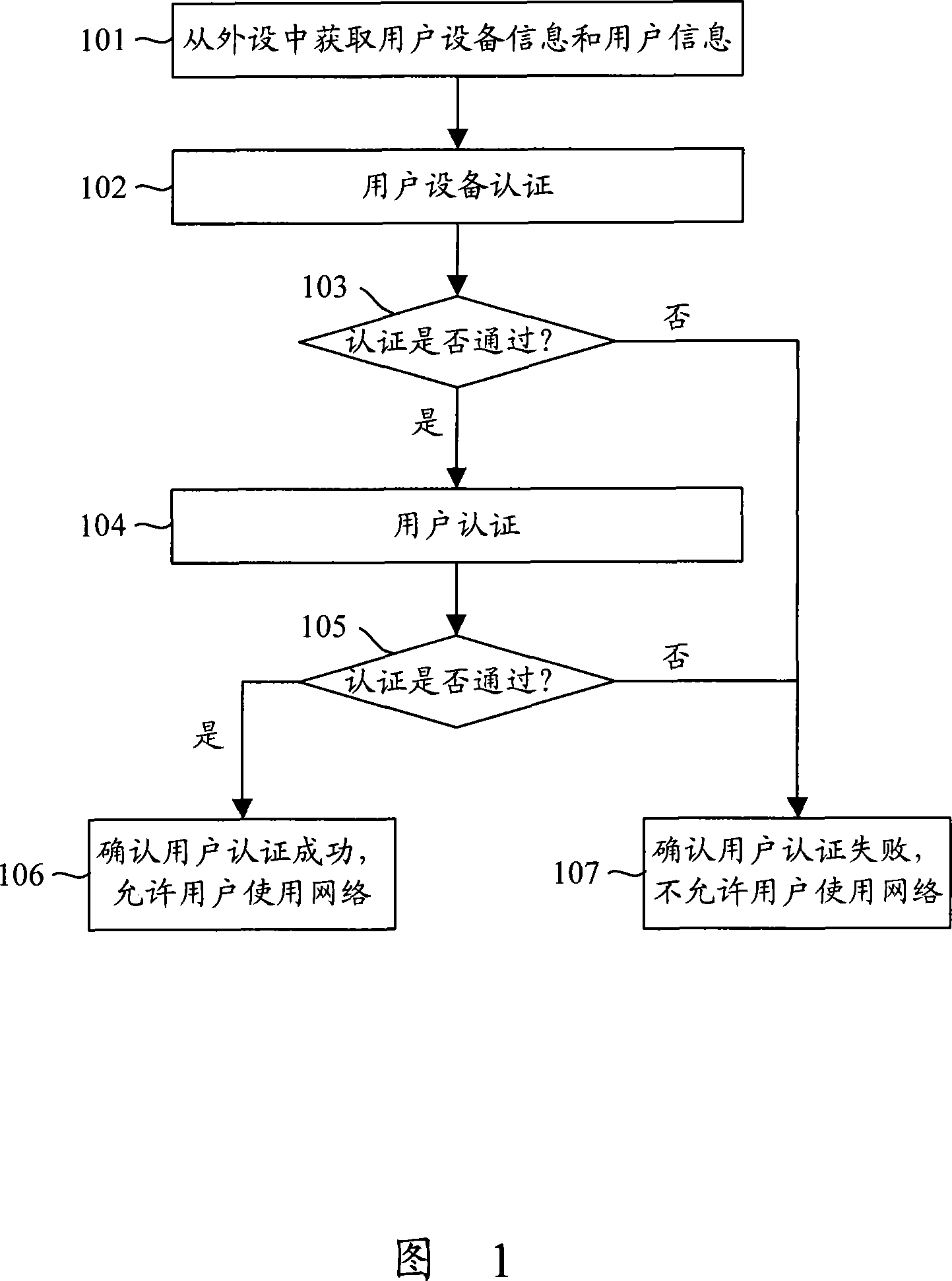
[0029] The technology of the present invention will be described in detail below in conjunction with the accompanying drawings.
[0030] Referring to Fig. 1, Fig. 1 is a flow chart of user authentication in an embodiment of the present invention, and the flow includes the following steps:
[0031] Step 101: Obtain user terminal information and user information from peripheral devices.
[0032] In order to realize the operation of this step, it is necessary to add the circuit design of the memory card reader to the printed circuit board (PCB) circuit of the user terminal, and connect the read and write pins of the memory card reader to the central processing unit of the user terminal. unit (CPU); in this way, when a peripheral device is inserted into the memory card reader-writer on the user terminal, the memory card reader-writer can read the information in the peripheral device from the peripheral device and convert the read information Send it to the CPU of the user termina...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com