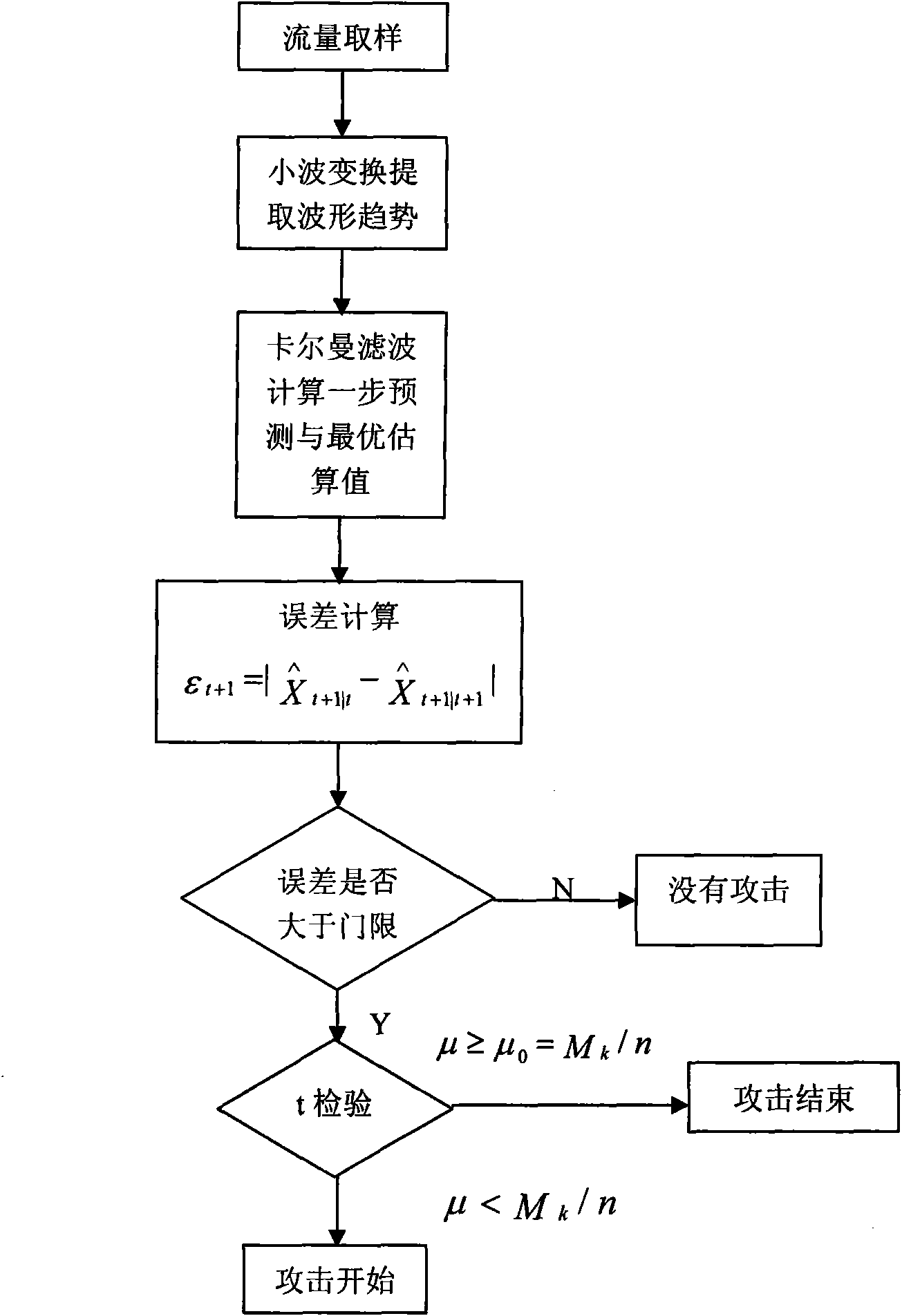
Method for one-step forecasting Kalman filtering detection of LDoS attack
A Kalman filtering and detection method technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problem of insufficient detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
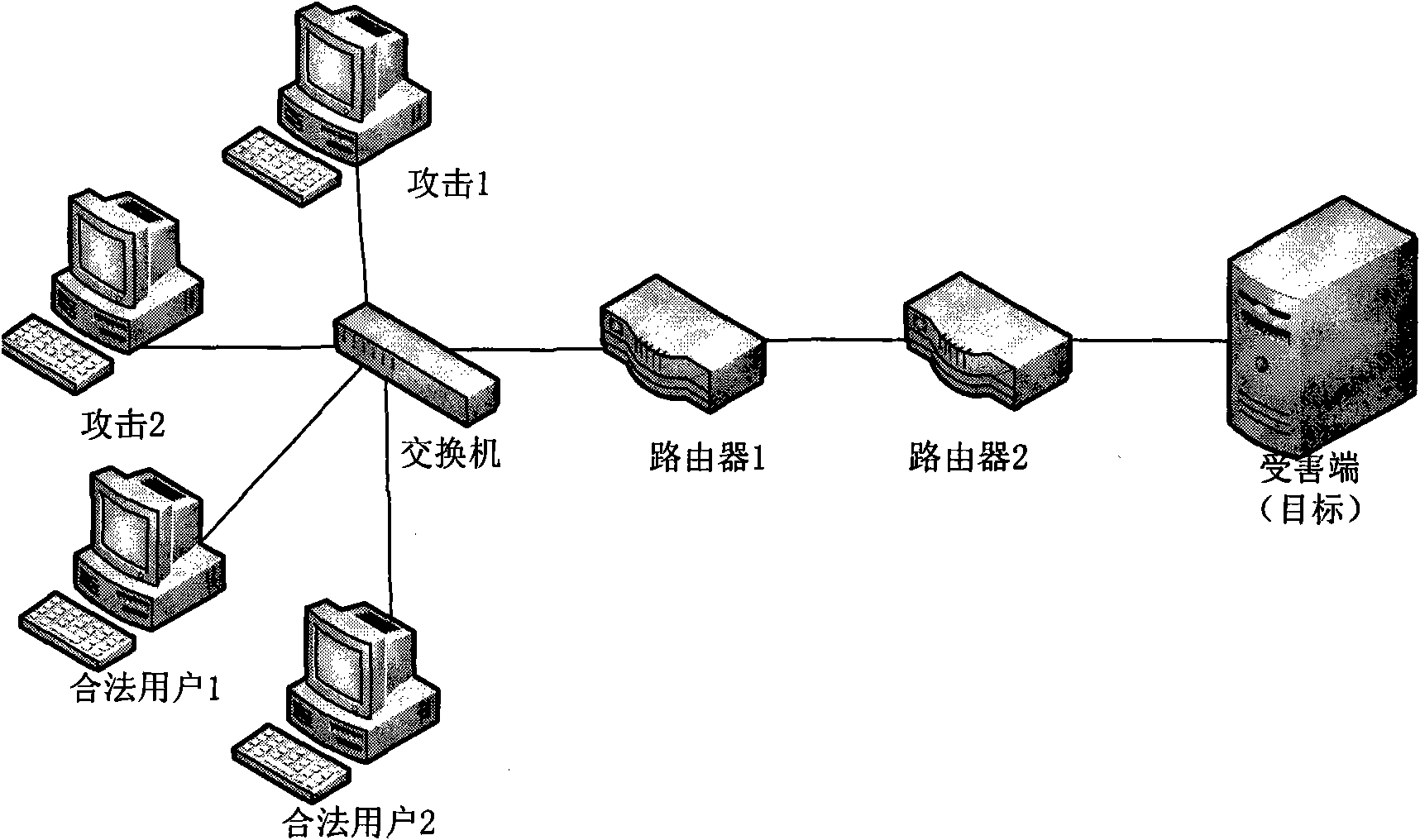
[0038] 1. in figure 2 In the simulated LDoS scenario, the router is Cisco2621, and the bottleneck bandwidth between routers is 10Mbps. Other equipment configurations are shown in the table below:
[0039] machinary code
Attacker1
192.168.20.23
Red Hat 9.0
Attacker2
192.168.20.24
Red Hat 9.0
legitimate user 1
192.168.20.25
Windows 2000
legitimate user 2
192.168.20.26
Windows 2000
Victim
192.168.40.8
Red Hat 9.0
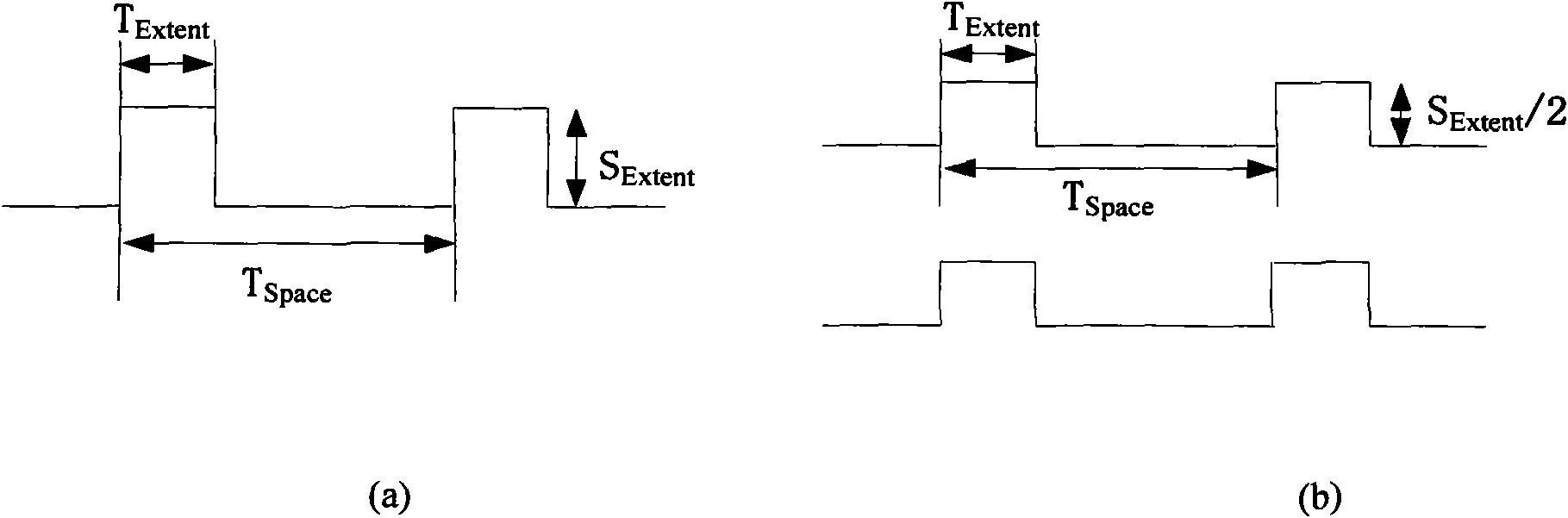
[0040] Let the legitimate user establish an FTP connection with the victim (Victim) server normally, monitor the traffic changes on the user end and the server end, wait for 180s after the flow is stable, and the Attacker launches an LDoS-based attack, and the duration of each attack is 540s, and then let the legitimate user The user normally downloads 180s, and so on. Reasonably set the parameter A (200ms, 5Mbps, 1s, 540) of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com